This is “Where Are Vulnerabilities? Understanding the Weaknesses”, section 13.3 from the book Getting the Most Out of Information Systems (v. 1.2). For details on it (including licensing), click here.
For more information on the source of this book, or why it is available for free, please see the project's home page. You can browse or download additional books there. To download a .zip file containing this book to use offline, simply click here.
13.3 Where Are Vulnerabilities? Understanding the Weaknesses
Learning Objectives
- Recognize the potential entry points for security compromise.
- Understand infiltration techniques such as social engineering, phishing, malware, Web site compromises (such as SQL injection), and more.
- Identify various methods and techniques to thwart infiltration.
Figure 13.1
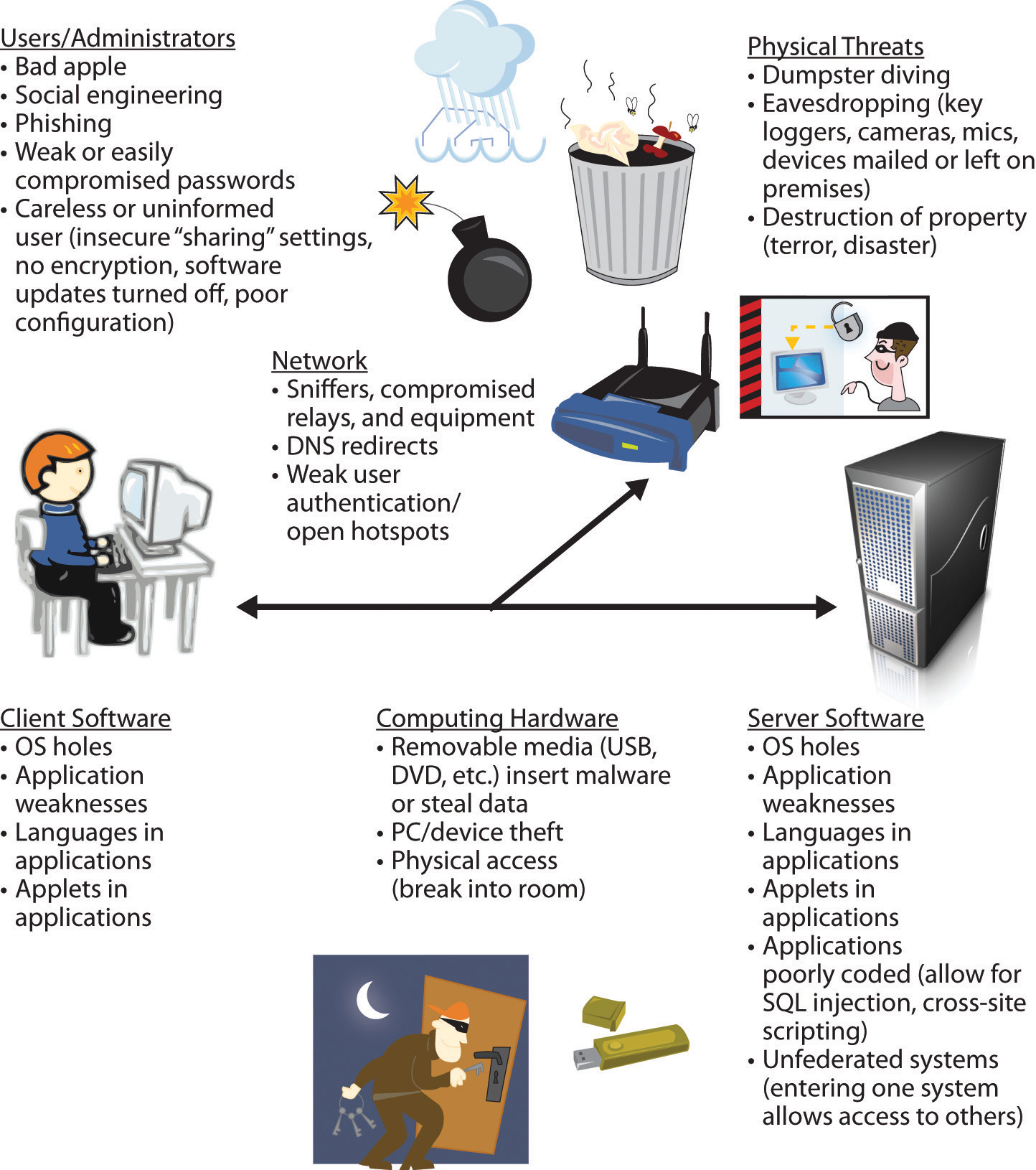
This diagram shows only some of the potential weaknesses that can compromise the security of an organization’s information systems. Every physical or network “touch point” is a potential vulnerability. Understanding where weaknesses may exist is a vital step toward improved security.
Modern information systems have lots of interrelated components and if one of these components fails, there might be a way in to the goodies. This creates a large attack surface for potential infiltration and compromise, as well as one that is simply vulnerable to unintentional damage and disruption.
User and Administrator Threats
Bad Apples
While some of the more sensational exploits involve criminal gangs, research firm Gartner estimates that 70 percent of loss-causing security incidents involve insiders.J. Mardesich, “Ensuring the Security of Stored Data,” CIO Strategy Center, 2009. Rogue employees can steal secrets, install malware, or hold a firm hostage. Check processing firm Fidelity National Information Services was betrayed when one of its database administrators lifted personal records on 2.3 million of the firm’s customers and illegally sold them to direct marketers.
And it’s not just firm employees. Many firms hire temporary staffers, contract employees, or outsource key components of their infrastructure. Other firms have been compromised by members of their cleaning or security staff. A contract employee working at Sentry Insurance stole information on 110,000 of the firm’s clients.J. Vijayan, “Software Consultant Who Stole Data on 110,000 People Gets Five-Year Sentence,” Computerworld, July 10, 2007.
Social Engineering
As P. T. Barnum is reported to have said, “There’s a sucker born every minute.” Con games that trick employees into revealing information or performing other tasks that compromise a firm are known as social engineering in security circles. In some ways, crooks have never had easier access to background information that might be used to craft a scam. It’s likely that a directory of a firm’s employees, their titles, and other personal details is online right now via social networks like LinkedIn and Facebook. With just a few moments of searching, a skilled con artist can piece together a convincing and compelling story.
A Sampling of Methods Employed in Social Engineering
- Impersonating senior management, a current or new end user needing help with access to systems, investigators, or staff (fake uniforms, badges)
- Identifying a key individual by name or title as a supposed friend or acquaintance
- Making claims with confidence and authority (“Of course I belong at this White House dinner.”)
- Baiting someone to add, deny, or clarify information that can help an attacker
- Using harassment, guilt, or intimidation
- Using an attractive individual to charm others into gaining information, favors, or access
- Setting off a series of false alarms that cause the victim to disable alarm systems
- Answering bogus surveys (e.g., “Win a free trip to Hawaii—just answer three questions about your network.”)
Data aggregator ChoicePoint sold private information to criminals who posed as legitimate clients, compromising the names, addresses, and Social Security numbers of some 145,000 individuals. In this breach, not a single computer was compromised. Employees were simply duped into turning data over to crooks. Gaffes like that can be painful. ChoicePoint paid $15 million in a settlement with the Federal Trade Commission, suffered customer loss, and ended up abandoning once lucrative businesses.G. Anthes, “The Grill: Security Guru Ira Winkler Takes the Hot Seat,” Computerworld, July 28, 2008.
