This is “Peer Production, Social Media, and Web 2.0”, chapter 7 from the book Getting the Most Out of Information Systems: A Manager's Guide (v. 1.1). For details on it (including licensing), click here.
For more information on the source of this book, or why it is available for free, please see the project's home page. You can browse or download additional books there. To download a .zip file containing this book to use offline, simply click here.
Chapter 7 Peer Production, Social Media, and Web 2.0
7.1 Introduction
Learning Objectives
After studying this section you should be able to do the following:
- Recognize the unexpected rise and impact of social media and peer production systems, and understand how these services differ from prior generation tools.
- List the major classifications of social media services.
Over the past few years a fundamentally different class of Internet services has attracted users, made headlines, and increasingly garnered breathtaking market valuations. Often referred to under the umbrella term “Web 2.0A term broadly referring to Internet services that foster collaboration and information sharing; characteristics that distinctly set “Web 2.0” efforts apart from the static, transaction-oriented Web sites of “Web 1.0.” The term is often applied to Web sites and Internet services that foster social media or other sorts of peer production.,” these new services are targeted at harnessing the power of the Internet to empower users to collaborate, create resources, and share information in a distinctly different way from the static Web sites and transaction-focused storefronts that characterized so many failures in the dot-com bubble. Blogs, wikis, social networks, photo and video sharing sites, and tagging systems all fall under the Web 2.0 moniker, as do a host of supporting technologies and related efforts.
The term Web 2.0 is a tricky one because like so many popular technology terms there’s not a precise definition. Coined by publisher and pundit Tim O’Reilly in 2003, techies often joust over the breadth of the Web 2.0 umbrella and over whether Web 2.0 is something new or simply an extension of technologies that have existed since the creation of the Internet. These arguments aren’t really all that important. What is significant is how quickly the Web 2.0 revolution came about, how unexpected it was, and how deeply impactful these efforts have become. Some of the sites and services that have evolved and their Web 1.0 counterparts are listed in Table 7.1 "Web 1.0 versus Web 2.0".Adapted from T. O’Reilly, “What Is Web 2.0?” O’Reilly, September 30, 2005.
Table 7.1 Web 1.0 versus Web 2.0
| Web 1.0 | Web 2.0 | |
|---|---|---|
| DoubleClick | → | Google AdSense |
| Ofoto | → | Flickr |
| Akamai | → | BitTorrent |
| mp3.com | → | Napster |
| Britannica Online | → | Wikipedia |
| personal Web sites | → | blogging |
| evite | → | upcoming.org and Eventful |
| domain name speculation | → | search engine optimization |
| page views | → | cost per click |
| screen scraping | → | Web services |
| publishing | → | participation |
| content management systems | → | wikis |
| directories (taxonomy) | → | tagging (“folksonomy”) |
| stickiness | → | syndication |
| instant messaging | → | |
| Monster.com | → |
To underscore the speed with which Web 2.0 arrived on the scene, and the impact of leading Web 2.0 services, consider the following efforts:
- According to a spring 2008 report by Morgan Stanley, Web 2.0 services ranked as seven of the world’s top ten most heavily trafficked Internet sites (YouTube, Live.com, MySpace, Facebook, Hi5, Wikipedia, and Orkut); only one of these sites (MySpace) was on the list in 2005.Morgan Stanley, Internet Trends Report, March 2008.
- With only seven full-time employees and an operating budget of less than $1 million, Wikipedia has become the Internet’s fifth most visited site on the Internet.G. Kane and R. Fichman, “The Shoemaker’s Children: Using Wikis for Information Systems Teaching, Research, and Publication,” MIS Quarterly, March 2009. The site boasts well over fifteen million articles in over two hundred sixty different languages, all of them contributed, edited, and fact-checked by volunteers.
- Just two years after it was founded, MySpace was bought for $580 million by Rupert Murdoch’s News Corporation (the media giant that owns the Wall Street Journal and the Fox networks, among other properties). By the end of 2007, the site accounted for some 12 percent of Internet minutes and had repeatedly ranked as the most-visited Web site in the United States.D. Chmielewski and J. Guynn, “MySpace Ready to Prove Itself in Faceoff,” Chicago Tribune, June 8, 2008. But rapid rise doesn’t always mean a sustained following, and by the start of 2010, some were beginning to write the service’s obituary as it failed to keep pace with Facebook.O. Malik, “MySpace, R.I.P.,” GigaOM, February 10, 2010.
- The population of rival Facebook is now so large that it could be considered the third largest “nation” in the world. Half the site’s users log in at least once a day, spending an average of fifty-five minutes a day on the site.“Facebook Facts and Figures (History and Statistics),” Website Monitoring Blog, March 17, 2010. A fall 2007 investment from Microsoft pegged the firm’s overall value at $15 billion, a number that would have made it the fifth most valuable Internet firm, despite annual revenues at the time of only $150 million.M. Arrington, “Perspective: Facebook Is Now Fifth Most Valuable U.S. Internet Company,” TechCrunch, October 25, 2007. Those revenues have been growing, with the privately held firm expected to bring in from $1.2 to $2 billion in 2010.J. Vascellaro, “Facebook CEO in No Rush to ‘Friend’ Wall Street,” Wall Street Journal, March 3, 2010.
- Just twenty months after its founding, YouTube was purchased by Google for $1.65 billion. While Google struggles to figure out how to make profitable what is currently a money-losing resource hog (over twenty hours of video are uploaded to YouTube each minute)E. Nakashima, “YouTube Ordered to Release User Data,” Washington Post, July 4, 2008. the site has emerged as the Web’s leading destination for video, hosting everything from apologies from JetBlue’s CEO for service gaffes to questions submitted as part of the 2008 U.S. presidential debates. Fifty percent of YouTube’s roughly three hundred million users visit the site at least once a week.Morgan Stanley, Internet Trends Report, March 2008.
- Twitter has emerged as a major force that can break news and shape public opinion. China and Iran are among the governments so threatened by the power of Twitter-fueled data sharing that each has, at times, blocked Twitter access within their borders. At the first Twitter-focused Chirp conference in April 2010, Twitter boasted a population of over one hundred million users who have collectively posted more than ten billion tweets (Twitter messages). By this time, the service had also spawned an ecosystem of over one hundred thousand registered Twitter-supporting apps. In another nod to the service’s significance, the U.S. Library of Congress announced plans to archive every tweet ever sent.N. Bolton, “Chirp, Twitter’s First Developer Conference, Opens Its Doors,” New York Times, April 14, 2010; and M. Shaer, “Google Launches Archive Search for Twitter,” Christian Science Monitor, April 15, 2010.
- Services such as Twitter, Yelp, and the highly profitable TripAdvisor have unleashed the voice of the customer so that it is now often captured and broadcast immediately at the point of service. Reviews are now incorporated into search results and maps, making them the first thing many customers see when encountering a brand online. TripAdvisor, with just five hundred employees, contributes over $150 million in profits to parent company Expedia (at roughly 50 percent margins),B. Wash, “Double Duty,” Colby Magazine, Winter 2009. while Yelp has reportedly turned down acquisition offers valuing it at $700 million.P. Burrows, “Hot Tech Companies Like Yelp Are Bypassing IPOs,” BusinessWeek, February 4, 2010.
