This is “Property Risk Management”, chapter 11 from the book Enterprise and Individual Risk Management (v. 1.0). For details on it (including licensing), click here.
For more information on the source of this book, or why it is available for free, please see the project's home page. You can browse or download additional books there. To download a .zip file containing this book to use offline, simply click here.
Chapter 11 Property Risk Management
At this point you should feel somewhat comfortable with most of the overall picture of risk, but despite the many examples of risk management and types of coverage you have seen, the details of each coverage are not explicit yet. In this chapter, we will elaborate on property risks, including electronic commerce, or e-commerce, risk and global risk exposures. In Chapter 12 "The Liability Risk Management", we will elaborate on liability risks overall and the particulars of e-commerce liability. Home coverage that includes both property and liability coverage will be discussed in detail in Chapter 1 "The Nature of Risk: Losses and Opportunities". Auto coverage will be discussed in Chapter 1 "The Nature of Risk: Losses and Opportunities". Chapter 13 "Multirisk Management Contracts: Homeowners" and Chapter 14 "Multirisk Management Contracts: Auto" focus on personal lines coverage. Chapter 15 "Multirisk Management Contracts: Business" and Chapter 16 "Risks Related to the Job: Workers’ Compensation and Unemployment Compensation" take us into the world of commercial lines coverage and workers’ compensation. In this part of the text, you will be asked to relate sections of the actual policies provided in the appendixes at the end of the textbook to loss events. Our work will clarify many areas of property and liability of various risks, including the most recent e-commerce risk exposures and the fundamental global risk exposure. In this chapter, we cover the following:
- Links
- Property risks
- E-commerce property risks
- Global risks
Links
The most important part of property coverage is that you, as the first party, are eligible to receive benefits in the event you or your business suffers a loss. In contrast, liability coverage, discussed in Chapter 12 "The Liability Risk Management", pays benefits to a third party if you cause a loss (or if someone causes you to have a loss, his or her liability insurance would pay benefits to you). In this chapter we focus on the first type: coverage for you when your property is damaged or lost.
In personal lines coverage such as homeowners and auto policies, the property coverage for losses you sustain, as the owner of the property, is only part of the policies. In commercial lines, you may use a packaged multilines policy that includes both commercial property and commercial general liability policies. In this chapter we focus only on the part of the policies relating to the property coverage for first-party damages to you. As part of your holistic risk and risk management, it is important to have an appreciation of this part of the coverage.
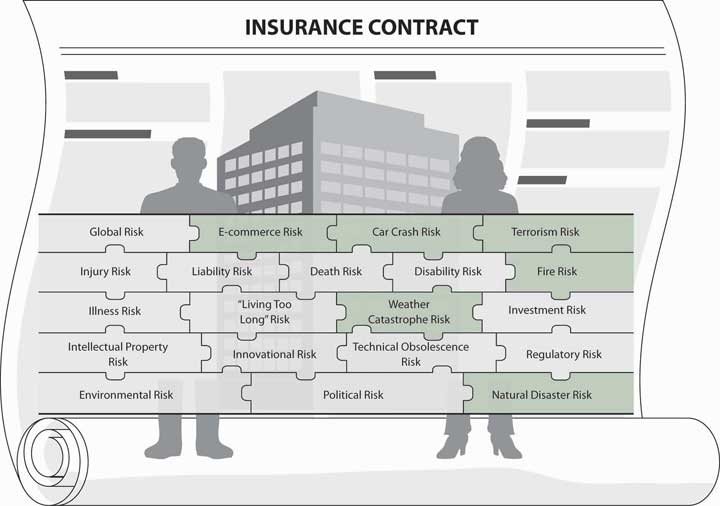
As we develop the holistic risk management program, you now realize that you need a myriad of policies to cover all your property exposures, including that of e-commerce, and another myriad of policies to protect your liability exposures. In some cases, property and liability coverages are packaged together, such as in homeowners and auto policies, but what is actually covered under each? Our objective is to untangle it all and show how to achieve a complete risk management picture. To achieve complete holistic risk management, we have to put together a hierarchy of coverages for various exposures, perils, and hazards—each may appear in one or another policy—as shown in Figure 11.1 "Links between Property Risks and Insurance Contracts" (see the shaded risk pieces of the puzzle that indicate property or first-party-type risks applicable to this chapter). In addition to understanding this hierarchy, we need to have a vision of the future. E-commerce risk, considered one of the emerging risks, is explored in this chapter. Hazards derived from global exposure are other important risks that receive special attention in this chapter.
Figure 11.1 Links between Property Risks and Insurance Contracts
11.1 Property Risks
Learning Objectives
In this section we elaborate on the following:
- How insurable property is classified
- The ways in which valuation, deductibles, and coinsurance clauses influence property coverage and premiums
Property can be classified in a number of ways, including its mobility, use value, and ownership. Sometimes these varying characteristics affect potential losses, which in turn affect decisions about which risk management options work best. A discussion of these classifying characteristics, including consideration of the hot topic of electronic commerce (e-risk) exposures and global property exposures, follows.
Physical propertyConsists of real or personal property. generally is categorized as either real or personal. Real propertyPermanent structures (realty) that if removed would alter the functioning of the property. represents permanent structures (realty) that if removed would alter the functioning of the property. Any building, therefore, is real property. In addition, built-in appliances, fences, and other such items typically are considered real property.
Physical property that is mobile (not permanently attached to something else) is considered personal propertyPhysical property that is mobile (not permanently attached to something else).. Included in this category are motorized vehicles, furniture, business inventory, clothing, and similar items. Thus, a house is real property, while a stereo and a car are personal property. Some property, such as carpeting, is not easily categorized. The risk manager needs to consider the various factors discussed below in determining how best to manage such property.
Why is this distinction between real and personal property relevant? One reason is that dissimilar properties are exposed to perils with dissimilar likelihoods. When flood threatens a house, the opportunities to protect it are limited. Yet the threat of flood damage to something mobile may be thwarted by movement of the item away from flood waters. For example, you may be able to drive your car out of the exposed area and to move your clothes to higher ground.
A second reason to distinguish between real and personal property is that appropriate valuation mechanisms may differ between the two. We will discuss later in this chapter the concepts of actual cash value and replacement cost new. Because of moral hazard issues, an insurer may prefer to value personal property at actual cash value (a depreciated amount). The amount of depreciation on real property, however, may outweigh concerns about moral hazard. Because of the distinction, valuation often varies between personal and real property.
When property is physically damaged or lost, the cost associated with being unable to use that property may go beyond the physical loss. Indirect loss and business interruption losses discussed in the box “Business Interruption with and without Direct Physical Loss” provides a glimpse into the impact of this coverage on businesses and the importance of the appropriate wording in the policies. In many cases, only loss of use of property that is directly damaged leads to coverage; in other cases, the loss of property itself is not a prerequisite to trigger loss of use coverage. As a student in this field, you will become aware of the importance of the exact meaning of the words in the insurance policy.