Phishing
PhishingA con executed using technology, typically targeted at acquiring sensitive information or tricking someone into installing malicious software. refers to cons executed through technology. The goal of phishing is to leverage the reputation of a trusted firm or friend to trick the victim into performing an action or revealing information. The cons are crafty. Many have masqueraded as a security alert from a bank or e-commerce site (“Our Web site has been compromised, click to log in and reset your password.”), a message from an employer, or even a notice from the government (“Click here to update needed information to receive your tax refund transfer.”). Sophisticated con artists will lift logos, mimic standard layouts, and copy official language from legitimate Web sites or prior e-mails. Gartner estimates that these sorts phishing attacks cost consumers $3.2 billion in 2007.L. Avivah, “Phishing Attacks Escalate, Morph, and Cause Considerable Damage,” Gartner, December 12, 2007.
Other phishing attempts might dupe a user into unwittingly downloading dangerous software (malware) that can do things like record passwords and keystrokes, provide hackers with deeper access to your corporate network, or enlist your PC as part of a botnet. One attempt masqueraded as a message from a Facebook friend, inviting the recipient to view a video. Victims clicking the link were then told they need to install an updated version of the Adobe Flash plug-in to view the clip. The plug in was really a malware program that gave phishers control of the infected user’s computer.B. Krebs, “‘Koobface’ Worm Resurfaces on Facebook, MySpace,” Washington Post, March 2, 2009. Other attempts have populated P2P networks (peer-to-peer file distribution systems such as BitTorrent) with malware-installing files masquerading as video games or other software, movies, songs, and pornography.
So-called spear phishing attacks specifically target a given organization or group of users. In one incident, employees of a medical center received e-mails purportedly from the center itself, indicating that the recipient was being laid off and offering a link to job counseling resources. The link really offered a software payload that recorded and forwarded any keystrokes on the victim’s PC.C. Garretson, “Spam that Delivers a Pink Slip,” NetworkWorld, November 1, 2006. And with this type of phishing, the more you know about a user, the more convincing it is to con them. Phishers using pilfered résumé information from Monster.com crafted targeted and personalized e-mails. The request, seemingly from the job site, advised users to download the “Monster Job Seeker Tool”; this “tool” installed malware that encrypted files on the victim’s PC, leaving a ransom note demanding payment to liberate a victim’s hard disk.T. Wilson, “Trojan On Monster.com Steals Personal Data,” Forbes, August 20, 2007.
Don’t Take the Bait: Recognizing the “Phish Hooks”
Web browser developers, e-mail providers, search engines, and other firms are actively working to curtail phishing attempts. Many firms create blacklists that block access to harmful Web sites and increasingly robust tools screen for common phishing tactics. But it’s still important to have your guard up. Some exploits may be so new that they haven’t made it into screening systems (so-called zero-day exploits).
Never click on a link or download a suspicious, unexpected enclosure without verifying the authenticity of the sender. If something looks suspicious, don’t implicitly trust the “from” link in an e-mail. It’s possible that the e-mail address has been spoofedTerm used in security to refer to forging or disguising the origin or identity. E-mail transmissions and packets that have been altered to seem as if they came from another source are referred to as being “spoofed.” (faked) or that it was sent via a colleague’s compromised account. If unsure, contact the sender or your security staff.
Also know how to read the complete URL to look for tricks. Some firms misspell Web address names (http://wwwyourbank.com—note the missing period), set up subdomains to trick the eye (http://yourbank.com.sneakysite.com—which is hosted at sneakysite.com even though a quick glance looks like yourbank.com), or hijack brands by registering a legitimate firm’s name via foreign top-level domains (http://yourbank.cn).
A legitimate URL might also appear in a phishing message, but an HTML coding trick might make something that looks like http://yourbank.com/login actually link to http://sneakysite.com. Hovering your cursor over the URL or an image connected to a link should reveal the actual URL as a tool tip (just don’t click it, or you’ll go to that site).
Figure 13.2
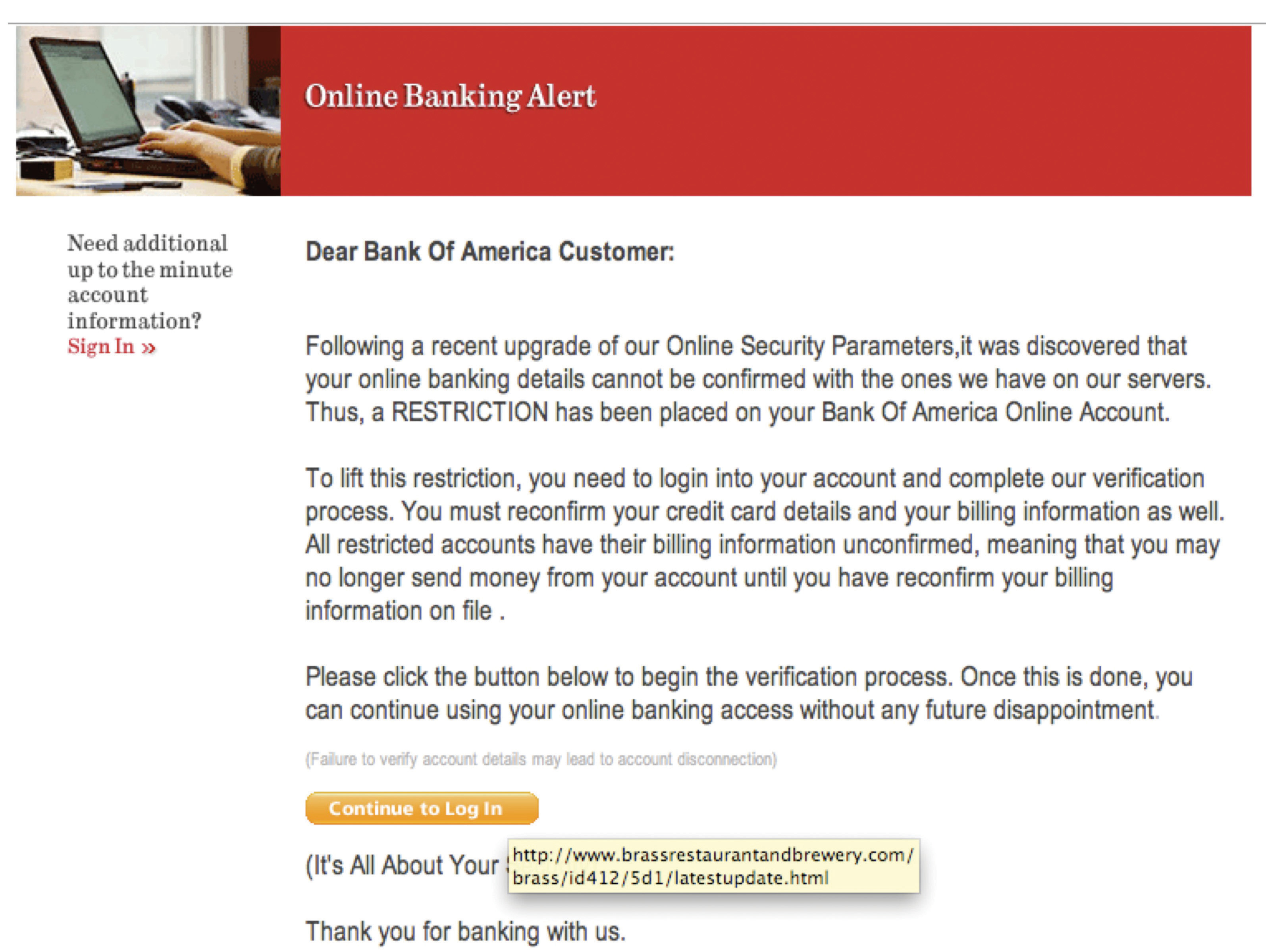
This e-mail message looks like it’s from Bank of America. However, hovering the cursor above the “Continue to Log In” button reveals the URL without clicking through to the site. Note how the actual URL associated with the link is not associated with Bank of America.