Table 7.2 Major Social Media Tools
| Description | Features | Technology Providers | Use Case Examples | |
|---|---|---|---|---|
| Blogs | Short for “Web log”—an online diary that keeps a running chronology of entries. Readers can comment on posts. Can connect to other blogs through blog rolls or trackbacks. Key uses: Share ideas, obtain feedback, mobilize a community. |
|
|
|
| Wikis | A Web site that anyone can edit directly from within the browser. Key uses: Collaborate on common tasks or to create a common knowledge base. |
|
|
|
| Electronic Social Network | Online community that allows users to establish a personal profile, link to other profiles (i.e., friends), share content, and communicate with members via messaging, posts. Key Uses: Discover and reinforce affiliations; identify experts; message individuals or groups; virally share media. |
|
|
|
| Microblogging | Short, asynchronous messaging system. Users send messages to “followers.” Key Uses: distribute time-sensitive information, share opinions, virally spread ideas, run contests and promotions, solicit feedback, provide customer support, track commentary on firms/products/issues, organize protests. |
|
|
|
Millions of users, billions of dollars, huge social impact, and these efforts weren’t even on the radar of most business professionals when today’s graduating college seniors first enrolled as freshmen. The trend demonstrates that even some of the world’s preeminent thought leaders and business publications can be sideswiped by the speed of the Internet.
Consider that when management guru Michael Porter wrote a piece titled “Strategy and the Internet” at the end of the dot-com bubble, he lamented the high cost of building brand online, questioned the power of network effects, and cast a skeptical eye on ad-supported revenue models. Well, it turns out Web 2.0 efforts challenged all of these concerns. Among the efforts above, all built brand on the cheap with little conventional advertising, and each owes their hypergrowth and high valuation to their ability to harness the network effect.
While the Web 2.0 moniker is a murky one, we’ll add some precision to our discussion of these efforts by focusing on peer productionWhen users collaboratively work to create content, products, and services. Includes social media sites, open source software, and peer-produced services, such as Skype and BitTorrent, where the participation of users provide the infrastructure and computational resources that enable the service., perhaps Web 2.0’s most powerful feature, where users work, often collaboratively, to create content and provide services online. Web-based efforts that foster peer production are often referred to as social mediaContent that is created, shared, and commented on by a broader community of users. Services that support the production and sharing of social media include blogs, wikis, video sites like YouTube, and social networks. or user-generated content sites. These sites include blogs; wikis; social networks like Facebook and MySpace; communal bookmarking and tagging sites like Del.icio.us; media sharing sites like YouTube and Flickr; and a host of supporting technologies. And it’s not just about media. Peer-produced services like Skype and BitTorrent leverage users’ computers instead of a central IT resource to forward phone calls and video. This ability saves their sponsors the substantial cost of servers, storage, and bandwidth. Peer production is also leveraged to create much of the open source software that supports many of the Web 2.0 efforts described above. Techniques such as crowdsourcing, where initially undefined groups of users band together to solve problems, create code, and develop services, are also a type of peer production. These efforts often seek to leverage the so-called wisdom of crowds, the idea that a large, diverse group often has more collective insight than a single or small group of trained professionals. These efforts will be expanded on below, along with several examples of their use and impact.
Key Takeaways
- A new generation of Internet applications is enabling consumers to participate in creating content and services online. Examples include Web 2.0 efforts such as social networks, blogs, and wikis, as well as efforts such as Skype and BitTorrent, which leverage the collective hardware of their user communities to provide a service.
- These efforts have grown rapidly, most with remarkably little investment in promotion. Nearly all of these new efforts leverage network effects to add value and establish their dominance and viral marketing to build awareness and attract users.
- Experts often argue whether Web 2.0 is something new or merely an extension of existing technologies. The bottom line is the magnitude of the impact of the current generation of services.
- Peer production and social media fall under the Web 2.0 umbrella. These services often leverage the wisdom of crowds to provide insight or production that can be far more accurate or valuable than that provided by a smaller group of professionals.
- Network effects play a leading role in enabling Web 2.0 firms. Many of these services also rely on ad-supported revenue models.
Questions and Exercises
- What distinguishes Web 2.0 technologies and services from the prior generation of Internet sites?
- Several examples of rapidly rising Web 2.0 efforts are listed in this section. Can you think of other dramatic examples? Are there cautionary tales of efforts that may not have lived up to their initial hype or promise? Why do you suppose they failed?
- Make your own list of Web 1.0 and Web 2.0 services and technologies. Would you invest in them? Why or why not?
- In what ways do Web 2.0 efforts challenge the assumptions that Michael Porter made regarding Strategy and the Internet?
7.2 Blogs
Learning Objectives
After studying this section you should be able to do the following:
- Know what blogs are and how corporations, executives, individuals, and the media use them.
- Understand the benefits and risks of blogging.
- Appreciate the growth in the number of blogs, their influence, and their capacity to generate revenue.
BlogsOnline journal entries, usually made in a reverse chronological order. Blogs typically provide comment mechanisms where users can post feedback for authors and other readers. (short for Web logs) first emerged almost a decade ago as a medium for posting online diaries. (In a perhaps apocryphal story, Wired magazine claimed the term “Web log” was coined by Jorn Barger, a sometimes homeless, yet profoundly prolific, Internet poster). From humble beginnings, the blogging phenomenon has grown to a point where the number of public blogs tracked by Technorati (the popular blog index) has surpassed one hundred million.D. Takahashi, “Technorati Releases Data on State of the Blogosphere: Bloggers of the World Have United,” VentureBeat, September 28, 2008. This number is clearly a long tailIn this context, refers to an extremely large selection of content or products. The long tail is a phenomenon whereby firms can make money by offering a near-limitless selection. phenomenon, loaded with niche content that remains “discoverable” through search engines and blog indexes. TrackbacksLinks in a blog post that refer eaders back to cited sources. Trackbacks allow a blogger to see which and how many other bloggers are referring to their content. A “trackback” field is supported by most blog software and while it’s not required to enter a trackback when citing another post, it’s considered good “netiquette” to do so. (third-party links back to original blog post), and blog rollsA list of a blogger’s favorite blogs. While not all blogs include blog rolls, those that do are often displayed on the right or left column of a blog’s main page. (a list of a blogger’s favorite sites—a sort of shout-out to blogging peers) also help distinguish and reinforce the reputation of widely read blogs.
The most popular blogs offer cutting-edge news and commentary, with postings running the gamut from professional publications to personal diaries. While this cacophony of content was once dismissed, blogging is now a respected and influential medium. Some might say that many of the most popular blogs have grown beyond the term, transforming into robust media enterprises. Consider that the political blog The Huffington Post is now more popular than all but eight newspaper sites and has a valuation higher than many publicly traded papers.E. Alterman, “Out of Print, the Death and Life of the American Newspaper,” New Yorker, March 31, 2008; and M. Learmonth, “Huffington Post More Valuable Than Some Newspaper Cos.,” DigitalNext, December 1, 2008. Keep in mind that this is a site without the sports, local news, weather, and other content offered by most papers. Ratings like this are hard to achieve—most bloggers can’t make a living off their musings. But among the elite ranks, killer subscriber numbers are a magnet for advertisers. Top blogs operating on shoestring budgets can snare several hundred thousand dollars a month in ad revenue.S. Zuckerman, “Yes, Some Blogs Are Profitable—Very Profitable,” San Francisco Chronicle, October 21, 2007. Most start with ad networks like Google AdSense, but the most elite engage advertisers directly for high-value deals and extended sponsorships.