General Property Coverage
The first standard fire policy (SFP)The generally accepted method of insuring against property loss due to fire until being replaced by homeowners policies and commercial insurance options. came into effect during the late 1800s and came to be described as the generally accepted manner of underwriting for property loss due to fire. Two revisions of the SFP were made in 1918 and 1943. Most recently, the SFP has largely been removed from circulation, replaced by homeowners policies for residential property owners, discussed in Chapter 1 "The Nature of Risk: Losses and Opportunities", and the commercial package policy (CPP), featured in Chapter 1 "The Nature of Risk: Losses and Opportunities". The SFP was simple and relatively clear. Most of its original provisions are still found in current policies, updated for the needs of today’s insured. In light of the changes regarding terrorism exclusion that occurred after September 11, 2001 (discussed in Chapter 1 "The Nature of Risk: Losses and Opportunities"), the topic of standard fire policies came under review. The issue at hand is that, under current laws, standard fire policies cannot exclude fires resulting from terrorism or nuclear attacks without legislative intervention.For more information, read the article “Standard Fire Policy Dates Back to 19th Century,” featured in Best’s Review, April 2002.
Business Interruption with and without Direct Physical Loss
When there is a direct physical loss, insurance coverage for business interruption is more likely to exist than when the interruption is not from direct physical loss. The New Orleans hotels that suffered damage due to flooding and wind caused by Hurricane Katrina on August 30, 2005, are more likely to have had business interruption coverage. The oil industry, including its refineries and rigs that were shut down as both hurricanes Katrina and Rita ripped through the Gulf Coast, also had insurance coverage for business interruption. The stop in oil production was associated with a physical loss. Not all business interruptions are covered by insurance. The economic losses suffered by many New York businesses during the New York City transportation strike of December 2005 were not a direct loss from physical damage. As such, these businesses did not have insurance to cover the losses. Nonrelated causes of loss that affect the continued viability of businesses usually do not have insurance remedies. The avian flu pandemic is expected to disrupt many businesses’ activities indirectly. Employees are expected to be afraid to show up for work, and some industries—such as shipping—will be vulnerable. A key problem in these cases would be lack of insurance coverage.
In the past, some policyholders submitted business-interruption claims for nondirect economic loss. They were not successful in court. A case in point is the lawsuit filed in August 2002 by the luxury hotel chain Wyndham International against half a dozen of its insurers and the brokerage firm Marsh & McLennan. Wyndham claimed that it had suffered $44 million in lost revenue following the terrorist acts of September 11, 2001, and that the insurers had acted in bad faith in failing to pay the corporation’s business-interruption claims. The Wyndham properties that reported September 11-related losses included hotels in Chicago and Philadelphia and three Puerto Rico beach resorts. Wyndham owns no properties in downtown New York City.
September 11 was the wake-up call. It’s estimated that some $10 billion in claims have been filed for business-interruption losses, much of them far away from Ground Zero. With the Federal Aviation Administration—ordered closing of airports nationwide, the travel industry bore major losses. Resort hotels like Wyndham’s saw business fall dramatically.
Are losses recoverable if the business sustained no physical damage? It depends, of course, on the policy. Most small and midsize businesses have commercial policies based on standard forms developed by the Insurance Services Office (ISO). The ISO’s customary phrase is that the suspension of business to which the income loss relates must be caused by “direct physical loss of or damage to property at the premises described in the Declarations.” Larger companies often have custom-written manuscript policies that may not be so restrictive. Whatever the wording is, it is likely to be debated in court.
Sources: Michael Bradford, “Hotels Start Recovery Efforts in Wake of Katrina Losses” Business Insurance, October 10, 2005, accessed March 15, 2009, http://www.businessinsurance.com/cgi-bin/article.pl?articleId=17714&a=a&bt=Hotels+Start+Recovery+Efforts; Michael Bradford, “Storms Slap Energy Sector with Losses as High as $8 Billion,” Business Insurance, October 3, 2005, accessed March 15, 2009, http://www.businessinsurance.com/cgi-bin/article.pl?articleId=17640&a=a&bt=storms+slap+energy; Daniel Hays, “No Coverage Likely for N.Y. Transit Strike,” National Underwriter Online News Service, December 20, 2005, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2005/12/20-STRIKE-dh?searchfor=transit%20strike; Mark E. Ruquet, “Business Policies May Not Cover Pandemics,” National Underwriter Online News Service, December 7, 2005, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2005/12/07-PANDEMIC-mr?searchfor= policies%20may%20not%20cover%20pandemics; Mark Ruquet, “Avian Flu Could Send Shipping Off Course,” National Underwriter Online News Service, December 12,2005, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2005/12/12-AVIAN-AON-mr?searchfor=avian%20flu; Sam Friedman, “9/11 Boosts Focus on Interruption Risks,” National Underwriter, Property & Casualty/Risk & Benefits Management Edition, April 29, 2002; Joseph B. Treaster, “Insurers Reluctant to Pay Claims Far Afield from Ground Zero,” New York Times, September 12, 2002; John Foster, “The Legal Aftermath of September 11: Handling Attrition and Cancellation in Uncertain Times,” Convene, the Journal of the Professional Convention Management Association, December 2001; Daniel Hays, “Zurich Loses Ruling in a 9/11 Case,” National Underwriter Online News Service, February 11, 2005, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2005/02/11-Zurich%20Loses%20Ruling%20In%20A%209-11%20Case?searchfor=.
From Coast to Coast: Who Is Responsible for Earthquake and Flood Losses?
No region of the United States is safe from environmental catastrophes. Floods and flash floods, the most common of all natural disasters, occur in every state. The Midwest’s designated Tornado Alley ranges from Texas to the Dakotas, though twisters feel free to land just about anywhere. The Pacific Rim states of Hawaii, Alaska, Washington, Oregon, and California are hosts to volcanic activity, most famously the May 1980 eruption of Mount St. Helens in southwestern Washington, which took the lives of more than fifty-eight people. California is also home to the San Andreas Fault, whose seismic movements have caused nine major earthquakes in the past one hundred years; the January 1994 Northridge quake was the most costly in U.S. history, causing an estimated $20 billion in total property damage. (By comparison, the famous San Francisco earthquake of 1906 caused direct losses of $24 million, which would be about $10 billion in today’s dollars.) Along the Gulf and Atlantic coasts, natural disaster means hurricanes. Insurers paid out more money for Hurricane Katrina in 2005 than they collected in premiums in twenty-five years from Louisiana insureds. California insurers paid out more in Northridge claims than they had collected in earthquake premiums over the previous thirty years. The year 2005 saw an unprecedented number of losses because of hurricanes Katrina, Rita, and Wilma. The record number of hurricanes included twenty-seven named storms. The insured losses from Hurricane Katrina alone were estimated between $40 and $60 billion, while the economic losses were estimated to be more than $100 billion. Theses losses are the largest catastrophic losses in U.S. history, surpassing Hurricane Andrew’s record cost to the industry of $20.9 billion in 2004 dollars. This record also surpasses the worst human-made catastrophe of September 11, 2001, which stands at $34.7 billion in losses in 2004 dollars.