Figure 13.3
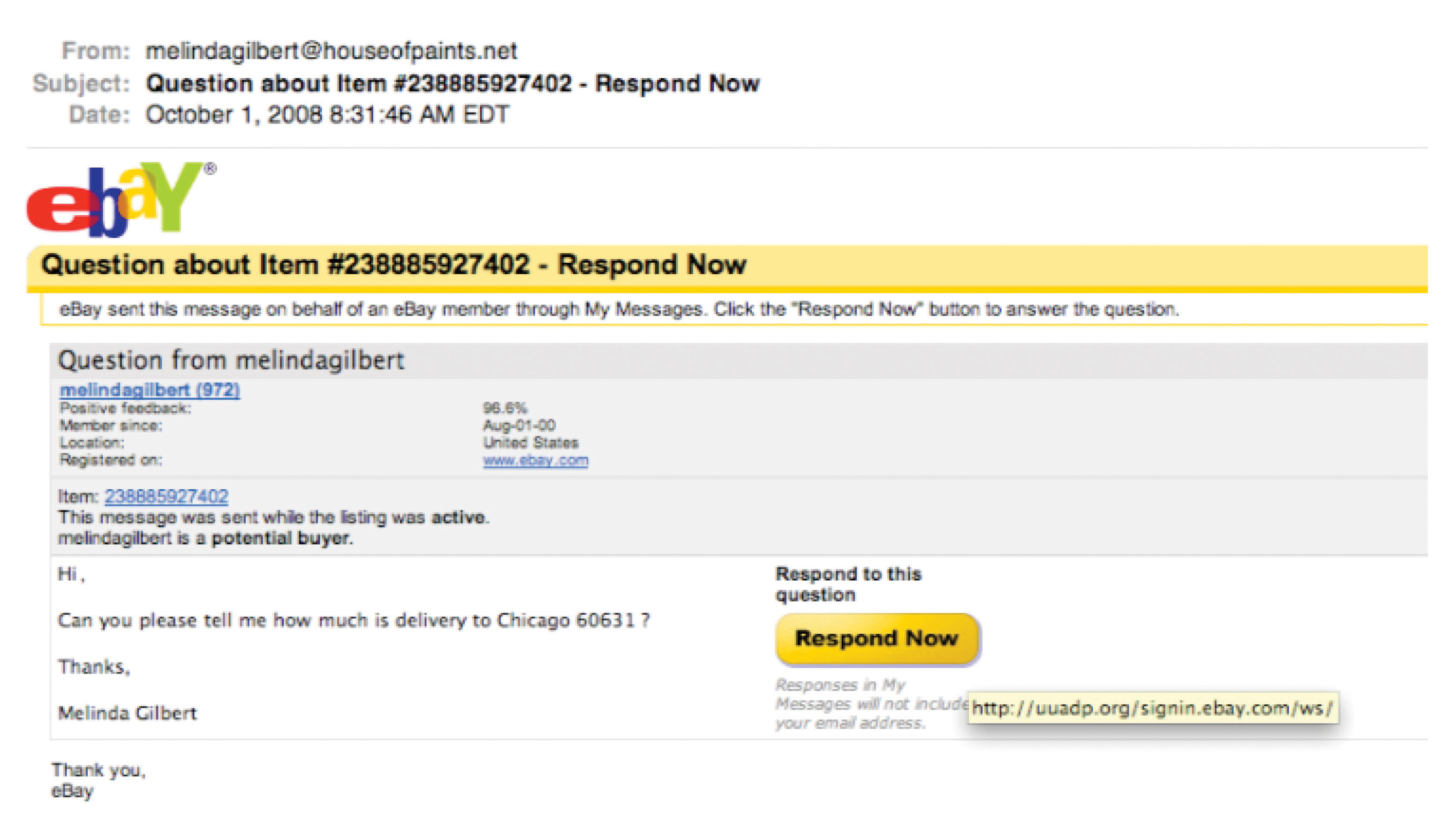
This image is from a phishing scheme masquerading as an eBay message. The real destination is a compromised .org domain unassociated with eBay, but the phishers have created a directory at this domain named “signin.ebay.com” in hopes that users will focus on that part of the URL and not recognize they’re really headed to a non-eBay site.
Web 2.0: The Rising Security Threat
Social networks and other Web 2.0 tools are a potential gold mine for crooks seeking to pull off phishing scams. Malware can send messages that seem to come from trusted “friends.” Messages such as status updates and tweets are short, and with limited background information, there are fewer contexts to question a post’s validity. Many users leverage bit.ly or other URL-shortening services that don’t reveal the Web site they link to in their URL, making it easier to hide a malicious link. While the most popular URL-shortening services maintain a blacklist, early victims are threatened by zero-day exploitsAttacks that are so new that they haven’t been clearly identified, and so they haven’t made it into security screening systems.. Criminals have also been using a variety of techniques to spread malware across sites or otherwise make them difficult to track and catch.
The technical openness of many Web 2.0 efforts can also create problems if schemes aren’t implemented properly. For example, Mark Zuckerberg’s Facebook page fell victim to hackers who used a hole in a Facebook API that allowed unauthorized status update posts to public Facebook fan pages.G. Cluley, “Mark Zuckerberg Fan Page Hacked on Facebook: What Really Happened?” NakedSecurity, January 27, 2011. APIs can allow firms to share services, collaborate, and enable mash-ups, but if code is poorly implemented it can also be an open back door where the bad guys can sneak in.
Some botnets have even used Twitter to communicate by sending out coded tweets to instruct compromised machines.UnsafeBits, “Botnets Go Public by Tweeting on Twitter,” Technology Review, August 17, 2009. Social media can also be a megaphone for loose lips, enabling a careless user to broadcast proprietary information to the public domain. A 2009 Congressional delegation to Iraq was supposed to have been secret. But Rep. Peter Hoekstra tweeted his final arrival into Baghdad for all to see, apparently unable to contain his excitement at receiving BlackBerry service in Iraq. Hoekstra tweeted, “Just landed in Baghdad. I believe it may be first time I’ve had bb service in Iraq. 11th trip here.” You’d think he would have known better. At the time, Hoekstra was a ranking member of the House Intelligence Committee!