Top blogs have begun to attract well-known journalists away from print media. The Huffington Post hired a former Washington Post editor Lawrence Roberts to head the site’s investigative unit. The popular blog TechCrunch now features posts by Sarah Lacy (a BusinessWeek cover-story writer) and has hired Erick Schonfeld away from Time Warner’s business publishing empire. Schonfeld’s colleague, Om Malik, has gone on to found another highly ranked tech industry blog, GigaOM.
Senior executives from many industries have also begun to weigh in with online ruminations, going directly to the people without a journalist filtering their comments. Hotel chief Bill Marriott, Paul Levy (CEO of health care quality leader Beth Israel Deaconess Medical Center), Toyota’s Akio Toyoda, and Zappos’ CEO Tony Hsieh use their blogs for purposes that include a combination of marketing, sharing ideas, gathering feedback, press response, image shaping, and reaching consumers directly without press filtering. Blogs have the luxury of being more topically focused than traditional media, with no limits on page size, word count, or publication deadline. Some of the best examples engage new developments in topic domains much more quickly and deeply than traditional media. For example, it’s not uncommon for blogs focused on the law or politics to provide a detailed dissection of a Supreme Court opinion within hours of its release—offering analysis well ahead of, and with greater depth, than via what bloggers call the mainstream media (MSM)Refers to newspapers, magazines, television, and radio. The MSM is distinctly different from Internet media such as blogs.. As such, it’s not surprising that most mainstream news outlets have begun supplementing their content with blogs that can offer greater depth, more detail, and deadline-free timeliness.
Blogs
While the feature set of a particular blog depends on the underlying platform and the preferences of the blogger, several key features are common to most blogs:
- Ease of use. Creating a new post usually involves clicking a single button.
- Reverse chronology. Posts are listed in reverse order of creation, making it easy to see the most recent content.
- Comment threads. Readers can offer comments on posts.
- Persistence. Posts are maintained indefinitely at locations accessible by permanent links.
- Searchability. Current and archived posts are easily searchable.
- Tags. Posts are often classified under an organized tagging scheme.
- Trackbacks. Allows an author to acknowledge the source of an item in their post, which allows bloggers to follow the popularity of their posts among other bloggers.
The voice of the blogosphereA term referring to the collective community of bloggers, as well as those who read and comment on blogs. can wield significant influence. Examples include leading the charge for Dan Rather’s resignation and prompting the design of a new insulin pump. In an example of what can happen when a firm ignores social media, consider the flare-up Ingersoll Rand faced when the online community exposed a design flaw in its Kryptonite bike lock.
Online posts showed the thick metal lock could be broken with a simple ball-point pen. A video showing the hack was posted online. When Ingersoll Rand failed to react quickly, the blogosphere erupted with criticism. Just days after online reports appeared, the mainstream media picked up the story. The New York Times ran a piece titled “The Pen Is Mightier Than the Lock” that included a series of photos demonstrating the ballpoint Kryptonite lock pick. The event tarnished the once-strong brand and eventually resulted in a loss of over $10 million.
Like any Web page, blogs can be public, tucked behind a corporate firewall, or password protected. Most blogs offer a two-way dialogue, allowing users to comment on posts (sort of instant “letters to the editor,” posted online and delivered directly to the author). The running dialogue can read like an electronic bulletin board, and can be an effective way to gather opinion when vetting ideas. Comments help keep a blogger honest. Just as the “wisdom of crowds” keeps Wikipedia accurate, a vigorous community of commenters will quickly expose a blogger’s errors of fact or logic.
Despite this increased popularity, blogging has its downside. Blog comments can be a hothouse for spam and the disgruntled. Ham-handed corporate efforts (such as poor response to public criticism or bogus “praise posts”) have been ridiculed. Employee blogging can be difficult to control and public postings can “live” forever in the bowels of an Internet search engine or as content pasted on other Web sites. Many firms have employee blogging and broader Internet posting policies to guide online conduct that may be linked to the firm (see Section 7.9 "Get SMART: The Social Media Awareness and Response Team"). Bloggers, beware—there are dozens of examples of workers who have been fired for what employers viewed as inappropriate posts.
Blogs can be hosted via third-party services (Google Blogger, WordPress, Tumblr, TypePad, Windows Live Spaces), with most offering a combination of free and premium features. Blogging features have also been incorporated into social networks such as Facebook, MySpace, and Ning, as well as corporate social media platforms such as Socialtext. Blogging software can also be run on third-party servers, allowing the developer more control in areas such as security and formatting. The most popular platform for users choosing to host their own blog server is the open source WordPress system.
In the end, the value of any particular blog derives from a combination of technical and social features. The technical features make it easy for a blogger and his or her community to engage in an ongoing conversation on some topic of shared interest. But the social norms and patterns of use that emerge over time in each blog are what determine whether technology features will be harnessed for good or ill. Some blogs develop norms of fairness, accuracy, proper attribution, quality writing, and good faith argumentation, and attract readers that find these norms attractive. Others mix it up with hotly contested debate, one-sided partisanship, or deliberately provocative posts, attracting a decidedly different type of discourse.
Key Takeaways
- Blogs provide a rapid way to distribute ideas and information from one writer to many readers.
- Ranking engines, trackbacks, and comments allow a blogger’s community of readers to spread the word on interesting posts and participate in the conversation, and help distinguish and reinforce the reputations of widely read blogs.
- Well-known blogs can be powerfully influential, acting as flashpoints on public opinion.
- Firms ignore influential bloggers at their peril, but organizations should also be cautious about how they use and engage blogs, and avoid flagrantly promotional or biased efforts.
- Top blogs have gained popularity, valuations, and profits that far exceed those of many leading traditional newspapers, and leading blogs have begun to attract well-known journalists away from print media.
- Senior executives from several industries use blogs for business purposes, including marketing, sharing ideas, gathering feedback, press response, image shaping, and reaching consumers directly without press filtering.
Questions and Exercises
- Visit Technorati and find out which blogs are currently the most popular. Why do you suppose the leaders are so popular?
- How are popular blogs discovered? How is their popularity reinforced?
- Are blog comment fields useful? If so, to whom or how? What is the risk associated with allowing users to comment on blog posts? How should a blogger deal with comments that they don’t agree with?
- Why would a corporation, an executive, a news outlet, or a college student want to blog? What are the benefits? What are the concerns?
- Identify firms and executives that are blogging online. Bring examples to class and be prepared to offer your critique of their efforts.
- How do bloggers make money? Do all bloggers have to make money? Do you think the profit motive influences their content?
- Investigate current U.S. Federal Trade Commission laws (or the laws in your home country) that govern bloggers and other social media use. How do these restrictions impact how firms interact with bloggers? What are the penalties and implications if such rules aren’t followed? Are there unwritten rules of good practice that firms and bloggers should consider as well? What might those be?