Fearing that the suffering housing, construction, and related industries would impair economic growth, state government stepped in. The state-run California Earthquake Authority was established in 1996 to provide coverage to residential property owners in high-risk areas. Disaster insurance then went to the federal level. In the aftermath of Katrina, in December 2005, a proposal for a national catastrophe insurance program was pushed by four big state regulators during the National Insurance Commissioners meeting in Chicago. The idea was to change the exclusion in the policies and allow for flood coverage, while calling for a private-state-federal partnership to fund megacatastrophe losses and the creation of a new all-perils homeowners policy that would cover the cost of flood losses.
Questions for Discussion
- Lee is in favor of government-supported disaster reinsurance because it encourages economic growth and development. Chris believes that it encourages overgrowth and overdevelopment in environmentally fragile areas. Whose argument do you support?
- The Gulf Coast town you live in has passed a building code requiring that new beachfront property be built on stilts. If your house is destroyed by a hurricane, rebuilding it on stilts will cost an extra $25,000. The standard homeowners policy excludes costs caused by ordinance or laws regulating the construction of buildings. Is this fair? Who should pay the extra expense?
- Jupiter Island, located off the coast of south Florida, is the wealthiest town in the country. Its 620 year-round residents earn an average of just over $200,000 per year, per person. Thus, a typical household of two adults, two children, a housekeeper, a gardener/chauffeur, and a cook boasts an annual income of some $1.4 million. What is the reasoning for subsidizing hurricane insurance for residents of Jupiter Island?
- In light of your understanding of the uninsurable nature of catastrophes, who should bear the financial burden of natural disasters?
Sources: Insurance Information Institute at http://www.III.org; Steve Tuckey, “A National Cat Program? Insurers Have Doubts,” National Underwriter Online News Service, December 5, 2005, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2005/12/05-CAT-st?searchfor=national%20cat%20program; Mark E. Ruquet, “Towers Perrin: Katrina Loss $55 Billion,” National Underwriter Online News Service, October 6, 2005, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2005/10/06-TOWERSP-mr?searchfor =towers%20perrin%20katrina; “Louisiana Hurricane Loss Cancels 25 Years of Premiums,” National Underwriter, January 6, 2006, accessed March 15, 2009, http://www.propertyandcasualtyinsurancenews.com/cms/NUPC/Breaking%20News/2006/01/06-LAIII-ss?searchfor=louisiana%20hurricane; Insurance Information Institute, “Earthquakes: Risk and Insurance Issues,” May 2002, http://www.iii.org/media/hottopics/insurance/earthquake/; Jim Freer, “State to Help Those Seeking Property, Casualty Insurance,” The South Florida Business Journal, March 15, 2002.
Types of Property Coverage and Determination of Payments
Once it is determined that a covered peril has caused a covered loss to covered property, several other policy provisions are invoked to calculate the covered amount of compensation. As noted earlier, the topic of covered perils is very important. Catastrophes such as earthquakes are not considered covered perils for private insurance, but in many cases catastrophes such as hurricanes and other weather-related catastrophes are covered. The box Note 11.7 "From Coast to Coast: Who Is Responsible for Earthquake and Flood Losses?" is designed to stimulate discussions about the payment of losses caused by catastrophes. Important provisions in this calculation are the valuation clause, deductibles, and coinsurance.
Valuation Clause
The intent of insurance is to indemnify an insured. Payment on an actual cash value basis is most consistent with the indemnity principle, as discussed in Chapter 9 "Fundamental Doctrines Affecting Insurance Contracts". Yet the deduction of depreciation can be both severe and misunderstood. In response, property insurers often offer coverage on a replacement cost new (RCN) basis, which does not deduct depreciation in valuing the loss. Rather, replacement costIndemnification for a property loss with no deduction for depreciation. new is the value of the lost or destroyed property if it were bought new or rebuilt on the day of the loss.
Deductibles
The cost of insurance to cover frequent losses (as experienced by many property exposures) is high. To alleviate the financial strain of frequent small losses, many insurance policies include a deductible. A deductible requires the insured to bear some portion of a loss before the insurer is obligated to make any payment. The purpose of deductibles is to reduce costs for the insurer, thus making lower premiums possible. The insurer saves in three ways. First, the insurer is not responsible for the entire loss. Second, because most losses are small, the number of claims for loss payment is reduced, thereby reducing the claims processing costs. Third, the moral and morale hazards are lessened because there is greater incentive to prevent loss when the insured bears part of the burden.For example, residents of a housing development had full coverage for windstorm losses (that is, no deductible). Their storm doors did not latch properly, so wind damage to such doors was common. The insurer paid an average of $100 for each loss. After doing so for about six months, it added a $50 deductible to the policies as they were renewed. Storm door losses declined markedly when insureds were required to pay for the first $50 of each loss.
The small, frequent losses associated with property exposures are good candidates for deductibles because their frequency minimizes risk (the occurrence of a small loss is nearly certain) and their small magnitude makes retention affordable. The most common forms of deductibles in property insurance are the following:
- Straight deductible
- Franchise deductible
- Disappearing deductible
A straight deductibleOne that requires payment for all losses less than a specified dollar amount. requires payment for all losses less than a specified dollar amount. For example, if you have a $200 deductible on the collision coverage part of your auto policy, you pay the total amount of any loss that does not exceed $200. In addition, you pay $200 of every loss in excess of that amount. If you have a loss of $800, therefore, you pay $200 and the insurer pays $600.
A franchise deductibleOne that pays the entire amount in full once the amount of loss equals the deductible. is similar to a straight deductible, except that once the amount of loss equals the deductible, the entire loss is paid in full. This type of deductible is common in ocean marine cargo insurance, although it is stated as a percentage of the value insured rather than a dollar amount. The franchise deductible is also used in crop hail insurance, which provides that losses less than, for example, 5 percent of the crop are not paid, but when a loss exceeds that percentage, the entire loss is paid.
The major disadvantage with the franchise deductible from the insurer’s point of view is that the insured is encouraged to inflate a claim that falls just short of the amount of the deductible. If the claims adjuster says that your crop loss is 4 percent, you may argue long and hard to get the estimate up to 5 percent. Because it invites moral hazard, a franchise deductible is appropriate only when the insured is unable to influence or control the amount of loss, such as in ocean marine cargo insurance.
The disappearing deductible is a modification of the franchise deductible. Instead of having one cut-off point beyond which losses are paid in full, a disappearing deductibleOne whose amount decreases as the amount of the loss increases. is a deductible whose amount decreases as the amount of the loss increases. For example, let’s say that the deductible is $500 to begin with; as the loss increases, the deductible amount decreases. This is illustrated in Table 11.1 "How the Disappearing Deductible Disappears".
Table 11.1 How the Disappearing Deductible Disappears
| Amount of Loss ($) | Loss Payment ($) | Deductible ($) |
|---|---|---|
| 500.00 | 0.00 | 500.00 |
| 1,000.00 | 555.00 | 445.00 |
| 2,000.00 | 1,665.00 | 335.00 |
| 4,000.00 | 3,885.00 | 115.00 |
| 5,000.00 | 4,955.00 | 5.00 |
| 5,045.00 | 5,045.00 | 0.00 |
| 6,000.00 | 6,000.00 | 0.00 |
At one time, homeowners policies had a disappearing deductible. Unfortunately, it took only a few years for insureds to learn enough about its operation to recognize the benefit of inflating claims. As a result, it was replaced by the straight deductible.