Figure 13.4
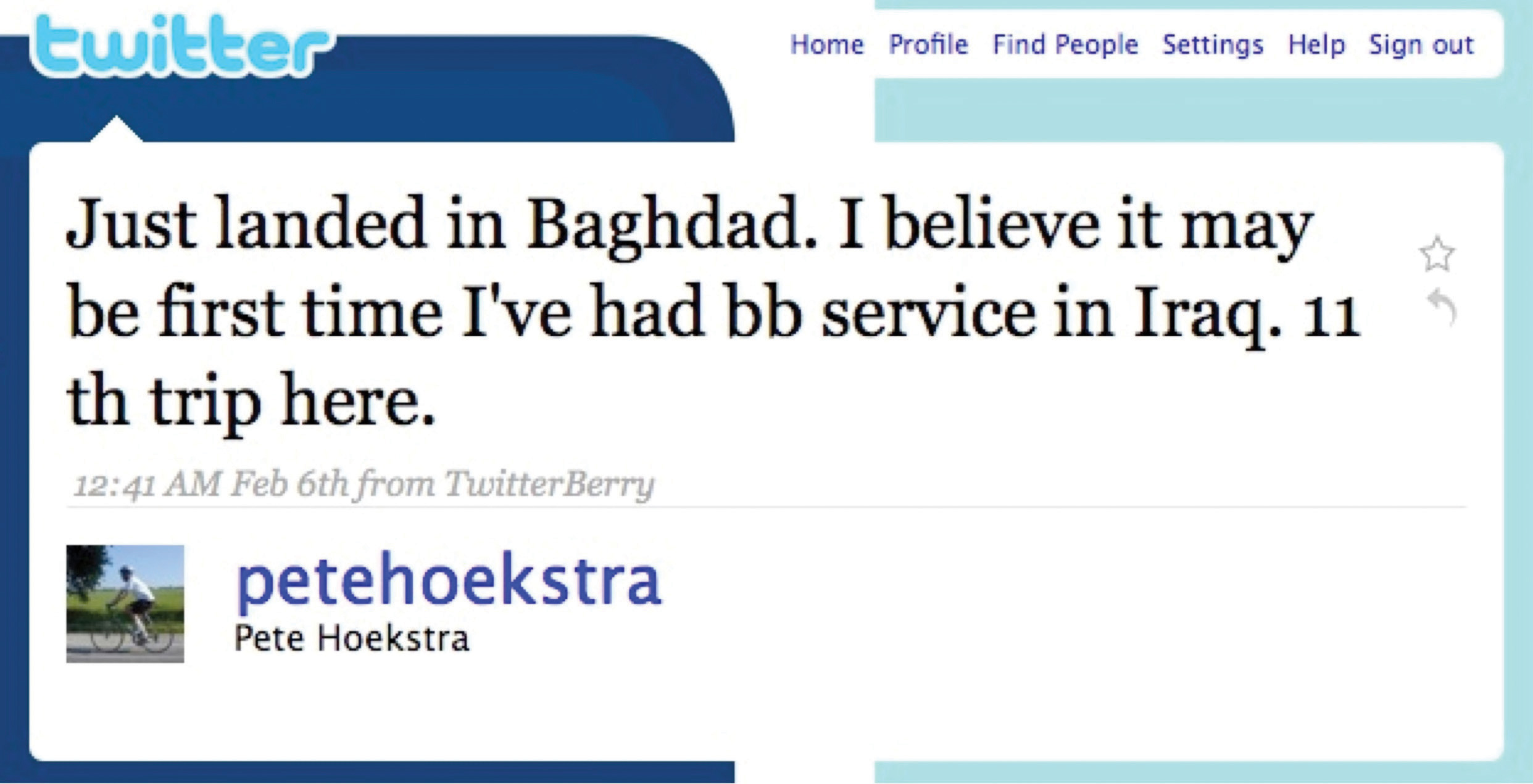
A member of the House Intelligence Committee uses Twitter and reveals his locale on a secret trip.
Passwords
Many valuable assets are kept secure via just one thin layer of protection—the password. And if you’re like most users, your password system is a mess.F. Manjoo, “Fix Your Terrible, Insecure Passwords in Five Minutes,” Slate, November 12, 2009. With so many destinations asking for passwords, chances are you’re using the same password (or easily guessed variants) in a way that means getting just one “key” would open many “doors.” The typical Web user has 6.5 passwords, each of which is used at four sites, on average.N. Summers, “Building a Better Password,” Newsweek, October 19, 2009. Some sites force users to change passwords regularly, but this often results in insecure compromises. Users make only minor tweaks (e.g., appending the month or year); they write passwords down (in an unlocked drawer or Post-it note attached to the monitor); or they save passwords in personal e-mail accounts or on unencrypted hard drives.
The challenge questions offered by many sites to automate password distribution and reset are often pitifully insecure. What’s your mother’s maiden name? What elementary school did you attend? Where were you born? All are pretty easy to guess. One IEEE study found acquaintances could correctly answer colleagues’ secret questions 28 percent of the time, and those who did not know the person still guessed right at a rate of 17 percent. Plus, within three to six months, 16 percent of study participants forgot answers to their own security questions.R. Lemos, “Are Your ‘Secret Questions’ Too Easily Answered?” Technology Review, May 18, 2009. In many cases, answers to these questions can be easily uncovered online. Chances are, if you’ve got an account at a site like Ancestry.com, classmates.com, or Facebook, then some of your secret answers have already been exposed—by you! A Tennessee teen hacked into Sarah Palin’s personal Yahoo! account (gov.palin@yahoo.com) in part by correctly guessing where she met her husband. A similar attack hit staffers at Twitter, resulting in the theft of hundreds of internal documents, including strategy memos, e-mails, and financial forecasts, many of which ended up embarrassingly posted online.N. Summers, “Building a Better Password,” Newsweek, October 19, 2009.
Related to the password problem are issues with system setup and configuration. Many vendors sell software with a common default password. For example, for years, leading database products came with the default account and password combination “scott/tiger.” Any firm not changing default accounts and passwords risks having an open door. Other firms are left vulnerable if users set systems for open access—say turning on file sharing permission for their PC. Programmers, take note: well-designed products come with secure default settings, require users to reset passwords at setup, and also offer strong warnings when security settings are made weaker. But unfortunately, there are a lot of legacy products out there, and not all vendors have the insight to design for out-of-the-box security.
Building a Better Password
There’s no simple answer for the password problem. BiometricsTechnologies that measure and analyze human body characteristics for identification or authentication. These might include fingerprint readers, retina scanners, voice and face recognition, and more. are often thought of as a solution, but technologies that replace conventionally typed passwords with things like fingerprint readers, facial recognition, or iris scans are still rarely used, and PCs that include such technologies are widely viewed as novelties. Says Carnegie Mellon University CyLab fellow Richard Power, “Biometrics never caught on and it never will.”N. Summers, “Building a Better Password,” Newsweek, October 19, 2009.