- According to your reading, how does the blog The Huffington Post compare with the popularity of newspaper Web sites?
- What advantage do blogs have over the MSM? What advantage does the MSM have over the most popular blogs?
- Start a blog using Blogger.com, WordPress.com, or some other blogging service. Post a comment to another blog. Look for the trackback field when making a post, and be sure to enter the trackback for any content you cite in your blog.
7.3 Wikis
Learning Objectives
After studying this section you should be able to do the following:
- Know what wikis are and how they are used by corporations and the public at large.
- Understand the technical and social features that drive effective and useful wikis.
- Suggest opportunities where wikis would be useful and consider under what circumstances their use may present risks.
- Recognize how social media such as wikis and blogs can influence a firm’s customers and brand.
A wikiA Web site that can be modified by anyone, from directly within a Web browser (provided that user is granted edit access). is a Web site anyone can edit directly within a Web browser (provided the site grants the user edit access). Wikis derive their name from the Hawaiian word for “quick.” Ward Cunningham, the “wiki father” christened this new class of software with the moniker in honor of the wiki-wiki shuttle bus at the Honolulu airport. Wikis can indeed be one of the speediest ways to collaboratively create content online. Many popular online wikis serve as a shared knowledge repository in some domain.
The largest and most popular wiki is Wikipedia, but there are hundreds of publicly accessible wikis that anyone can participate in. Each attempts to chronicle a world of knowledge within a particular domain, with examples ranging from Wine Wiki for oenophiles to Wookieepedia, the Star Wars wiki. But wikis can be used for any collaborative effort—from meeting planning to project management. And in addition to the hundreds of public wikis, there are many thousand more that are hidden away behind firewalls, used as proprietary internal tools for organizational collaboration.
Like blogs, the value of a wiki derives from both technical and social features. The technology makes it easy to create, edit, and refine content; learn when content has been changed, how and by whom; and to change content back to a prior state. But it is the social motivations of individuals (to make a contribution, to share knowledge) that allow these features to be harnessed. The larger and more active a wiki community, the more likely it is that content will be up-to-date and that errors will be quickly corrected (again, we see the influence of network effects, where products and services with larger user bases become more valuable). Several studies have shown that large community wiki entries are as or more accurate than professional publication counterparts.S. Robert Lichter, Are Chemicals Killing Us? Statistical Assessment Service, May 21, 2009; J. Kane, R. Fichman, J. Gallaugher, and J. Glaser, “Community Relations 2.0,” Harvard Business Review, November 2009.
Want to add to or edit a wiki entry? On most sites you just click the “Edit” link. Wikis support what you see is what you get (WYSIWYG)A phrase used to describe graphical editing tools, such as those found in a wiki, page layout program, or other design tool. editing that, while not as robust as traditional word processors, is still easy enough for most users to grasp without training or knowledge of arcane code or markup language. Users can make changes to existing content and can easily create new pages or articles and link them to other pages in the wiki. Wikis also provide a version history. Click the “History” link on Wikipedia, for example, and you can see when edits were made and by whom. This feature allows the community to roll backThe ability to revert a wiki page to a prior version. This is useful for restoring earlier work in the event of a posting error, inaccuracy, or vandalism. a wiki to a prior page, in the event that someone accidentally deletes key info, or intentionally defaces a page.
Vandalism is a problem on Wikipedia, but it’s more of a nuisance than a crisis. A Wired article chronicled how Wikipedia’s entry for former U.S. President Jimmy Carter was regularly replaced by a photo of a “scruffy, random unshaven man with his left index finger shoved firmly up his nose.”D. Pink, “The Book Stops Here,” Wired, March 2005. Nasty and inappropriate, to be sure, but the Wikipedia editorial community is now so large and so vigilant that most vandalism is caught and corrected within seconds. Watch-lists for the most active targets (say the Web pages of political figures or controversial topics) tip off the community when changes are made. The accounts of vandals can be suspended, and while mischief-makers can log in under another name, most vandals simply become discouraged and move on. It’s as if an army of do-gooders follows a graffiti tagger and immediately repaints any defacement.
Wikis
As with blogs, a wiki’s features set varies depending on the specific wiki tool chosen, as well as administrator design, but most wikis support the following key features:
- All changes are attributed, so others can see who made a given edit.
- A complete revision history is maintained so changes can be compared against prior versions and rolled back as needed.
- There is automatic notification and monitoring of updates; users subscribe to wiki content and can receive updates via e-mail or RSS feed when pages have been changed or new content has been added.
- All the pages in a wiki are searchable.
- Specific wiki pages can be classified under an organized tagging scheme.
Wikis are available both as software (commercial as well as open source varieties) that firms can install on their own computers or as online services (both subscription or ad-supported) where content is hosted off-site by third parties. Since wikis can be started without the oversight or involvement of a firm’s IT department, their appearance in organizations often comes from grassroots user initiative. Many wiki services offer additional tools such as blogs, message boards, or spreadsheets as part of their feature set, making most wikis really more full-featured platforms for social computing.
Jump-starting a wiki can be a challenge, and an underused wiki can be a ghost town of orphan, out-of-date, and inaccurate content. Fortunately, once users see the value of wikis, use and effectiveness often snowballs. The unstructured nature of wikis are also both a strength and weakness. Some organizations employ wikimastersIndividuals often employed by organizations to review community content in order to delete excessive posts, move commentary to the best location, and edit as necessary. to “garden” community content; “prune” excessive posts, “transplant” commentary to the best location, and “weed” as necessary. Wikipatterns.com offers a guide to the stages of wiki adoption and a collection of community-building and content-building strategies.
Examples of Wiki Use
Wikis can be vital tools for collecting and leveraging knowledge that would otherwise be scattered throughout an organization; reducing geographic distance; removing boundaries between functional areas; and flattening preexisting hierarchies. Companies have used wikis in a number of ways:
- At Pixar, all product meetings have an associated wiki to improve productivity. The online agenda ensures that all attendees can arrive knowing the topics and issues to be covered. Anyone attending the meeting (and even those who can’t make it) can update the agenda, post supporting materials, and make comments to streamline and focus in-person efforts.
- At European investment bank Dresdner Kleinwort Wasserstein, employees use wikis for everything from setting meeting agendas to building multimedia training for new hires. Six months after launch, wiki use had surpassed activity on the firm’s established intranet. Wikis are also credited with helping to reduce Dresdner e-mail traffic by 75 percent.D. Carlin, “Corporate Wikis Go Viral,” BusinessWeek, March 12, 2007.
- Sony’s PlayStation team uses wikis to regularly maintain one-page overviews on the status of various projects. In this way, legal, marketing, and finance staff can get quick, up-to-date status reports on relevant projects, including the latest projected deadlines, action items, and benchmark progress. Strong security measures are enforced that limit access to only those who must be in the know, since the overviews often discuss products that have not been released.
- Employees at investment-advisory firm Manning and Napier use a wiki to collaboratively track news in areas of critical interest. Providing central repositories for employees to share articles and update evolving summaries on topics such as health care legislation, enables the firm to collect and focus what would otherwise be fragmented findings and insight. Now all employees can refer to central pages that each serve as a lightning rod attracting the latest and most relevant findings.