The small, frequent nature of most direct property losses makes deductibles particularly important. Deductibles help maintain reasonable premiums because they eliminate administrative expenses of the low-value, common losses. In addition, the nature of property losses causes the cost of property insurance per dollar of coverage to decline with the increasing percentage of coverage on the property. That is, the first 10 percent value of the property insurance is more expensive than the second (and so on) percent value. The cost of property insurance follows this pattern because most property losses are small, and so the expected loss does not increase in the same proportion as the increased percentage of the property value insured.
Coinsurance
A coinsurance clauseClause that requires one to carry an amount of insurance equal to a specified percentage of the value of property in order to be paid the full amount of loss incurred and that stipulates a proportional payment of loss for failure to carry sufficient insurance. has two main provisions: first, it requires you to carry an amount of insurance equal to a specified percentage of the value of the property if you wish to be paid the amount of loss you incur in full, and second, it stipulates a proportional payment of loss for failure to carry sufficient insurance. It makes sense that if insurance coverage is less than the value of the property, losses will not be paid in full because the premiums charged are for lower values. For property insurance, as long as coverage is at least 80 percent of the value of the property, the property is considered fully covered under the coinsurance provision.
What happens when you fail to have the amount of insurance of at least 80 percent of the value of your building? Nothing happens until you have a partial loss. At that time, you are subject to a penalty. Suppose in January you bought an $80,000 policy for a building with an actual cash value of $100,000, and the policy has an 80 percent coinsurance clause, which requires at least 80 percent of the value to be covered in order to receive the actual loss. By the time the building suffers a $10,000 loss in November, its actual cash value has increased to $120,000. The coinsurance limit is calculated as follows:
The amount the insurer pays is $8,333.33. Who pays the other $1,666.67? You do. Your penalty for failing to carry at least 80 percent of the actual value is to bear part of the loss. You will see in Chapter 1 "The Nature of Risk: Losses and Opportunities" that you should buy coverage for the value of the home and also include an inflation guard endorsement so that the value of coverage will keep up with inflation.
What if you have a total loss at the time the building is worth $120,000, and you have only $80,000 worth of coverage? Applying the coinsurance formula yields the following:
You would not receive $99,999.99, however, because the total amount of insurance is $80,000, which is the maximum amount the insurer is obligated to pay. When a loss equals or exceeds the amount of insurance required by the applicable percentage of coinsurance, the coinsurance penalty is not part of the calculation because the limit is the amount of coverage. The insurer is not obligated to pay more than the face amount of insurance in any event because a typical policy specifies this amount as its maximum coverage responsibility.
You save money buying a policy with a coinsurance clause because the insurer charges a reduced premium rate, but you assume a significant obligation. The requirement is applicable to values only at the time of loss, and the insurer is not responsible for keeping you informed of value changes. That is your responsibility.
Key Takeaways
In this section you studied the general features of property coverage:
- Insurable property is classified as either real or personal property, and this classification affects the property’s exposure to risks and basis for valuation
- Coverage amounts depend on valuation as either actual cash value or replacement cost new
- The use of deductibles reduces the cost of claims, the frequency of claims, and moral hazard; common forms of deductibles are straight, franchise, and disappearing
- A coinsurance clause requires insureds to carry an amount of insurance equal to a specified percentage of the value of the property in order to be paid the full amount of an incurred loss; otherwise insureds will be subject to penalty in the form of bearing a proportional amount of the loss
Discussion Questions
- What is the difference between real and personal property? Why do insurers make a distinction between them?
- What is a deductible? Provide illustrative examples of straight, franchise, and disappearing deductibles.
- What is the purpose of coinsurance? How does the policyholder become a coinsurer? Under what circumstances does this occur?
11.2 E-Commerce Property Risks
Learning Objectives
In this section we elaborate on the following:
- The increased frequency and severity of e-commerce property risks
- Five major categories of e-commerce property risks
- Loss-control steps that can reduce e-commerce property risks
- Availability of insurance as a means of transferring e-commerce property risks
This chapter, as noted above, introduces areas that are growing in importance in the world of insurance. Almost every home, family, and business has risk exposures because of the use of computers, the Internet, and the Web; we refer to this as e-commerce property riskBusiness risk exposures due to of the use of computers, the Internet, and the Web.. Think about your own courses at the university. Each professor emphasizes his or her communication with you on the Web site for the course. You use the Internet as a research tool. Every time you log on, you are exposed to risks from cyberspace. Most familiar to you is the risk of viruses. But there are many additional risk exposures from electronic business, both to you as an individual and to businesses. Businesses with a Web presence are those that offer professional services online and/or online purchasing. Some businesses are business to consumer (BTC); others are business to business (BTB).
Regardless of the nature of the use of the Internet, cyber attacks have become more frequent and have resulted in large financial losses. According to the 2002 Computer Security Institute/Federal Bureau of Investigation (CSI/FBI) Computer Crime and Security Survey, Internet-related losses increased from $100 million in 1997 to $456 million in 2002.Richard Power, “Computer Security Issues & Trends,” Vol. VIII, Mo I. The survey was conducted by the Computer Security Institute (CSI) with the participation of the San Francisco Federal Bureau of Investigation’s Computer Intrusion Squad. Established in 1974, CSI has thousands of members worldwide and provides a wide variety of information and education programs to assist in protecting the information assets of corporations and governmental organizations. For more information, go to http://www.gocsi.com. The 6th Annual CyberSource fraud survey indicated a $700 million increase (37 percent) in lost revenue in 2004, from an estimated $2.6 billion in 2003. Small and medium businesses were hit the hardest. These losses are in line with fast revenue growth from e-commerce.The 6th Annual CyberSource Fraud Survey was sponsored by CyberSource Corporation and undertaken by Mindwave Research. The survey was fielded September 17 through October 1, 2004, and yielded 348 qualified and complete responses (versus 333 the year before). The sample was drawn from a database of companies involved in electronic commerce activities. Copies of the survey are available by visiting http://www.cybersource.com/fraudreport/.
Businesses today are becoming aware of their e-commerce risk exposures. In every forum of insurers’ meetings and in every insurance media, e-risk exposure is discussed as one of the major “less understood” risk exposures.For example, see Lee McDonald,” Insurer Points out Risks of E-Commerce,” Best’s Review, February 2000; Ron Lent, “Electronic Risk Gives Insurers Pause,” National Underwriter, Property & Casualty/Risk & Benefits Management Edition, May 7, 2001; Caroline Saucer, “Technological Advances: Web Site Design Provides Clues to Underwriting Online Risks,” Best’s Review, December 2000. In this chapter, we discuss the hazards and perils of e-commerce risk exposure to the business itself as the first party. In Chapter 12 "The Liability Risk Management", we will discuss the liability side of the risk exposure of businesses due to the Internet and online connections. Next, we discuss the hazards and perils of electronic business in general.