Other approaches leverage technology that distributes single use passwords. These might arrive via external devices like an electronic wallet card, key chain fob, or cell phone. Security firm RSA has even built the technology into BlackBerrys. Enter a user name and receive a phone message with a temporary password. Even if a system was compromised by keystroke capture malware, the password is only good for one session. Lost device? A central command can disable it. This may be a good solution for situations that demand a high level of security, and Wells Fargo and PayPal are among the firms offering these types of services as an option. However, for most consumer applications, slowing down users with a two-tier authentication system would be an impractical mandate.
While you await technical fixes, you can at least work to be part of the solution rather than part of the problem. It’s unlikely you’ve got the memory or discipline to create separate unique passwords for all of your sites, but at least make it a priority to create separate, hard-to-guess passwords for each of your highest priority accounts (e.g., e-mail, financial Web sites, corporate network, and PC). Remember, the integrity of a password shared across Web sites isn’t just up to you. That hot start-up Web service may not have the security resources or experience to protect your special code, and if that Web site’s account is hacked, your user name and password are now in the hands of hackers that can try out those “keys” across the Web’s most popular destinations.
Web sites are increasingly demanding more “secure” passwords, requiring users to create passwords at least eight characters in length and that include at least one number and other nonalphabet character. Beware of using seemingly clever techniques to disguise common words. Many commonly available brute-force password cracking tools run through dictionary guesses of common words or phrases, substituting symbols or numbers for common characters (e.g., “@” for “a,” “+” for “t”). For stronger security, experts often advise basing passwords on a phrase, where each letter makes up a letter in an acronym. For example, the phrase “My first Cadillac was a real lemon so I bought a Toyota” becomes “M1stCwarlsIbaT.”F. Manjoo, “Fix Your Terrible, Insecure Passwords in Five Minutes,” Slate, November 12, 2009. Be careful to choose an original phrase that’s known only by you and that’s easy for you to remember. Studies have shown that acronym-based passwords using song lyrics, common quotes, or movie lines are still susceptible to dictionary-style hacks that build passwords from pop-culture references (in one test, two of 144 participants made password phrases from an acronym of the Oscar Meyer wiener jingle).N. Summers, “Building a Better Password,” Newsweek, October 19, 2009. Finding that balance between something tough for others to guess yet easy for you to remember will require some thought—but it will make you more secure. Do it now!
Technology Threats (Client and Server Software, Hardware, and Networking)
Malware
Any accessible computing device is a potential target for infiltration by malware. Malware (for malicious software) seeks to compromise a computing system without permission. Client PCs and a firm’s servers are primary targets, but as computing has spread, malware now threatens nearly any connected system running software, including mobile phones, embedded devices, and a firm’s networking equipment.
Some hackers will try to sneak malware onto a system via techniques like phishing. In another high-profile hacking example, infected USB drives were purposely left lying around government offices. Those seemingly abandoned office supplies really contained code that attempted to infiltrate government PCs when inserted by unwitting employees.
Machines are constantly under attack. Microsoft’s Internet Safety Enforcement Team claims that the mean time to infection for an unprotected PC is less than five minutes.J. Markoff, “A Robot Network Seeks to Enlist Your Computer,” New York Times, October 20, 2008. Oftentimes malware attempts to compromise weaknesses in software—either bugs, poor design, or poor configuration.
Years ago, most attacks centered on weaknesses in the operating system, but now malware exploits have expanded to other targets, including browsers, plug-ins, and scripting languages used by software. BusinessWeek reports that Adobe has replaced Microsoft as the primary means by which hackers try to infect or take control of PCs. Even trusted Web sites have become a conduit to deliver malware payloads. More than a dozen sites, including those of the New York Times, USA Today, and Nature, were compromised when seemingly honest advertising clients switched on fake ads that exploit Adobe software.A. Ricadela, “Can Adobe Beat Back the Hackers?” BusinessWeek, November 19, 2009. Some attacks were delivered through Flash animations that direct computers to sites that scan PCs, installing malware payloads through whatever vulnerabilities are discovered. Others circulated via e-mail through PDF triggered payloads deployed when a file was loaded via Acrobat Reader. Adobe is a particularly tempting target, as Flash and Acrobat Reader are now installed on nearly every PC, including Mac and Linux machines.
Malware goes by many names. Here are a few of the more common terms you’re likely to encounter.Portions adapted from G. Perera, “Your Guide to Understanding Malware,” LaptopLogic.com, May 17, 2009.
Methods of infection are as follows:
- Viruses. Programs that infect other software or files. They require an executable (a running program) to spread, attaching to other executables. Viruses can spread via operating systems, programs, or the boot sector or auto-run feature of media such as DVDs or USB drives. Some applications have executable languages (macros) that can also host viruses that run and spread when a file is open.
- Worms. Programs that take advantage of security vulnerability to automatically spread, but unlike viruses, worms do not require an executable. Some worms scan for and install themselves on vulnerable systems with stunning speed (in an extreme example, the SQL Slammer worm infected 90 percent of vulnerable software worldwide within just ten minutes).M. Broersma, “Slammer—the First ‘Warhol’ Worm?” CNET, February 3, 2003.
- Trojans. Exploits that, like the mythical Trojan horse, try to sneak in by masquerading as something they’re not. The payload is released when the user is duped into downloading and installing the malware cargo, oftentimes via phishing exploits.
While the terms above cover methods for infection, the terms below address the goal of the malware:
- Botnets or zombie networks. Hordes of surreptitiously infected computers linked and controlled remotely by a central command. Botnets are used in crimes where controlling many difficult-to-identify PCs is useful, such as when perpetrating click fraud, sending spam, registering accounts that use CAPTCHAsAn acronym for Completely Automated Public Turing Test to Tell Computers and Humans Apart. CAPTCHAs are those scrambled character images that many sites require to submit some sort of entry (account setup, ticket buying). CAPTCHAs were developed because computers have difficulty discerning letters that are distorted or mixed inside a jumbled graphic. CAPTCHAs are meant to be a Turing Test—a test to distinguish if a task is being performed by a computer or a human.G. Keizer, “Botnet Busts Newest Hotmail CAPTCHA,” Computerworld, February 19, 2009. (those scrambled character images meant to thwart things like automated account setup or ticket buying), executing “dictionary” password cracking attempts, or launching denial-of-service attacks.
- Malicious adware. Programs installed without full user consent or knowledge that later serve unwanted advertisements.
- Spyware. Software that surreptitiously monitors user actions, network traffic, or scans for files.
- Keylogger. Type of spyware that records user keystrokes. Keyloggers can be either software-based or hardware, such as a recording “dongle” that is plugged in between a keyboard and a PC.
- Screen capture. Variant of the keylogger approach. This category of software records the pixels that appear on a user’s screen for later playback in hopes of identifying proprietary information.
- Blended threats. Attacks combining multiple malware or hacking exploits.