- Intellipedia is a secure wiki built on Intelink, a U.S. government system connecting sixteen spy agencies, military organizations, and the Department of State. The wiki is a “magnum opus of espionage,” handling some one hundred thousand user accounts and five thousand page edits a day. Access is classified in tiers as “unclassified,” “secret,” and “top secret” (the latter hosting 439,387 pages and 57,248 user accounts). A page on the Mumbai terror attacks was up within minutes of the event, while a set of field instructions relating to the use of chlorine-based terror bombs in Iraq was posted and refined within two days of material identification—with the document edited by twenty-three users at eighteen locations.M. Calabrese, “Wikipedia for Spies: The CIA Discovers Web 2.0,” Time, April 8, 2009.
When brought outside the firewall, corporate wikis can also be a sort of value-generation greenhouse, allowing organizations to leverage input from their customers and partners:
- Intuit has created a “community wiki” that encourages the sharing of experience and knowledge not just regarding Intuit products, such as QuickBooks, but also across broader topics its customers may be interested in, such as industry-specific issues (e.g., architecture, nonprofit) or small business tips (e.g., hiring and training employees). The TurboTax maker has also sponsored TaxAlmanac.org, a wiki-based tax resource and research community.
- Microsoft leveraged its customer base to supplement documentation for its Visual Studio software development tool. The firm was able to enter the Brazilian market with Visual Studio in part because users had created product documentation in Portuguese.R. King, “No Rest for the Wiki,” BusinessWeek, March 12, 2007.
- ABC and CBS have created public wikis for the television programs Lost, The Amazing Race, and CSI, among others, offering an outlet for fans, and a way for new viewers to catch up on character backgrounds and complex plot lines.
- Executive Travel, owned by American Express Publishing, has created a travel wiki for its more than one hundred and thirty thousand readers with the goal of creating what it refers to as “a digital mosaic that in theory is more authoritative, comprehensive, and useful” than comments on a Web site, and far more up-to-date than any paper-based travel guide.R. King, “No Rest for the Wiki,” BusinessWeek, March 12, 2007. Of course, one challenge in running such a corporate effort is that there may be a competing public effort already in place. Wikitravel.org currently holds the top spot among travel-based wikis, and network effects suggest it will likely grow and remain more current than rival efforts.
Don’t Underestimate the Power of Wikipedia
Not only is the nonprofit Wikipedia, with its enthusiastic army of unpaid experts and editors, replacing the three-hundred-year reference reign of Encyclopedia Britannica, Wikipedia entries can impact nearly all large-sized organizations. Wikipedia is the go-to, first-choice reference site for a generation of “netizens,” and Wikipedia entries are invariably one of the top links, often the first link, to appear in Internet search results.
This position means that anyone from top executives to political candidates to any firm large enough to warrant an entry has to contend with the very public commentary offered up in a Wikipedia entry. In the same way that firms monitor their online reputations in blog posts and Twitter tweets, they’ve also got to keep an eye on wikis.
But firms that overreach and try to influence an entry outside of Wikipedia’s mandated neutral point of view (NPOV)An editorial style that is free of bias and opinion. Wikipedia norms dictate that all articles must be written in NPOV., risk a backlash and public exposure. Version tracking means the wiki sees all. Users on computers at right-leaning Fox News were embarrassingly caught editing the wiki page of the lefty pundit and politician Al Franken (a nemesis of Fox’s Bill O’Reilly);A. Bergman, “Wikipedia Is Only as Anonymous as your I.P.,” O’Reilly Radar, August 14, 2007. Sony staffers were flagged as editing the entry for the Xbox game Halo 3;I. Williams, “Sony Caught Editing Halo 3 Wikipedia Entry,” Vnunet.com, September 5, 2007. and none other than Wikipedia founder Jimmy Wales was criticized for editing his own Wikipedia biographyE. Hansen, “Wikipedia Founder Edits Own Bio,” Wired, December 19, 2005.—acts that some consider bad online form at best, and dishonest at worst.
One last point on using Wikipedia for research. Remember that according to its own stated policies, Wikipedia isn’t an original information source; rather, it’s a clearinghouse for verified information. So citing Wikipedia as a reference usually isn’t considered good form. Instead, seek out original (and verifiable) sources, such as those presented via the links at the bottom of Wikipedia entries.
Key Takeaways
- Wikis can be powerful tools for many-to-many content collaboration, and can be ideal for creating resources that benefit from the input of many such as encyclopedia entries, meeting agendas, and project status documents.
- The greater the number of wiki users, the more likely the information contained in the wiki will be accurate and grow in value.
- Wikis can be public or private.
- The availability of free or low-cost wiki tools can create a knowledge clearinghouse on topics, firms, products, and even individuals. Organizations can seek to harness the collective intelligence (wisdom of crowds) of online communities. The openness of wikis also acts as a mechanism for promoting organizational transparency and accountability.
Questions and Exercises
- Visit a wiki, either an established site like Wikipedia, or a wiki service like Socialtext. Make an edit to a wiki entry or use a wiki service to create a new wiki for your own use (e.g., for a class team to use in managing a group project). Be prepared to share your experience with the class.
- What factors determine the value of a wiki? Which key concept, first introduced in Chapter 2 "Strategy and Technology: Concepts and Frameworks for Understanding What Separates Winners from Losers", drives a wiki’s success?
- If anyone can edit a wiki, why aren’t more sites crippled by vandalism or by inaccurate or inappropriate content? Are there technical reasons not to be concerned? Are there “social” reasons that can alleviate concern?
- Give examples of corporate wiki use, as well as examples where firms used wikis to engage their customers or partners. What is the potential payoff of these efforts? Are there risks associated with these efforts?
- Do you feel that you can trust content in wikis? Do you feel this content is more or less reliable than content in print encyclopedias? Than the content in newspaper articles? Why?
- Have you ever run across an error in a wiki entry? Describe the situation.
- Is it ethical for a firm or individual to edit their own Wikipedia entry? Under what circumstances would editing a Wikipedia entry seem unethical to you? Why? What are the risks a firm or individual is exposed to when making edits to public wiki entries? How do you suppose individuals and organizations are identified when making wiki edits?
- Would you cite Wikipedia as a reference when writing a paper? Why or why not?
7.4 Electronic Social Networks
Learning Objectives
After studying this section you should be able to do the following:
- Know what social networks are, be able to list key features, and understand how they are used by individuals, groups, and corporations.
- Understand the difference between major social networks MySpace, Facebook, and LinkedIn.
- Recognize the benefits and risks of using social networks.
- Be aware of trends that may influence the evolution of social networks.
Social networksAn online community that allows users to establish a personal profile and communicate with others. Large public social networks include MySpace, Facebook, LinkedIn, and Google’s Orkut. have garnered increasing attention as established networks grow and innovate, new networks emerge, and value is demonstrated. MySpace signed a billion-dollar deal to carry ads from Google’s AdSense network. Meanwhile, privately held Facebook has blown past the flagging MySpace. Its leadership in privacy management, offering new features, allowing third-party applications on its platform, and providing sophisticated analytics tools to corporations and other on-site sponsors have helped the firm move beyond its college roots. LinkedIn, which rounds out the big three U.S. public social networks, has grown to the point where its influence is threatening recruiting sites like Monster.com and CareerBuilder.M. Boyle, “Recruiting: Enough to Make a Monster Tremble,” BusinessWeek, June 25, 2009. It now offers services for messaging, information sharing, and even integration with the BusinessWeek Web site.
