This is “Profiling and Privacy”, section 14.8 from the book Getting the Most Out of Information Systems (v. 1.4). For details on it (including licensing), click here.
For more information on the source of this book, or why it is available for free, please see the project's home page. You can browse or download additional books there. To download a .zip file containing this book to use offline, simply click here.
14.8 Profiling and Privacy
Learning Objectives
- Understand the privacy concerns that arise as a result of using third-party or tracking cookies to build user profiles.
- Be aware of the negative consequences that could result from the misuse of third-party or tracking cookies.
- Know the steps Google has taken to demonstrate its sensitivity to privacy issues.
- Know the kinds of user information that Google stores, and the steps Google takes to protect the privacy of that information.
While AdSense has been wildly successful, contextual advertising has its limits. For example, what kind of useful targeting can firms really do based on the text of a news item on North Korean nuclear testing?R. Singel, “Online Behavioral Targeting Targeted by Feds, Critics,” Wired News, June 3, 2009. For more accurate targeting, Google offers what it calls “interest-based ads,” which is based on a third-party cookie that tracks browsing activity across Google properties and AdSense partner sites. AdSense builds a profile, identifying users within dozens of broad categories and over six hundred subcategories.R. Hof, “Behavioral Targeting: Google Pulls Out the Stops,” BusinessWeek, March 11, 2009. Of course, there’s a financial incentive to do this too. Ads deemed more interesting should garner more clicks, meaning more potential customer leads for advertisers, more revenue for Web sites that run AdSense, and more money for Google.
But while targeting can benefit Web surfers, users will resist if they feel that they are being mistreated, exploited, or put at risk. Negative backlash might also result in a change in legislation. The U.S. Federal Trade Commission has already called for more transparency and user control in online advertising and for requesting user consent (opt-inProgram (typically a marketing effort) that requires customer consent. This program is contrasted with opt-out programs, which enroll all customers by default.) when collecting sensitive data.R. Singel, “Online Behavioral Targeting Targeted by Feds, Critics,” Wired News, June 3, 2009. Mishandled user privacy could curtail targeting opportunities, limiting growth across the online advertising field. And with less ad support, many of the Internet’s free services could suffer.
Figure 14.13
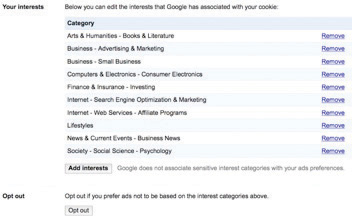
Here’s an example of one user’s interests, as tracked by Google’s “Interest-based Ads” and displayed in the firm’s “Ad Preferences Manager.”
Google’s roll-out of interest-based ads shows the firm’s sensitivity to these issues. The firm has also placed significant control in the hands of users, with options at program launch that were notably more robust than those of its competitors.S. Hansell, “A Guide to Google’s New Privacy Controls,” New York Times, March 12, 2009. Each interest-based ad is accompanied by an “Ads by Google” link that will bring users to a page describing Google advertising and which provides access to the company’s “Ads Preferences Manager.” This tool allows surfers to see any of the hundreds of potential categorizations that Google has assigned to that browser’s tracking cookie. Users can remove categorizations, and even add interests if they want to improve ad targeting. Some topics are too sensitive to track, and the technology avoids profiling race, religion, sexual orientation, health, political or trade union affiliation, and certain financial categories.R. Mitchell, “What Google Knows about You,” Computerworld, May 11, 2009.
Google also allows users to install a cookie that opts them out of interest-based tracking. And since browser cookies can expire or be deleted, the firm has gone a step further, offering a browser plug-inA small computer program that extends the feature set or capabilities of another application. that will remain permanent, even if a user’s opt-outPrograms that enroll all customers by default, but that allow consumers to discontinue participation if they want to. cookie is purged.
Google, Privacy Advocates, and the Law
Google’s moves are meant to demonstrate transparency in its ad targeting technology, and the firm’s policies may help raise the collective privacy bar for the industry. While privacy advocates have praised Google’s efforts to put more control in the hands of users, many continue to voice concern over what they see as the increasing amount of information that the firm houses.M. Helft, “BITS; Google Lets Users See a Bit of Selves” New York Times, November 9, 2009. For an avid user, Google could conceivably be holding e-mail (Gmail), photos (Picasa), social media activity (Google+), a Web surfing profile (AdSense and DoubleClick), location (Google Latitude), appointments (Google Calendar), music and other media (Google Play), files stored in the cloud (Google Drive), transcripts of phone messages (Google Voice), work files (Google Docs), and more.