All the News Fit to Print (Brought to You by Scam Artists)
In fall 2009, bad guys posing as the telecom firm Vonage signed up to distribute ads through the New York Times Web site. Many firms that display online ads on their Web sites simply create placeholders on their Web pages, with the actual ad content served by the advertisers themselves (see Chapter 14 "Google in Three Parts: Search, Online Advertising, and Beyond" for details). In this particular case, the scam artists posing as Vonage switched off the legitimate-looking ads and switched on code that, according to the New York Times, “took over the browsers of many people visiting the site, as their screens filled with an image that seemed to show a scan for computer viruses. The visitors were then told that they needed to buy antivirus software to fix a problem, but the software was more snake oil than a useful program.”A. Vance, “Times Web Ads Show Security Breach,” New York Times, September 14, 2009. Sites ranging from Fox News, the San Francisco Chronicle, and British tech site The Register have also been hit with ad scams in the past. In the Times case, malware wasn’t distributed directly to user PCs, but by passing through ads from third parties to consumers, the Times became a conduit for a scam. In the same way that manufacturers need to audit their supply chain to ensure that partners aren’t engaged in sweatshop labor or disgraceful pollution, sites that host ads need to audit their partners to ensure they are legitimate and behaving with integrity.
The Virus in Your Pocket
Most mobile phones are really pocket computers, so it’s not surprising that these devices have become malware targets. And there are a lot of pathways to exploit. Malware might infiltrate a smartphone via e-mail, Internet surfing, MMS attachments, or even Bluetooth. The “commwarrior” mobile virus spread to at least eight countries, propagating from a combination of MMS messages and Bluetooth.J. Charney, “Commwarrior Cell Phone Virus Marches On,” CNET, June 5, 2005.
Most smartphones have layers of security to block the spread of malware, so hackers typically hunt for the weakest victims. Easy marks include “jail-broken” iPhones, devices with warranty-voiding modifications in which security restrictions are overridden to allow phones to be used off network, and for the installation of unsanctioned applications. Estimates suggest some 10 percent of iPhones are jail-broken, and early viruses exploiting the compromised devices ranged from a “Rick roll” that replaced the home screen image with a photo of 1980s crooner Rick AstleyS. Steade, “It’s Shameless How They Flirt,” Good Morning Silicon Valley, November 9, 2009. to the more nefarious Ikee.B, which scanned text messages and hunted out banking codes, forwarding the nabbed data to a server in Lithuania.R. Lemos, “Nasty iPhone Worm Hints at the Future,” Technology Review, November 29, 2009.
The upside? Those smart devices are sometimes crime fighters themselves. A Pittsburgh mugging victim turned on Apple’s “Find My iPhone” feature within its MobileMe service, mapping the perpetrator’s path, then sending the law to bust the bad guys while they ate at a local restaurant.J. Murrell, “The iWitness News Roundup: Crime-fighting iPhone,” Good Morning Silicon Valley, August 31, 2009.
Figure 13.5
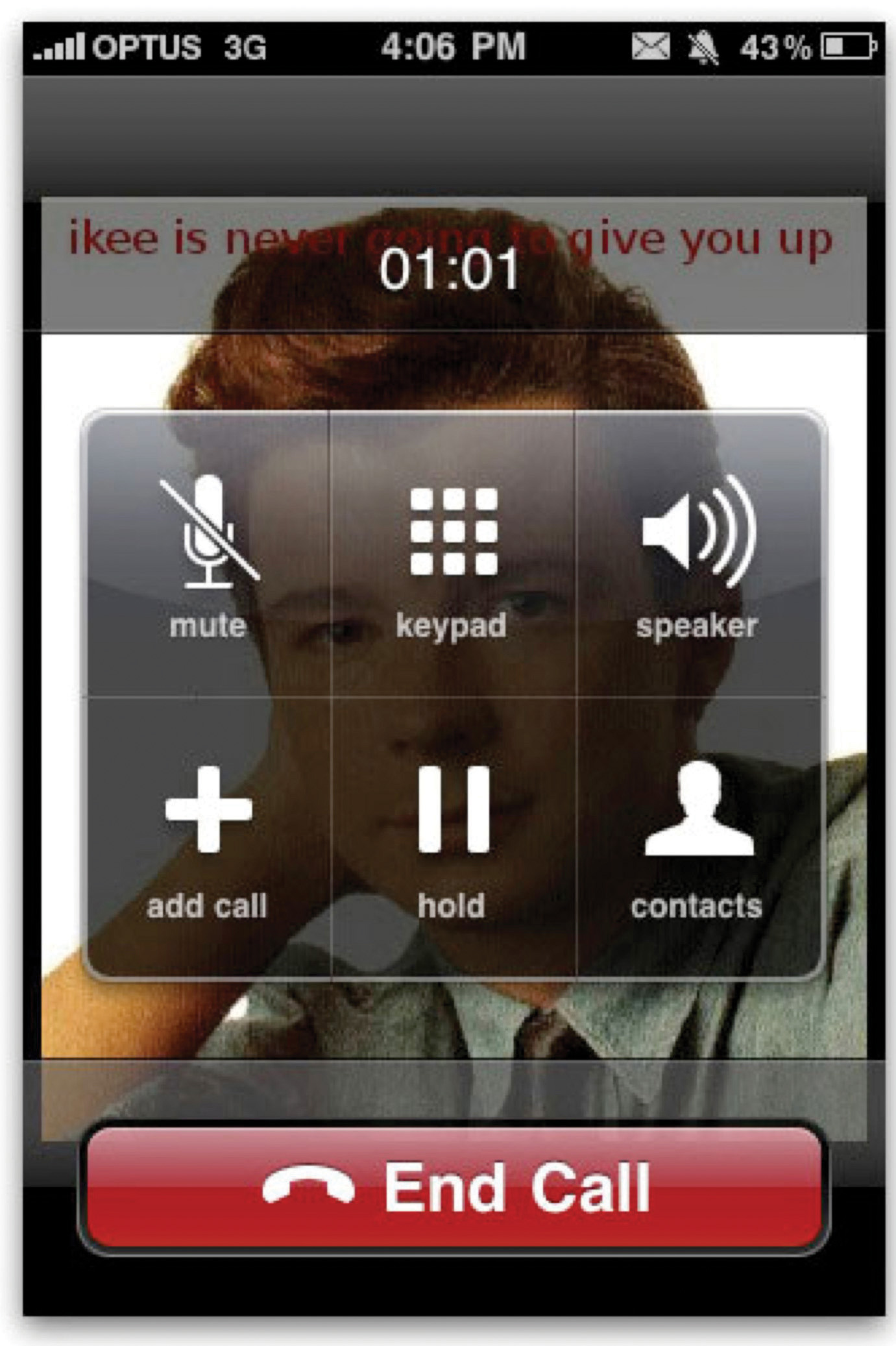
A “jail-broken” iPhone gets “Rick rolled” by malware.
Compromising Web Sites
Some exploits directly target poorly designed and programmed Web sites. Consider the SQL injection technique. It zeros in on a sloppy programming practice where software developers don’t validate user input.
It works like this. Imagine that you visit a Web site and are asked to enter your user ID in a field on a Web page (say your user ID is smith). A Web site may be programmed to take the data you enter from the Web page’s user ID field (smith), then add it to a database command (creating the equivalent of a command that says “find the account for ‘smith’”). The database then executes that command.