Causes of Loss in E-Commerce
The 2004 CSI/FBI survey provided many categories of the causes of losses in the computer/electronic systems area. By frequency, the 2004 order of causes of losses were: virus (78 percent); insider abuse of net access (59 percent); laptop/mobile thefts (49 percent); unauthorized access to information (39 percent); system penetration (37 percent); denial of service (17 percent); theft of proprietary information (10 percent); and sabotage, financial fraud, and telecom fraud (less than 10 percent). This list does not account for the severity of losses in 2004; however, the 269 respondents to this section of the survey reported losses reaching $141.5 million.
The 2004 CSI/FBI survey covered a wide spectrum of risk exposure in e-commerce, for both first-party (property and business interruption) and third-party (liability losses, covered in Chapter 12 "The Liability Risk Management") losses. As you can see from this summary of the survey and other sources, the causes of e-commerce property risksBusiness risk exposures due to of the use of computers, the Internet, and the Web. are numerous. We can group these risks into five broad categories:
- Hardware and software thefts (information asset losses and corruption due to hackers, vandalism, and viruses)
- Technological changes
- Regulatory and legal changes
- Trademark infringements
- Internet-based telephony crimes
Hardware and Software Thefts
Companies have rapidly become dependent on computers. When a company’s computer system is down, regardless of the cause, the company risks losing weeks, months, or possibly years of data. Businesses store the majority of their information on computers. Customer databases, contact information, supplier information, order forms, and almost all documents a company uses to conduct business are stored on the computer system. Losses from theft of proprietary information, sabotage of data networks, or telecom eavesdropping can cause major losses to the infrastructure base of a business, whether it is done by outside hackers or by insider disgruntled employees.
Hackers and crackers can cause expensive, if not fatal, damage to a company’s computer systems. HackersVirtual vandals who try to poke holes in a company’s security network. are virtual vandals who try to poke holes in a company’s security network.George S. Sutcliffe, Esq., E-Commerce and Insurance Risk Management (Boston: Standard Publishing Corp., 2001), 13. Hackers may be satisfied with defacing Web sites, while crackersVandals who want to break in to a company’s security network and steal proprietary information for personal gain. are vandals who want to break in to a company’s security network and steal proprietary information for personal gain. Potential terrorists are usually classified as crackers. Their objective is to hit specific companies in order to bring systems down, steal data, or modify data to destroy its integrity. InsidersInternal employees who vandalize a company because they are upset with it for some reason. are internal employees upset with the company for some reason, perhaps because of a layoff or a failure to get an expected promotion. Inside access to the company computer network, and the knowledge of how to use it, gives this group the potential to cause the most damage to a business.
A virusProgram or code that replicates itself inside a personal computer or a workstation with the intent to destroy an operating system or control program. is a program or code that replicates itself inside a personal computer or a workstation with the intent to destroy an operating system or control program. When it replicates, it infects another program or document.Adapted from the online glossary of Symantec, a worldwide provider of Internet security solutions, at http://www.symantec.com/avcenter/refa.html.
Technological Changes
Another risk companies face in the cyber world is the rapid advancement of technology. When a company updates its computer system, its software package, or the process for conducting business using the computer system, business is interrupted while employees learn how to conduct business using the new system. The result of this downtime is lost revenue.
Regulatory and Legal Changes
Almost as quickly as the Internet is growing, the government is adding and changing applicable e-commerce laws. In the past, there were few laws because the Internet was not fully explored nor fully understood, but now, laws and regulations are mounting. Thus, companies engaged in e-commerce face legal risks arising from governmental involvement. An example of a law that is likely to change is the tax-free Internet sale. There is no sales tax imposed on merchants (and hence the consumer) on Internet sales between states partly because the government has not yet determined how states should apportion the tax revenue. As the volume of online purchases increases, so do the consequences of lost sales tax revenue from e-commerce.
Lack of qualified lawyers to handle cases that arise out of e-commerce disputes is another new risk. There are many areas of e-law that lawyers are not yet specialized in. Not only are laws complex and tedious, they are also changing rapidly. As a result, it is difficult for lawyers to stay abreast of each law that governs and regulates cyberspace.
Trademarks Infringements
Domain name disputes are a serious concern for many businesses. In most cases, disputes over the rights to a domain name result from two specific events. Domain name hijackingWhen an individual or a business reserves a domain name that uses the trademark of a competitor. occurs when an individual or a business reserves a domain name that uses the trademark of a competitor. The other event arises when a business or an individual reserves the well-recognized name or trademark of an unrelated company as a domain name with the intent of selling the domain name to the trademark holder. Seeking compensation for the use of a registered domain name from the rightful trademark holder is known as cybersquattingSeeking compensation for the use of a registered domain name from the rightful trademark holder..George S. Sutcliffe, Esq., E-Commerce and Insurance Risk Management (Boston: Standard Publishing Corp., 2001), 13.
A recent case involving cybersquatting is People for the Ethical Treatment of Animals v. Doughney. In August 2001, the Fourth Circuit Court of Appeals held that the defendant, Michael Doughney, was guilty of service mark infringement and unfair competition, and had violated the Anti-Cybersquatting Consumer Protection Act (ACPA). Doughney had created a Web site at http://www.peta.org, which contained the registered service mark PETA. People for the Ethical Treatment of Animals (PETA) is an animal rights organization that opposes the exploitation of animals for food, clothing, entertainment, and vivisection. When users typed in http://www.peta.org, they expected to arrive at the site for People for the Ethical Treatment of Animals. Instead, they surprisingly arrived at People Eating Tasty Animals, a “resource for those who enjoy eating meat, wearing fur and leather, hunting, and the fruits of scientific research.” The site contained links to a number of organizations that held views generally opposing those of PETA.People for the Ethical Treatment of Animals v. Doughney, No. 00-1918 (4th Cir2001); http://www.phillipsnizer.com/internetlib.htm. On two occasions, Doughney suggested that if PETA wanted one of his domains, or objected to his registration, it could “make me an offer” or “negotiate a settlement.”
Web site hijackingWhen a Web site operator knowingly deceives the user by redirecting the user to a site the user did not intend to view. occurs when a Web site operator knowingly deceives the user by redirecting the user to a site the user did not intend to view. A recent case, Ford Motor Company v. 2600 Enterprises et al., caught attention in December 2001 when 2600 Enterprises automatically redirected users from a Web site they operate at a domain name directing profanity at General Motors to the Web site operated by Ford at http://www.ford.com. The defendants redirected users by programming an embedded link, which utilized Ford’s mark, into the code of the defendants’ Web site.Ford Motor Company v. 2600 Enterprises et al., 177 F. Supp. 2d 661, 2001, U.S. District Court Lexis 21302 (E.D. Michigan2001); http://www.phillipsnizer.com/int-trademark.htm. Domain-name hijacking, cybersquatting, and Web site hijacking for the sake of parody or satire is protected by the First Amendment, but sometimes the pranksters’ only purpose is to harass or extract profit from the trademark owner.Monte Enbysk, “Hackers and Vandals and Worms, Oh My!” Microsoft bCentral newsletter, http://www.bcentral.com.