Google insists that reports portraying it as a data-hoarding Big Brother are inaccurate. Data is not sold to third parties. Any targeting is fully disclosed, with users empowered to opt out at all levels.R. Mitchell, “What Google Knows about You,” Computerworld, May 11, 2009. Google has introduced several tools, including Google Dashboard and Google Ad Preferences Manager, that allow users to see information Google stores about them, clear their browsing history, and selectively delete collected data.“Policies and Principles,” Google, http://www.google.com/policies/privacy/ (accessed June 11, 2012). But critics counter that corporate intentions and data use policies (articulated in a Web site’s Terms of Service) can change over time, and that a firm’s good behavior today is no guarantee of good behavior in the future.R. Mitchell, “What Google Knows about You,” Computerworld, May 11, 2009. Google has modified its policy several times in the past, including changes that now allow the firm to link search history to ad targeting. It has also unified its privacy policy in a way that allows for greater profiling, sharing, and tailored services across Google offerings.C. Boulton, “Google Privacy Policy Changes are Live: Here are Your Options,” eWeek, March 1, 2012.
Google does enjoy a lot of user goodwill, and it is widely recognized for its unofficial motto “Don’t Be Evil.” However, some worry that even though Google might not be evil, it could still make a mistake, and that despite its best intentions, a security breach or employee error could leave data dangerously or embarrassingly exposed.
Gaffes have repeatedly occurred. A system flaw inadvertently shared some Google Docs with contacts who were never granted access to them.J. Kincaid, “Google Privacy Blunder Shares Your Docs without Permission,” TechCrunch, March 7, 2009. When the firm introduced its Google Buzz social networking service, many users were horrified that their most frequently used Gmail contacts were automatically added to Buzz, allowing others to see who you’re communicating with. As one report explained, “Suddenly, journalists’ clandestine contacts were exposed, secret affairs became dramatically less secret, and stalkers obtained a new tool to harass their victims. Oops.”A. Gold, “Keep Your Buzz to Yourself: Google Misjudged Its Users’ Right to Privacy,” The Harvard Crimson, February 22, 2010. Eleven congressmen subsequently asked the U.S. Federal Trade Commission to investigate the Google Buzz for possible breaches of consumer privacy.G. Gross, “Lawmakers Ask for FTC Investigation of Google Buzz,” PCWorld, March 29, 2010. Google admitted that some of its “Street View” cars, while driving through neighborhoods and taking photos for Google maps, had inadvertently collected personal data, including e-mails and passwords.A. Oreskovic, “Google Admits to Broader Collection of Personal Data,” Washington Post, October 23, 2010. And in May 2011, Google scrambled to plug a hole that could potentially allow hackers to access the contacts, calendars, and photos on Android phones connecting to the Internet over open Wi-Fi networks.D. Goldman, “Major Security Flaw Found in Android Phones,” CNN, May 18, 2011. A rogue employee was fired for violating the firm’s strict guidelines and procedures on information access.T. Kranzit, “Google Fired Engineer for Privacy Breach,” CNet, September 14, 2010. The firm has also been accused of bypassing privacy settings in Apple’s Safari web browser in order to better track users.D. Basulto, “Google, Safari, and Our Final Privacy Wake-Up Call,” The Washington Post, February 22, 2012.
Privacy advocates also worry that the amount of data stored by Google serves as one-stop shopping for litigators and government investigators. The counter argument points to the fact that Google has continually reflected an aggressive defense of data privacy in court cases. When Viacom sued Google over copyright violations in YouTube, the search giant successfully fought the original subpoena, which had requested user-identifying information.R. Mitchell, “What Google Knows about You,” Computerworld, May 11, 2009. Google has also resisted Justice Department subpoenas for search queries, while rivals have complied.A. Broache, “Judge: Google Must Give Feds Limited Access to Records,” CNET, March 17, 2006.
Google has also claimed that it has been targeted by some foreign governments that are deliberately hacking or interfering with the firm’s services in order to quash some information sharing and to uncover dissident activity.D. Rushe, “Google Accuses China of Interfering with Gmail E-mail System,” Guardian, March 20, 2011.
Google is increasingly finding itself in precedent-setting cases where the law is vague. Google’s Street View, for example, has been the target of legal action in the United States, Canada, Japan, Greece, and the United Kingdom. Varying legal environments create a challenge to the global rollout of any data-driven initiative.L. Sumagaysay, “Not Everyone Likes the (Google Street) View,” Good Morning Silicon Valley, May 20, 2009.