But Web sites that don’t verify user entries and instead just blindly pass along entered data are vulnerable to attack. Hackers with just a rudimentary knowledge of SQL could type actual code fragments into the user ID field, appending this code to statements executed by the site (see sidebar for a more detailed description). Such modified instructions could instruct the Web site’s database software to drop (delete) tables, insert additional data, return all records in a database, or even redirect users to another Web site that will scan clients for weaknesses, then launch further attacks. Security expert Ben Schneier noted a particularly ghastly SQL injection vulnerability in the publicly facing database for the Oklahoma Department of Corrections, where “anyone with basic SQL knowledge could have registered anyone he wanted as a sex offender.”B. Schneier, “Oklahoma Data Leak,” Schneier on Security, April 18, 2008.
Not trusting user input is a cardinal rule of programming, and most well-trained programmers know to validate user input. But there’s a lot of sloppy code out there, which hackers are all too eager to exploit. IBM identifies SQL injection as the fastest growing security threat, with over half a million attack attempts recorded each day.A. Wittmann, “The Fastest-Growing Security Threat,” InformationWeek, November 9, 2009. Some vulnerable systems started life as quickly developed proofs of concepts, and programmers never went back to add the needed code to validate input and block these exploits. Other Web sites may have been designed by poorly trained developers who have moved on to other projects, by staff that have since left the firm, or where development was outsourced to another firm. As such, many firms don’t even know if they suffer from this vulnerability.
SQL injection and other application weaknesses are particularly problematic because there’s not a commercial software patch or easily deployed piece of security software that can protect a firm. Instead, firms have to meticulously examine the integrity of their Web sites to see if they are vulnerable.While some tools exist to automate testing, this is by no means as easy a fix as installing a commercial software patch or virus protection software.
How SQL Injection Works
For those who want to get into some of the geekier details of a SQL injection attack, consider a Web site that executes the code below to verify that an entered user ID is in a database table of usernames. The code executed by the Web site might look something like this:
"SELECT * FROM users WHERE userName = '" + userID + "';"
The statement above tells the database to SELECT (find and return) all columns (that’s what the “*” means) from a table named users where the database’s userName field equals the text you just entered in the userID field. If the Web site’s visitor entered smith, that text is added to the statement above, and it’s executed as:
"SELECT * FROM users WHERE userName = 'smith';"
No problem. But now imagine a hacker gets sneaky and instead of just typing smith, into the Web site’s userID field, they also add some additional SQL code like this:
smith'; DROP TABLE users; DELETE * FROM users WHERE 't' = 't
If the programming statement above is entered into the user ID, the Web site adds this code to its own programming to create a statement that is executed as:
SELECT * FROM users WHERE userName = 'smith'; DELETE * FROM users WHERE 't' = 't';
The semicolons separate SQL statements. That second statement says delete all data in the users table for records where ‘t’ = ‘t’ (this last part, ‘t’ = ‘t,’ is always true, so all records will be deleted). Yikes! In this case, someone entering the kind of code you’d learn in the first chapter of SQL for Dummies could annihilate a site’s entire user ID file using one of the site’s own Web pages as the attack vehicle.B. Schneier, “Oklahoma Data Leak,” Schneier on Security, April 18, 2008.
Related programming exploits go by names such as cross-site scripting attacks and HTTP header injection. We’ll spare you the technical details, but what this means for both the manager and the programmer is that all systems must be designed and tested with security in mind. This includes testing new applications, existing and legacy applications, partner offerings, and SaaS (software as a service) applications—everything. Visa and MasterCard are among the firms requiring partners to rigorously apply testing standards. Firms that aren’t testing their applications will find they’re locked out of business; if caught with unacceptable breaches, such firms may be forced to pay big fines and absorb any costs associated with their weak practices.“Information Security: Why Cybercriminals Are Smiling,” Knowledge@Wharton, August 19, 2009.
Push-Button Hacking
Not only are the list of technical vulnerabilities well known, hackers have created tools to make it easy for the criminally inclined to automate attacks. Chapter 14 "Google in Three Parts: Search, Online Advertising, and Beyond" outlines how Web sites can interrogate a system to find out more about the software and hardware used by visitors. Hacking toolkits can do the same thing. While you won’t find this sort of software for sale on Amazon, a casual surfing of the online underworld (not recommended or advocated) will surface scores of tools that probe systems for the latest vulnerabilities then launch appropriate attacks. In one example, a $700 toolkit (MPack v. 86) was used to infiltrate a host of Italian Web sites, launching Trojans that infested 15,000 users in just a six-day period.“Web Threats Whitepaper,” Trend Micro, March 2008. As an industry executive in BusinessWeek has stated, “The barrier of entry is becoming so low that literally anyone can carry out these attacks.”J. Schectman, “Computer Hacking Made Easy,” BusinessWeek, August 13, 2009.
Network Threats
The network itself may also be a source of compromise. Recall that the TJX hack happened when a Wi-Fi access point was left open and undetected. A hacker just drove up and performed the digital equivalent of crawling through an open window. The problem is made more challenging since wireless access points are so inexpensive and easy to install. For less than $100, a user (well intentioned or not) could plug in to an access point that could provide entry for anyone. If a firm doesn’t regularly monitor its premises, its network, and its network traffic, it may fall victim.
Other troubling exploits have targeted the very underpinning of the Internet itself. This is the case with so-called DNS cache poisoning. The DNS, or domain name service, is a collection of software that maps an Internet address, such as (http://www.bc.edu), to an IP address, such as 136.167.2.220. 220 (see Chapter 12 "A Manager’s Guide to the Internet and Telecommunications" for more detail). DNS cache poisoning exploits can redirect this mapping and the consequences are huge. Imagine thinking that you’re visiting your bank’s Web site, but instead your network’s DNS server has been poisoned so that you really visit a carefully crafted replica that hackers use to steal your log-in credentials and drain your bank account. A DNS cache poisoning attack launched against one of China’s largest ISPs redirected users to sites that launched malware exploits, targeting weaknesses in RealPlayer, Adobe Flash, and Microsoft’s ActiveX technology, commonly used in browsers.J. London, “China Netcom Falls Prey to DNS Cache Poisoning,” Computerworld, August 22, 2008.
Physical Threats
A firm doesn’t just have to watch out for insiders or compromised software and hardware; a host of other physical threats can grease the skids to fraud, theft, and damage. Most large firms have disaster-recovery plans in place. These often include provisions to backup systems and data to off-site locales, to protect operations and provide a fall back in the case of disaster. Such plans increasingly take into account the potential impact of physical security threats such as terrorism, or vandalism, as well.
Anything valuable that reaches the trash in a recoverable state is also a potential security breach. Hackers and spies sometimes practice dumpster divingCombing through trash to identify valuable assets., sifting through trash in an effort to uncover valuable data or insights that can be stolen or used to launch a security attack. This might include hunting for discarded passwords written on Post-it notes, recovering unshredded printed user account listings, scanning e-mails or program printouts for system clues, recovering tape backups, resurrecting files from discarded hard drives, and more.
Other compromises might take place via shoulder surfingGaining compromising information through observation (as in looking over someone’s shoulder)., simply looking over someone’s shoulder to glean a password or see other proprietary information that might be displayed on a worker’s screen.