Internet-Based Telephony Crimes
One of the fastest-growing communication technologies is Internet-based telephony—known as voice-over-Internet protocol (VoIP). The National Institute of Standards and Technology warned that this technology has “inherent vulnerabilities”Simon London, “Government Warns Users on Risks of Internet-Based Telephony: Voip Is Growing in Popularity as the Technology Proliferates, but Inherent in the Service, Warns the Government, Is Increased Security and Privacy Flaws,” Financial Times, February 6, 2005, http://www.ft.com/cms/s/0/5fca499c-7554-11d9-9608-00000e2511c8.html (accessed March 15, 2009). because firewalls are not designed to help in securing this industry, which is grew by $903 million in 2005, up from $686 million in 2004.
Risk Management of E-Commerce Exposures
Businesses can take loss-control steps to reduce the e-commerce property and business interruption risks by using the following:
- Security products and processes
- System audits
- Antivirus protection
- Backup systems and redundancies
- Data protection and security
- Passwords
- Digital signatures
- Encryption
- Firewalls
- Virtual private network (VPN)
Businesses today buy electronic security systems and develop many steps to reduce the risk of data and hardware losses. Firms conduct regular system audits to test for breaches in network security. Auditors attempt to break into various components of the company computer system, including the operating systems, networks, databases, servers, Web servers, and business processes in general, to simulate attacks and discover weaknesses.Kevin Coleman, “How E-Tailers and Online Shoppers Can Protect Themselves,” KPMG. Managed security services provide an option for virus protection. They include both antivirus protection and firewall installation.
Regular system backup processes and off-site systems saved many businesses hurt by the September 11 attacks. One advantage of keeping backup data files off-site is having clean data in case of damage in the original files from viruses, hackers, and crackers. Because security may be breached from people within the company, Internet access is generally available only to authorized internal and external users via the use of passwords. E-mails are easy to intercept and read as they travel across the Internet. Attaching a digital signature allows the recipient to discern whether the document has been altered.George S. Sutcliffe, Esq., E-Commerce and Insurance Risk Management (Boston: Standard Publishing Corp., 2001), 13. Another method to protect e-mails is encryption. EncryptionAllows the sender of an e-mail to scramble the contents of the document. allows the sender of an e-mail to scramble the contents of the document. Before the recipient can read the message, he or she needs to use a password for a private key. Encryption is used for confidential communications.
A firewall is another loss-control solution that protects the local area network (LAN) or corporate network from unauthorized access. A firewallDevice that protects a network from intrusion by preventing access unless certain criteria are met. protects a network from intrusion by preventing access unless certain criteria are met. Another loss-control technique is the virtual private network, which connects satellite offices with a central location. A virtual private network (VPN)Network that connects satellite offices with a central location and allows remote users to gain secure access to a corporate network. allows remote users to gain secure access to a corporate network. VPNs provide endless opportunities for telecommuters, business travelers, and multiple independent offices of a bigger company.
E-Commerce Property Insurance
According to the 2004 CSI/FBI Computer Crime and Security Survey described above, only 28 percent of 320 respondents had any external insurance policies to help manage cyber security risks. Traditional property insurance covers physical damage to tangible property due to an insured peril. Electronic data can be considered property in most instances, but standard commercial insurance policies, discussed in Chapter 1 "The Nature of Risk: Losses and Opportunities", contain exclusions that “explicitly invalidate coverage for exposures in relation to the use of technology.”“New Policy Offered to Cover Tech Risks,” National Underwriter Online News Service, July 2, 2002; Stand Alone E-Commerce Market Survey, by IRMI at http://www.irmi.com/Expert/Articles/2001/Popups/Rossi02-1.aspx. Some insurers now offer customized e-commerce insurance policies that expand the areas of coverage available for e-commerce property risk. ISO has an e-commerce endorsement that modifies insurance provided under commercial property coverage. Under this endorsement,
insurers will pay for the cost to replace or restore electronic data which has suffered loss or damage by a Covered Cause of Loss…including the cost of data entry, re-programming and computer consultation services.
The endorsement has four sections. Section I describes the electronic data coverage. Section II defines the period of coverage as well as the coverage of business income, extra expenses, and resumption of e-commerce activity. Section III classifies covered and excluded perils; exclusions include mechanical breakdown; downtime due to viruses, unless the computer is equipped with antivirus software; errors or omissions in programming or data processing; errors in design, maintenance, or repair; damage to one computer on the network caused by repair or modification of any other computer on the network; interruption as a result of insufficient capacity; and unexplained failure. Section IV of the endorsement is for other provisions, explained in Chapter 10 "Structure and Analysis of Insurance Contracts".
In addition to this endorsement, a few insurers have created a variety of e-commerce policies. Some of the companies include ACE USA, Chubb, AIG, the Fidelity and Deposit Companies (members of Zurich Financial Services Group), Gulf Insurance Group, Legion Indemnity Company, and Lloyd’s of London. This list is by no means inclusive.George S. Sutcliffe, Esq., E-Commerce and Insurance Risk Management (Boston: Standard Publishing Corp., 2001), 13. These companies provide not only first-party e-commerce property and business interruption coverage, but also liability coverage for third-party liability risks. The liability coverage will be discussed in Chapter 12 "The Liability Risk Management". Because e-commerce does not see geographical boundaries, many policies provide worldwide e-commerce coverage.
Key Takeaways
In this section you studied the emerging exposure of e-commerce property risk:
- E-commerce property risks fall under five categories: hardware and software thefts, technological changes, regulatory and legal changes, trademark infringements, and Internet-based telephony crimes
- Cyber attacks have become more frequent and more costly in the financial losses they cause
- Hackers, crackers, insiders, and viruses are major causes of hardware and software theft and data losses
- Technological advancements cause downtime while employees learn how to use new systems and components
- Frequent additions to and changes in existing e-commerce laws creates compliance risks and lack of qualified lawyers to handle disputes.
- Domain name hijacking, cybersquatting, and Web site hijacking are all ways of infringing legitimate companies’ trademarks
- Voice-over-Internet protocol (VoIP) has inherent vulnerabilities due to the absence of effective security measures
- Loss-control steps that can reduce e-commerce property risks include security products, system audits, backup systems, and data protection
- While electronic data is considered property, it is typically excluded from standard commercial insurance policies, thus leading to the rise of customized e-commerce policies and endorsements
Discussion Questions
- What are the risk exposures of e-commerce?
- How should the property risk of e-commerce be managed?
- Describe the parts of an e-commerce endorsement.
- What are some of the potential e-commerce property losses that businesses face?