Media reports often mention MySpace, Facebook, and LinkedIn in the same sentence. However, while these networks share some common features, they serve very different purposes. MySpace pages are largely for public consumption. Started by musicians, MySpace casts itself as a media discovery tool bringing together users with similar tastes.B. Johnson, “MySpace Bosses Battle to Oust Facebook from Social Networking Top Spot,” The Guardian, March 15, 2010.
Facebook, by contrast, is more oriented towards reinforcing existing social ties between people who already know each other. This difference leads to varying usage patterns. Since Facebook is perceived by users as relatively secure, with only invited “friends” seeing your profile, over a third of Facebook users post their mobile phone numbers on their profile pages.
LinkedIn was conceived from the start as a social network for business users. The site’s profiles act as a sort of digital Rolodex that users update as they move or change jobs. Users can pose questions to members of their network, engage in group discussions, ask for introductions through mutual contacts, and comment on others’ profiles (e.g., recommending a member). Active members find the site invaluable for maintaining professional contacts, seeking peer advice, networking, and even recruiting. Carmen Hudson, Starbucks manager of enterprise staffing, states LinkedIn is “one of the best things for finding midlevel executives.”R. King, “No Rest for the Wiki,” BusinessWeek, March 12, 2007. Such networks are also putting increasing pressure on firms to work particularly hard to retain top talent. While once HR managers fiercely guarded employee directories for fear that a list of talent may fall into the hands of rivals, today’s social networks make it easy for anyone to gain a list of a firm’s staff, complete with contact information.
While these networks dominate in the United States, the network effect and cultural differences work to create islands where other social networks are favored by a particular culture or region. The first site to gain traction in a given market is usually the winner. Google’s Orkut, Mixi, and Cyworld have small U.S. followings, but are among the largest sites in Brazil, Japan, and South Korea. Research by Ipsos Insight also suggests that users in many global markets, including Brazil, South Korea, and China, are more active social networkers than their U.S. counterparts.Ipsos Insights, Online Video and Social Networking Web Sites Set to Drive the Evolution of Tomorrow’s Digital Lifestyle Globally, July 5, 2007.
Perhaps the most powerful (and controversial) feature of most social networks is the feedAn update on an individual’s activities that are broadcast to a member’s contacts or “friends.” Feeds may include activities such as posting messages, photos, or video, joining groups, or installing applications. (or newsfeed). Pioneered by Facebook but now adopted by most services, feeds provide a timely update on the activities of people or topics that an individual has an association with. Feeds can give you a heads-up when someone makes a friend, joins a group, posts a photo, or installs an application.
Feeds are inherently viralIn this context, information or applications that spread rapidly between users.. By seeing what others are doing on a social network, feeds can rapidly mobilize populations and dramatically spread the adoption of applications. Leveraging feeds, it took just ten days for the Facebook group Support the Monks’ Protest in Burma to amass over one hundred and sixty thousand Facebook members. Feeds also helped music app iLike garner three million Facebook users just two weeks after its launch.S. Lacy, Once You’re Lucky, Twice You’re Good: The Rebirth of Silicon Valley and the Rise of Web 2.0 (New York: Gotham Books, 2008); and K. Nicole, “iLike Sees Exponential Growth with Facebook App,” Mashable, June 11, 2007. Its previous Web-based effort took eight months to reach those numbers.
But feeds are also controversial. Many users react negatively to this sort of public broadcast of their online activity, and feed mismanagement can create public relations snafus, user discontent, and potentially open up a site to legal action. Facebook initially dealt with a massive user outcry at the launch of feeds, and faced a subsequent backlash when its Beacon service broadcast user purchases without first explicitly asking their permission, and during attempts to rework its privacy policy and make Facebook data more public and accessible. (See Chapter 8 "Facebook: Building a Business from the Social Graph" for more details.)
Social Networks
The foundation of a social network is the user profile, but utility goes beyond the sort of listing found in a corporate information directory. Typical features of a social network include support for the following:
- Detailed personal profiles
- Affiliations with groups, such as alumni, employers, hobbies, fans, health conditions)
- Affiliations with individuals (e.g., specific “friends”)
- Private messaging and public discussions
- Media sharing (text, photos, video)
- Discovery-fueling feeds of recent activity among members (e.g., status changes, new postings, photos, applications installed)
- The ability to install and use third-party applications tailored to the service (games, media viewers, survey tools, etc.), many of which are also social and allow others to interact
Corporate Use of Social Networks
Hundreds of firms have established “fan” pages on Facebook and communites on LinkedIn. These are now legitimate customer- and client-engagement platforms that also support advertising. If a customer has decided to press the “like” button of a firm’s Facebook page and become a “fan,” corporate information will appear in their newsfeed, gaining more user attention than the often-ignored ads that run on the sides of social networks. (For more on social networks and advertising, see Chapter 8 "Facebook: Building a Business from the Social Graph".)
But social networks have also become organizational productivity tools. Many employees have organized groups using publicly available social networking sites because similar tools are not offered by their firms. Workforce Management reported that MySpace had over forty thousand groups devoted to companies or coworkers, while Facebook had over eight thousand.E. Frauenheim, “Social Revolution,” Workforce Management, October 2007. Assuming a large fraction of these groups are focused on internal projects, this demonstrates a clear pent-up demand for corporate-centric social networks (and creates issues as work dialogue moves outside firm-supported services).
Many firms are choosing to meet this demand by implementing internal social network platforms that are secure and tailored to firm needs. At the most basic level, these networks have supplanted the traditional employee directory. Social network listings are easy to update and expand. Employees are encouraged to add their own photos, interests, and expertise to create a living digital identity.
Firms such as Deloitte, Dow Chemical, and Goldman Sachs have created social networks for “alumni” who have left the firm or retired. These networks can be useful in maintaining contacts for future business leads, rehiring former employees (20 percent of Deloitte’s experienced hires are so-called boomerangs, or returning employees), or recruiting retired staff to serve as contractors when labor is tight.R. King, “Social Networks: Execs Use Them Too,” BusinessWeek, November 11, 2006. Maintaining such networks will be critical in industries like IT and health care that are likely to be plagued by worker shortages for years to come.
Social networking can also be important for organizations like IBM, where some 42 percent of employees regularly work from home or client locations. IBM’s social network makes it easier to locate employee expertise within the firm, organize virtual work groups, and communicate across large distances.W. Bulkley, “Playing Well with Others,” Wall Street Journal, June 18, 2007. As a dialogue catalyst, a social network transforms the public directory into a font of knowledge sharing that promotes organization flattening and value-adding expertise sharing.
While IBM has developed their own social network platforms, firms are increasingly turning to third-party vendors like SelectMinds (adopted by Deloitte, Dow Chemical, and Goldman Sachs) and LiveWorld (adopted by Intuit, eBay, the NBA, and Scientific American). Ning allows anyone to create a social network and currently hosts over 2.3 million separate online communities.K. Swisher, “Ning CEO Gina Bianchini to Step Down—Becomes an EIR at Andreessen Horowitz,” AllThingsD, March 15, 2010.