Ad targeting brings to a head issues of opportunity, privacy, security, risk, and legislation. Google is now taking a more active public relations and lobbying role to prevent misperceptions and to be sure its positions are understood. While the field continues to evolve, Google’s experience will lay the groundwork for the future of personalized technology and provide a case study for other firms that need to strike the right balance between utility and privacy. Despite differences, it seems clear to Google, its advocates, and its detractors that with great power comes great responsibility.
Key Takeaways
- Possible consequences resulting from the misuse of customer tracking and profiling technologies include user resistance and legislation. Mishandled user privacy could curtail targeting opportunities and limit growth in online advertising. With less ad support, many of the Internet’s free services could suffer.
- Google has taken several steps to protect user privacy. The firm offers several tools that enable users not only to see information that Google collects but also to delete, pause, or modify data collection and profiling terms.
- Google’s “Ads Preferences Manager” allows surfers to see, remove, and add to, any of the categorizations that Google has assigned to that browser’s tracking cookie. The technology also avoids targeting certain sensitive topics. The firm’s Privacy Dashboard provides additional access to and user control over Google’s profiling and data collection.
- Google allows users to install a cookie or plug-in that opts them out of interest-based tracking.
- Some privacy advocates have voiced concern over what they see as the increasing amount of information that Google and other firms collect.
- Even the best-intentioned and most competent firms can have a security breach that compromises stored information. Google has suffered privacy breaches from product flaws and poorly planned feature rollouts, as well as deliberate hacks and attacks. The firm has also changed policies regarding data collection and privacy as its services have evolved. Such issues may lead to further investigation, legislation, and regulation.
Questions and Exercises
- Gmail uses contextual advertising. The service will scan the contents of e-mail messages and display ads off to the side. Test the “creep out” factor in Gmail—create an account (if you don’t already have one), and send messages to yourself with controversial terms in them. Which ones showed ads? Which ones didn’t?
- Google has never built user profiles based on Gmail messages. Ads are served based on a real-time scanning of keywords. Is this enough to make you comfortable with Google’s protection of your own privacy? Why or why not?
- List the negative consequences that could result from the misuse of tracking cookies.
- What steps does Google take to protect the privacy of user information? What steps has Google taken to give users control over the user data that the firm collects and the ads the users wish to see?
- Which topics does “Ads Preferences Manager” avoid in its targeting system?
- Visit Google’s Ad Preferences page. Is Google tracking your interests? Do you think the list of interests is accurate? Browse the categories under the “Ad Interest” button. Would you add any of these categories to your profile? Why or why not? What do you gain or lose by taking advantage of Google’s “Opt Out” option? Visit rival ad networks. Do you have a similar degree of control? More or less?
- Visit Google Dashboard. What information is Google collecting about you? Does any of this surprise you? How do you suppose the firm uses this to benefit you? After seeing this information, did you make any changes to the settings in the privacy center? Why or why not?
- List the types of information that Google might store for an individual. Do you feel that Google is a fair and reliable steward for this information? Are there Google services or other online efforts that you won’t use due to privacy concerns? Why?
- Google’s “interest-based advertising” was launched as an opt-out effort. What are the pros and cons for Google, users, advertisers, and AdSense partner sites if Google were to switch to an opt-in system? How would these various constituencies be impacted if the government mandated that users explicitly opt in to third-party cookies and other behavior-tracking techniques?
- What is Google’s unofficial motto?
- What is “Street View”? Where and on what grounds is it being challenged?
- Cite two court cases where Google has mounted a vigorous defense of data privacy.
- Wired News quoted a representative of privacy watchdog group, The Center for Digital Democracy, who offered a criticism of online advertising. The representative suggested that online firms were trying to learn “everything about individuals and manipulate their weaknesses” and that the federal government should “investigate the role [that online ads] played in convincing people to take out mortgages they should not have.”R. Singel, “Online Behavioral Targeting Targeted by Feds, Critics,” Wired News, June 3, 2009. Do you think online advertising played a significant role in the mortgage crisis? What role do advertisers, ad networks, and content providers have in online advertising oversight? Should this responsibility be any different from oversight in traditional media (television, print, radio)? What guidelines would you suggest?
- Even well-intentioned firms can compromise user privacy. How have Google’s missteps compromised user privacy? As a manager, what steps would you take in developing and deploying information systems that might prevent these kinds of problems from occurring?