11.3 Global Property Exposures
Learning Objectives
In this section we elaborate on the following:
- Global risk exposures in the international competitive landscape
- Risk control measures for reducing common global risks
- Insurance options for global risk exposures
As with the Internet, global exposure is rapidly growing for many companies. This forces management to think about the unique problems that arise when companies cross national borders, also known as global riskThe unique problems that arise when companies cross national borders.. Political Risk Services (http://www.prsonline.com/), an organization that ranks countries for their instability, attaches a major cost to each country. This highlights the importance of understanding the countries that businesses decide to enter. In a survey conducted by the insurance broker AonMark E. Ruquet, “Big Firms Worry About Coverage for Political Risks Abroad,” National Underwriter Online News Service, August 9, 2001. The Aon survey asked 122 risk managers, chief financial officers, and others in similar positions of responsibility to assess various aspects of their overseas risks. The surveys were done by telephone and in some cases over the Internet. of Fortune 1,000 companies in the United States, 26 percent of the respondents felt comfortable with their political risk exposure and 29 percent felt comfortable with their global financial or economic risk exposure. While most respondents felt comfortable with their property/casualty coverages, only a small percentage felt comfortable with their political risk protection. The survey was conducted during May 2001, before the September 11 attack. In 2005, Aon provided a map of the political and economic risk around the world. The climate around the world has changed with the war in Iraq, a part of the world surrounded by major economic and political hot spots.
Political riskUnanticipated political events that disrupt the earning or profit-making ability of an enterprise. can be defined as unanticipated political events that disrupt the earning or profit-making ability of an enterprise. In “The Risk Report: Managing Political Risks,” insurance expert Kevin M. Quinley describes some of the perils that can affect a global organization: nationalization, privatization, expropriation (property taken away by the host nation according to its laws), civil unrest, revolution, foreign exchange restrictions, labor regulations, kidnapping, terrorism, seizure, and forfeiture. Some of the risks are considered political risks, others are economic risks. Table 11.2 "Ten Ways to Tune Up Management of Political Risks" explains some of these risks. In summary, the main categories of global risk exposure are as follows:
- Destabilized international political environment
- Heightened terrorism risk
- Legal risk due to changes in local laws
- Lack-of-data risk
- Currency inconvertibility risk
- Cultural barriers risks
According to the Risk Report, the nature of the risks has changed. Twenty years ago, the major risk was in the area of nationalization of capital assets, while the perils of today are more related to economic integration and the power of international financial markets. Experts agree that political risk looms larger after September 11, the war in Iraq, and the instability in the Middle East. Following the September 11 attack, Marsh and all large brokerage firms began providing political risk assessment services to clients worldwide.“Marsh to Begin Crisis Consulting Led by Anti-Terror Expert,” National Underwriter Online News Service, October 12, 2001; see Aon services at http://www.aon.com/risk_management/political_risk.jsp; see Willis services at http://www.willis.com/Services/Political%20Risk.aspx. The consulting includes formulating and reviewing crisis management plans for events such as natural disasters, product recalls, and terrorism. The plans are comprehensive, and they are integrated throughout the enterprise.
Table 11.2 Ten Ways to Tune Up Management of Political Risks
|
Reproduced with permission of the publisher, International Risk Management Institute, Inc., Dallas, Texas, from the Risk Report, copyright International Risk Management Institute, Inc., author Kevin Quinley CPCU, ARM. Further reproduction prohibited. For subscription information, phone 800-827-4242. Visit http://www.IRMI.com for practical and reliable risk and insurance information.
Legal Risk
Often, the decision to undertake operations in a particular country is made apart from any risk management considerations. Although the legal environment may have been carefully reviewed from the standpoint of firm operations, little information may have been obtained about insurance requirements and regulations. For example, in many countries, social insurance is much broader than in the United States and there are few, if any, alternatives available to the risk manager. The risk manager may be forced by regulations to purchase local coverage that is inadequate in covered perils or limits of liability. Particularly in less-developed countries, there simply may not be adequate insurance capacity to provide desirable amounts and types of coverage. The risk manager then must decide whether or not to ignore the regulations and use nonadmitted coverage.
Nonadmitted coverageContracts issued by a company not authorized to write insurance in the country where a risk exposure is located. involves contracts issued by a company not authorized to write insurance in the country where a risk exposure is located. Admitted insuranceContracts written by companies authorized to write insurance in the country where a risk exposure is located. is written by companies authorized to write insurance in the country where a risk exposure is located. Nonadmitted contracts have advantages to some U.S. policyholders: they are written in English; use U.S. dollars for premiums and claims, thus avoiding exchange rate risk; utilize terms and conditions familiar to U.S. risk managers; and provide flexibility in underwriting. However, such contracts may be illegal in some countries, and the local subsidiary may be subject to penalties if the contracts’ existence becomes known. Further, premium payment may not be tax deductible, even in countries where nonadmitted coverage is permitted. If nonadmitted insurance is purchased where it is prohibited, claim payments must be made to the parent corporation, which then has to find a way to transfer the funds to the local subsidiary.
Coverage is also affected by the codification of the legal system in the other countries. The Napoleonic code, for example, is used in France, Belgium, Egypt, Greece, Italy, Spain, and several other countries. Under this legal system, liability for negligence is not treated in the same way as liability is treated under the United States system of common law; any negligence not specifically mentioned in the code is dismissed. The common law system is based on legal precedence, and the judges play a much more significant role.
Data Risk
Another problem facing the international risk manager is the collection of adequate statistical information. Economic and statistical data commonly available in the United States may simply be nonexistent in other parts of the world. For example, census data providing an accurate reflection of mortality rates may not be available. Even in industrialized countries, statistics may need careful scrutiny because the method used to produce them may be vastly different from that typical to the risk manager’s experience. This is particularly true of rate-making data. Data may also be grossly distorted for political reasons. Officially stated inflation rates, for instance, are notoriously suspect in many countries.
Faced with this lack of reliable information, the risk manager has little choice but to proceed with caution until experience and internal data collection can supplement or confirm other data sources. Contacts with other firms in the same industry and with other foreign subsidiaries can provide invaluable sources of information.
Data collection and analysis are a problem not only in this broad sense. Communication between the corporate headquarters and foreign operations becomes difficult due to language barriers, cultural differences, and often a sense of antagonism about a noncitizen’s authority to make decisions. Particularly difficult under these circumstances are the identification and evaluation of exposures and the implementation of risk management tools. Loss control, for instance, is much more advanced and accepted in the United States than in most other countries. Encouraging foreign operations to install sprinklers, implement safety programs, and undertake other loss-control steps is generally quite difficult. Further, risk managers of U.S.-based multinational firms may have difficulty persuading foreign operations to accept retention levels as high as those used in the United States. Retention simply is not well accepted elsewhere.
Currency Risk
Any multinational transaction, where payments are transferred from one currency to another, is subject to exchange rate risk. Under the current system of floating exchange rates, the rate of currency exchange between any two countries is not fixed and may vary substantially over time. Currency exchange risk is in the area of liquidity and convertibility between currencies. The risk exposure is the inability of the global firm to exchange the currency and transfer out of hostile countries. How this kind of risk can be mitigated is explained in Chapter 5 "The Evolution of Risk Management: Enterprise Risk Management".
Cultural Differences Risk
As we are very acutely aware after the September 11, 2001, attacks, cultural differences are at the root of much of the trouble around the world. But this is not only in hostile events. When a business expands abroad, one of the first actions is the study of the local culture of doing business. If you ever were in the market in old Jerusalem, you may have experienced the differences in shopping. You learn very quickly that a merchant never expects you to buy the item for the quoted price. The haggling may take a long time. You may leave and come back before you buy the item you liked for less than half the originally quoted price. This is the culture. You are expected to bargain and negotiate. Another cultural difference is the “connection” or “protection.” Many business moves will never happen without the right connection with the right people in power.