A Little Too Public?
As with any type of social media, content flows in social networks are difficult to control. Embarrassing disclosures can emerge from public systems or insecure internal networks. Employees embracing a culture of digital sharing may err and release confidential or proprietary information. Networks could serve as a focal point for the disgruntled (imagine the activity on a corporate social network after a painful layoff). Publicly declared affiliations, political or religious views, excessive contact, declined participation, and other factors might lead to awkward or strained employee relationships. Users may not want to add a coworker as a friend on a public network if it means they’ll expose their activities, lives, persona, photos, sense of humor, and friends as they exist outside of work. And many firms fear wasted time as employees surf the musings and photos of their peers.
All are advised to be cautious in their social media sharing. Employers are trawling the Internet, mining Facebook, and scouring YouTube for any tip-off that a would-be hire should be passed over. A word to the wise: those Facebook party pics, YouTube videos of open mic performances, or blog postings from a particularly militant period might not age well and may haunt you forever in a Google search. Think twice before clicking the upload button! As Socialnomics author Erik Qualman puts it, “What happens in Vegas stays on YouTube (and Flickr, Twitter, Facebook…).”
Firms have also created their own online communities to foster brainstorming and customer engagement. Dell’s IdeaStorm.com forum collects user feedback and is credited with prompting line offerings, such as the firm’s introduction of a Linux-based laptop.D. Greenfield, “How Companies Are Using I.T. to Spot Innovative Ideas,” InformationWeek, November 8, 2008. At MyStarbucksIdea.com, the coffee giant has leveraged user input to launch a series of innovations ranging from splash sticks that prevent spills in to-go cups, to new menu items. Both IdeaStorm and MyStarbucksIdea run on a platform offered by Salesforce.com that not only hosts these sites but also provides integration into Facebook and other services. Starbucks (the corporate brand with the most Facebook “fans”) has extensively leveraged the site, using Facebook as a linchpin in the “Free Pastry Day” promotion (credited with generating one million in-store visits in a single day) and promotion of the firm’s AIDS-related (Starbucks) RED campaign, which garnered an astonishing three hundred ninety million “viral impressions” through feeds, wall posts, and other messaging.M. Brandau, “Starbucks Brews Up Spot on the List of Top Social Brands in 2008,” Nation’s Restaurant News, April 6, 2009.
Social Networks and Health Care
Dr. Daniel Palestrant often shows a gruesome slide that provides a powerful anecdote for Sermo, the social network for physicians that he cofounded and where he serves as CEO. The image is of an eight-inch saw blade poking through both sides of the bloodied thumb of a construction worker who’d recently arrived in a hospital emergency room. A photo of the incident was posted to Sermo, along with an inquiry on how to remove the blade without damaging tissue or risking a severed nerve. Within minutes replies started coming back. While many replies advised to get a hand surgeon, one novel approach suggested cutting a straw lengthwise, inserting it under the teeth of the blade, and sliding the protected blade out while minimizing further tissue tears.M. Schulder, “50on50: Saw Blade through Thumb. What Would You Do?” CNN, November 4, 2009. The example illustrates how doctors using tools like Sermo can tap into the wisdom of crowds to save thumbs and a whole lot more.
Sermo is a godsend to remote physicians looking to gain peer opinion on confounding cases or other medical questions. The American Medical Association endorsed the site early on,The AMA and Sermo have since broken ties; see B. Comer, “Sermo and AMA Break Ties,” Medical Marketing and Media, July 9, 2009. and the Nature scientific journals have included a “Discuss on Sermo” button alongside the online versions of their medical articles. Doctors are screened and verified to maintain the integrity of participants. Members leverage the site both to share information with each other and to engage in learning opportunities provided by pharmaceutical companies and other firms. Institutional investors also pay for special access to poll Sermo doctors on key questions, such as opinions on pending FDA drug approval. Sermo posts can send valuable warning signals on issues such as disease outbreaks or unseen drug side effects. And doctors have also used the service to rally against insurance company policy changes.
While Sermo focuses on the provider side of the health care equation, a short walk from the firm’s Cambridge, Massachusetts, headquarters will bring one to PatientsLikeMe (PLM), a social network empowering chronically ill patients across a wide variety of disease states. The firm’s “openness policy” is in contrast to privacy rules posted on many sites and encourages patients to publicly track and post conditions, treatments, and symptom variation over time, using the site’s sophisticated graphing and charting tools. The goal is to help others improve the quality of their own care by harnessing the wisdom of crowds.
Todd Small, a multiple sclerosis sufferer, used the member charts and data on PLM to discover that his physician had been undermedicating him. After sharing site data with his doctor, his physician verified the problem and upped the dose. Small reports that the finding changed his life, helping him walk better than he had in a decade and a half and eliminating a feeling that he described as being trapped in “quicksand.”T. Goetz, “Practicing Patients,” New York Times Magazine, March 23, 2008. In another example of PLM’s people power, the site ran its own clinical trial–like experiment to rapidly investigate promising claims that the drug Lithium could improve conditions for ALS (amyotrophic lateral sclerosis) patients. While community efforts did not support these initial claims, a decision was arrived at in months, whereas previous efforts to marshal researchers and resources to focus on the relatively rare disease would have taken many years, even if funding could be found.J. Kane, R. Fichman, J. Gallaugher, and J. Glaser, “Community Relations 2.0,” Harvard Business Review, November 2009.
Both Sermo and PatientsLikeMe are start-ups that are still exploring the best way to fund their efforts for growth and impact. Regardless of where these firms end up, it should be clear from these examples that social media will remain a powerful force on the health care landscape.
Key Takeaways
- Electronic social networks help individuals maintain contacts, discover and engage people with common interests, share updates, and organize as groups.
- Modern social networks are major messaging services, supporting private one-to-one notes, public postings, and broadcast updates or “feeds.”
- Social networks also raise some of the strongest privacy concerns, as status updates, past messages, photos, and other content linger, even as a user’s online behavior and network of contacts changes.
- Network effects and cultural differences result in one social network being favored over others in a particular culture or region.
- Information spreads virally via news feeds. Feeds can rapidly mobilize populations, and dramatically spread the adoption of applications. The flow of content in social networks is also difficult to control and sometimes results in embarrassing public disclosures.
- Feeds have a downside and there have been instances where feed mismanagement has caused user discontent, public relations problems, and the possibility of legal action.
- The use of public social networks within private organizations is growing, and many organizations are implementing their own, private, social networks.
- Firms are also setting up social networks for customer engagement and mining these sites for customer ideas, innovation, and feedback.
Questions and Exercises
- Visit the major social networks (MySpace, Facebook, LinkedIn). What distinguishes one from the other? Are you a member of any of these services? Why or why not?
- How are organizations like Deloitte, Goldman Sachs, and IBM using social networks? What advantages do they gain from these systems?
- What factors might cause an individual, employee, or firm to be cautious in their use of social networks?
- How do you feel about the feed feature common in social networks like Facebook? What risks does a firm expose itself to if it leverages feeds? How might a firm mitigate these kinds of risks?