Firms might also fall victim to various forms of eavesdropping, such as efforts to listen into or record conversations, transmissions, or keystrokes. A device hidden inside a package might sit inside a mailroom or a worker’s physical inbox, scanning for open wireless connections, or recording and forwarding conversations.J. Robertson, “Hackers Mull Physical Attacks on a Networked World,” San Francisco Chronicle, August 8, 2008. Other forms of eavesdropping can be accomplished via compromised wireless or other network connections, malware keylogger or screen capture programs, as well as hardware devices such as replacement keyboards with keyloggers embedded inside, microphones to capture the slightly unique and identifiable sound of each key being pressed, programs that turn on built-in microphone or cameras that are now standard on many PCs, or even James Bond-style devices using Van Eck techniques that attempt to read monitors from afar by detecting their electromagnetic emissions.
The Encryption Prescription
During a routine physical transfer of backup media, Bank of America lost tapes containing the private information—including Social Security and credit card numbers—of hundreds of thousands of customers.J. Mardesich, “Ensuring the Security of Stored Data,” CIO Strategy Center, 2009. This was potentially devastating fodder for identity thieves. But who cares if someone steals your files if they still can’t read the data? That’s the goal of encryption!
EncryptionScrambling data using a code or formula, known as a cipher, such that it is hidden from those who do not have the unlocking key. scrambles data, making it essentially unreadable to any program that doesn’t have the descrambling password, known as a keyCode that unlocks encryption.. Simply put, the larger the key, the more difficult it is for a brute-force attack to exhaust all available combinations and crack the code. When well implemented, encryption can be the equivalent of a rock solid vault. To date, the largest known brute-force attacksAn attack that exhausts all possible password combinations in order to break into an account. The larger and more complicated a password or key, the longer a brute-force attack will take., demonstration hacks launched by grids of simultaneous code-cracking computers working in unison, haven’t come close to breaking the type of encryption used to scramble transmissions that most browsers use when communicating with banks and shopping sites. The problem occurs when data is nabbed before encryption or after decrypting, or in rare cases, if the encrypting key itself is compromised.
Extremely sensitive data—trade secrets, passwords, credit card numbers, and employee and customer information—should be encrypted before being sent or stored.J. Mardesich, “Ensuring the Security of Stored Data,” CIO Strategy Center, 2009. Deploying encryption dramatically lowers the potential damage from lost or stolen laptops, or from hardware recovered from dumpster diving. It is vital for any laptops carrying sensitive information.
Encryption is also employed in virtual private network (VPN) technology, which scrambles data passed across a network. Public wireless connections pose significant security threats—they may be set up by hackers that pose as service providers, while really launching attacks on or monitoring the transmissions of unwitting users. The use of VPN software can make any passed-through packets unreadable. Contact your firm or school to find out how to set up VPN software.
In the Bank of America example above, the bank was burned. It couldn’t verify that the lost tapes were encrypted, so it had to notify customers and incur the cost associated with assuming data had been breached.J. Mardesich, “Ensuring the Security of Stored Data,” CIO Strategy Center, 2009.
Encryption is not without its downsides. Key management is a potentially costly procedural challenge for most firms. If your keys aren’t secure, it’s the equivalent of leaving the keys to a safe out in public. Encryption also requires additional processing to scramble and descramble data—drawing more power and slowing computing tasks. Moore’s Law will speed things along, but it also puts more computing power in the hands of attackers. With hacking threats on the rise, expect to see laws and compliance requirements that mandate encrypted data, standardize encryption regimes, and simplify management.
How Do Web Sites Encrypt Transmissions?
Most Web sites that deal with financial transactions (e.g., banks, online stores) secure transmissions using a method called public key encryptionA two key system used for securing electronic transmissions. One key distributed publicly is used to encrypt (lock) data, but it cannot unlock data. Unlocking can only be performed with the private key. The private key also cannot be reverse engineered from the public key. By distributing public keys, but keeping the private key, Internet services can ensure transmissions to their site are secure.. The system works with two keys—a public key and a private key. The public key can “lock” or encrypt data, but it can’t unlock it: that can only be performed by the private key. So a Web site that wants you to transmit secure information will send you a public key—you use this to lock the data, and no one that intercepts that transmission can break in unless they’ve got the private key. If the Web site does its job, it will keep the private key out of reach of all potentially prying eyes.
Wondering if a Web site’s transmissions are encrypted? Look at the Web address. If it begins with “https” instead of “http”, it should be secure. Also, look for the padlock icon in the corner of your Web browser to be closed (locked). Finally, you can double click the padlock to bring up a verification of the Web site’s identity (verified by a trusted third party firm, known as a certificate authorityA trusted third party that provides authentication services in public key encryption schemes.). If this matches your URL and indicates the firm you’re doing business with, then you can be pretty sure verified encryption is being used by the firm that you intend to do business with.
Figure 13.6

In this screenshot, a Firefox browser is visiting Bank of America. The padlock icon was clicked to bring up digital certificate information. Note how the Web site’s name matches the URL. The verifying certificate authority is the firm VeriSign.
Key Takeaways
- An organization’s information assets are vulnerable to attack from several points of weakness, including users and administrators, its hardware and software, its networking systems, and various physical threats.
- Social engineering attempts to trick or con individuals into providing information, while phishing techniques are cons conducted through technology.
- While dangerous, a number of tools and techniques can be used to identify phishing scams, limiting their likelihood of success.
- Social media sites may assist hackers in crafting phishing or social engineering threats, provide information to password crackers, and act as conduits for unwanted dissemination of proprietary information.
- Most users employ inefficient and insecure password systems; however, techniques were offered to improve one’s individual password regime.
- Viruses, worms, and Trojans are types of infecting malware. Other types of malware might spy on users, enlist the use of computing assets for committing crimes, steal assets, destroy property, serve unwanted ads, and more.
- Examples of attacks and scams launched through advertising on legitimate Web pages highlight the need for end-user caution, as well as for firms to ensure the integrity of their participating online partners.
- SQL injection and related techniques show the perils of poor programming. Software developers must design for security from the start—considering potential security weaknesses, and methods that improve end-user security (e.g., in areas such as installation and configuration).
- Encryption can render a firm’s data assets unreadable, even if copied or stolen. While potentially complex to administer and resource intensive, encryption is a critical tool for securing an organization’s electronic assets.
Questions and Exercises
- Consider your own personal password regime and correct any weaknesses. Share any additional password management tips and techniques with your class.
- Why is it a bad idea to use variants of existing passwords when registering for new Web sites?
- Relate an example of social engineering that you’ve experienced or heard of. How might the victim have avoided being compromised?
- Have you ever seen phishing exploits? Have you fallen for one? Why did you take the bait, or what alerted you to the scam? How can you identify phishing scams?
- Have you or has anyone you know fallen victim to malware? Relate the experience—how do you suppose it happened? What damage was done? What, if anything, could be done to recover from the situation?
- Why are social media sites such a threat to information security? Give various potential scenarios where social media use might create personal or organizational security compromises.
- Some users regularly update their passwords by adding a number (say month or year) to their code. Why is this bad practice?
- What kind of features should a programmer build into systems in order to design for security? Think about the products that you use. Are there products that you feel did a good job of ensuring security during setup? Are there products you use that have demonstrated bad security design? How?
- Why are SQL injection attacks more difficult to address than the latest virus threat?
- How should individuals and firms leverage encryption?
- Investigate how you might use a VPN if traveling with your laptop. Be prepared to share your findings with your class and your instructor.