Labor laws reflect another interesting cultural difference. In some countries, it is common to employ very young children—an act that is against the law in the United States. The families in these countries depend heavily on the income of their children. But an American business in such a country may be faced with an ethical dilemma: should it employ children or adhere to U.S. practices and labor laws?Etti G. Baranoff and Phyllis S. Myers, “Ethics in Insurance,” Academy of Insurance Education, Washington, D.C., instructional video with supplemental study guide (video produced by the Center for Video Education, 1997.) Islamic finance is very different from finance in the Western world; for example, in Islam, interest payments are not permitted. With the expanded involvement of many businesses in the Middle East and Islamic countries, many academics, as well as businesspeople, are learning about the special ways to conduct business there.
Global Risk Management
The steps in global risk management include processes to reduce risk and develop loss-control policies, along with obtaining the appropriate insurance. Table 11.2 "Ten Ways to Tune Up Management of Political Risks" lists ways to manage political risks. The steps include learning the culture of the country and becoming a good corporate citizen, learning about the reality of the country, and finding ways to avoid political and legal traps. In the area of insurance, the global firm first looks for public insurance policies. The U.S. government established an insurance program administered through the Overseas Private Investment Corporation (OPIC) in 1948. The types of coverage available include expropriation, confiscation, war risks, civil strife, unfair calling of guarantees, contract repudiation, and currency inconvertibility. These are shown in Table 11.2 "Ten Ways to Tune Up Management of Political Risks". OPIC insurance is available only in limited amounts and only in certain developing countries that have signed bilateral trade agreements with the United States for projects intended to aid development. Some private insurers, however, also provide political risk insurance. Private insurers do not have the same restrictions as OPIC, but country limits do exist to avoid catastrophe (dependent exposure units). Additional types of coverage, such as kidnap, ransom, and export license cancellation, are also provided by private insurers. Poor experience in this line of insurance has made coverage more difficult and costly to obtain.
After September 11, some insurers pulled out of the political risk market, while others took the opportunity to expand their global coverage offerings. A Canadian insurer reported that the demand for insurance for employee political risk and kidnap and ransom for a dozen global companies increased by 100 percent.Daniel Hays, “Insurer Finds Good Market in Political Risk,” National Underwriter Online News Service, November 28, 2001. Zurich North America and Chubb expanded their political risk insurance offerings to the Asian market.“Zurich North America Expands Political Risk Insurance to Asian Market,” National Underwriter Online News Service, April 6, 2002; John Jennings, “Political Risk Cover Demand Surges: Insurers,” National Underwriter, Property & Casualty/Risk & Benefits Management Edition, April 27, 1998. The private insurance market’s ability to meet the demand has been strengthening each year because customers require broader coverage with longer terms, up to ten years. Other companies expanding into the market are Bermuda’s Sovereign Risk, AIG, and Reliance, among others.
Until recently, long-term political risk insurance was available mostly from international government agencies such as the Washington-based Multilateral Investment Guarantee Corporation (MIGA), a member of the World Bank Group; OPIC; the United Kingdom’s Export Credit Guarantee Department; and the French government’s export credit agency, Coface. But now the private market has been competing in the longer-term coverages and has opened coverage to losses caused by war and currency inconvertibility. Capacity and limits increased as reinsurance became more readily available in this area of global risks. Lloyd’s of London, for example, offered about $100 million in limits in 2002, a huge increase from the $10 million it could provide in 1992, according to Investment Insurance International, the specialist political risk division of Aon Group. AIG has increased its limits to $30 million per risk, while the rest of the private market had about $55 million to work with.
Coverage is even available in Israel, where major concerns about security made investors and businesspeople nervous. A political risk team at Lloyd’s (MAP Underwriting) developed a policy to address those concerns.“Armed-Conflict Risks Covered,” National Underwriter, Property & Casualty/Risk & Benefits Management Edition, June 11, 2001. Many Internet sites deal with global risk. For example, Global Risk International at http://www.globalrisk.uk.com/ offers counterterrorist training, kidnap and ransom management, close protection, and surveillance. The policy gives peace of mind to businesses that believe in the economic future of Israel by protecting the effects of “war and other political violence on their investments, property and personnel.” This specific coverage includes acts of war.
As noted in Table 11.2 "Ten Ways to Tune Up Management of Political Risks", some global firms use captives for this exposure. Captives were discussed in Chapter 6 "The Insurance Solution and Institutions".
Key Takeaways
In this section you studied global risk exposures that arise from the increasingly international nature of business operations:
- Political risk results from unanticipated governmental destabilization that disrupts an enterprise’s profit-making ability
- Legal attitudes with respect to insurance can be very different in other parts of the world, leading many international companies to turn to nonadmitted coverage
- International data-gathering may be limited, suspect, or inconsistent with domestic techniques, so internal collection efforts and collaboration among businesses is often required
- Volatile currencies can create unfavorable exchange rates
- Cultural differences, especially as reflected in labor laws, pose ethical dilemmas for companies with opposing views in conducting business
- Public insurance policies available through groups like the Overseas Private Investment Corporation (OPIC) and the Multilateral Investment Guarantee Corporation (MIGA) provide options for mitigating global risks such as expropriation, confiscation, war risks, civil strife, and currency inconvertibility
- Private insurers have increased political risk insurance offerings such as coverage for kidnap, ransom, and export license cancellation in response to greater demand
Discussion Questions
- What is different about international property exposures compared with U.S. property exposures?
- Why might an American company operating in a foreign country choose to purchase nonadmitted coverage?
- Describe the steps of political risk management.
11.4 Review and Practice
- Assume you live on the Texas Gulf Coast, where hurricane damage can be extensive. Also assume that you own a two-story frame home valued at $120,000. You insured the house for $80,000, which was your purchase price four years ago. If you had a total loss, what reimbursement would you receive from your insurer? What if you had a loss of $10,000? (Assume an 80 percent coinsurance provision.)
-
Erin Lavinsky works for the Pharmacy On-Line company in Austin, Texas. She uses her business computer for personal matters and has received a few infected documents. She was too lazy to update her Norton Utilities and did not realize that she was sending her infected material to her coworkers. Before long, the whole system collapsed and business was interrupted for a day until the backup system was brought up. Respond to the following questions:
- Describe the types of risk exposures that Pharmacy On-Line is facing as a result of e-commerce.
- If Pharmacy On-Line purchased the ISO endorsement in Chapter 26 "Appendix C", would it be covered for the lost day?
- Describe what other risk exposures could interrupt the business of Pharmacy On-Line.
- What is a standard policy? Why is a standard policy desirable (or undesirable)?
-
Marina Del Ro Shipping Company expanded its operations to the Middle East just before September 11, 2001. Respond to the following questions:
- What are the global risk exposures of Marina Del Ro?
- What should Marina Del Ro do to mitigate these risks in terms of noninsurance and insurance solutions?
- Provide an example of a business interruption loss and of an extra expense loss in the e-commerce endorsement.