- What sorts of restrictions or guidelines should firms place on the use of social networks or the other Web 2.0 tools discussed in this chapter? Are these tools a threat to security? Can they tarnish a firm’s reputation? Can they enhance a firm’s reputation? How so?
- Why do information and applications spread so quickly within networks like Facebook? What feature enables this? What key promotional concept (described in Chapter 2 "Strategy and Technology: Concepts and Frameworks for Understanding What Separates Winners from Losers") does this feature foster?
- Why are some social networks more popular in some nations than others?
- Investigate social networks on your own. Look for examples of their use for fostering political and social movements; for their use in health care, among doctors, patients, and physicians; and for their use among other professional groups or enthusiasts. Identify how these networks might be used effectively, and also look for any potential risks or downside. How are these efforts supported? Is there a clear revenue model, and do you find these methods appropriate or potentially controversial? Be prepared to share your findings with your class.
7.5 Twitter and the Rise of Microblogging
Learning Objectives
After studying this section you should be able to do the following:
- Appreciate the rapid rise of Twitter—its scale, scope, and broad appeal.
- Understand how Twitter is being used by individuals, organizations, and political movements.
- Contrast Twitter and microblogging with Facebook, conventional blogs, and other Web 2.0 efforts.
- Consider the commercial viability of the effort, its competitive environment, and concerns regarding limited revenue.
Spawned in 2006 as a side project at the now-failed podcasting start-up Odeo (an effort backed by Blogger.com founder Evan Williams), Twitter has been on a rocket ride. The site’s user numbers have blasted past both mainstream and new media sites, dwarfing New York Times, LinkedIn, and Digg, among others. Reports surfaced of rebuffed buyout offers as high as $500 million.S. Ante, “Facebook’s Thiel Explains Failed Twitter Takeover,” BusinessWeek, March 1, 2009. By the firm’s first developer conference in April 2010, Twitter and its staff of 175 employees had created a global phenomenon embraced by over one hundred million users worldwide.
Twitter is a microbloggingA type of short-message blogging, often made via mobile device. Microblogs are designed to provide rapid notification to their readership (e.g., a news flash, an update on one’s activities), rather than detailed or in-depth comments. Twitter is the most popular microblogging service. service that allows users to post 140-character messages (tweetsA Twitter post, limited to 140 characters.) via the Web, SMSA text messaging standard used by many mobile phones., or a variety of third-party desktop and smartphone applications. The microblog moniker is a bit of a misnomer. The service actually has more in common with Facebook’s status updates and news feeds than it does with traditional blogs. But unlike Facebook, where most users must approve “friends” before they can see status updates, Twitter’s default setting allows for asymmetrical following (although it is possible to set up private Twitter accounts and to block followers).
Sure, there’s a lot of inane “tweeting” going on—lots of meaningless updates that read, “I’m having a sandwich” or “in line at the airport.” But while not every user may have something worthwhile to tweet, many find that Twitter makes for invaluable reading, offering a sense of what friends, customers, thought leaders, and newsmakers are thinking. Twitter leadership has described the service as communicating “The Pulse of the Planet.”E. Schonfeld, “Twitter's Internal Strategy Laid Bare: To Be ‘The Pulse of The Planet,’” TechCrunch, July 19, 2009. For many, Twitter is a discovery engine, a taste-making machine, a critical source of market intelligence, a source of breaking news, and an instantaneous way to plug into the moment’s zeitgeist.
Many also find Twitter to be an effective tool for quickly blasting queries to friends, colleagues, or strangers who might offer potentially valuable input. Says futurist Paul Saffo, “Instead of creating the group you want, you send it and the group self-assembles.”C. Miller, “Putting Twitter’s World to Use,” New York Times, April 13, 2009. Users can classify comments on a given topic using hash tagsA method for organizing tweets where keywords are preceeded by the # character. (keywords preceded by the “#” or “hash” symbol), allowing others to quickly find related tweets (e.g., #iranelection, #mumbai, #swineflu, #sxsw). Any user can create a hash tag—just type it into your tweet (you may want to search Twitter first to make sure that the tag is not in use by an unrelated topic and that if it is in use, it appropriately describes how you want your tweet classified).
Twitter users have broken news during disasters, terror attacks, and other major events. Dictators fear the people power Twitter enables, and totalitarian governments worldwide have moved to block citizen access to the service (prompting Twitter to work on censor-evading technology). During the 2009 Iranian election protests, the U.S. State Department even asked Twitter to postpone maintenance to ensure the service would continue to be available to support the voice and activism of Iran’s democracy advocates.C. Ruffini, “State Dept. Asked Twitter to Delay Maintenance,” CBS News, June 16, 2009.
Twitter is also emerging as a legitimate business tool. Consider the following commercial examples:
- Starbucks uses Twitter in a variety of ways. It has run Twitter-based contests and used the service to spread free samples of new products, such as its VIA instant coffee line. Twitter has also been a way for the company to engage customers in its cause-based marketing efforts, such as (Starbucks) RED, which supports (Product) RED. Starbucks has even recruited staff via Twitter and was one of the first firms to participate in Twitter’s advertising model featuring “promoted tweets.”
- Dell used Twitter to uncover an early warning sign indicating poor design of the keyboard on its Mini 9 Netbook PC. After a series of tweets from early adopters indicated that the apostrophe and return keys were positioned too closely together, the firm dispatched design change orders quickly enough to correct the problem when the Mini 10 was launched just three months later. By December 2009, Dell also claimed to have netted $6.5 million in outlet store sales referred via the Twitter account @DellOutlet (more than 1.5 million followers)K. Eaton, “Twitter Really Works: Makes $6.5 Million in Sales for Dell,” Fast Company, December 8, 2009. and another $1 million from customers who have bounced from the outlet to the new products site.J. Abel, “Dude—Dell’s Making Money Off Twitter!” Wired News, June 12, 2009.
- Brooklyn Museum patrons can pay an additional $20 a year for access to the private, members-only “1stFans” Twitter feed that shares information on special events and exclusive access to artist content.
- Twitter is credited with having raised millions via Text-to-Donate and other fundraising efforts following the Haiti earthquake.
- Twitter can be a boon for sharing time-sensitive information. The True Massage and Wellness Spa in San Francisco tweets last-minute cancellations to tell customers of an unexpected schedule opening. With Twitter, appointments remain booked solid. Gourmet food trucks, popular in many American cities, are also using Twitter to share location and create hipster buzz. Los Angeles’s Kogi Korean Taco Truck now has over sixty thousand followers and uses Twitter to reveal where it’s parked, ensuring long lines of BBQ-craving foodies. Of the firm’s success, owner Roy Choi says, “I have to give all the credit to Twitter.”A. Romano, “Now 4 Restaurant 2.0,” Newsweek, February 28, 2009.
- Electronics retailer Best Buy has recruited over 2,300 Blue Shirt and Geek Squad staffers to crowdsource Twitter-driven inquiries via @Twelpforce, the firm’s customer service Twitter account. Best Buy staffers register their personal Twitter accounts on a separate Best Buy–run site. Then any registered employees tweeting using the #twelpforce, will automatically have those posts echoed through @Twelpforce, with the employee’s account credited at the end of the tweet. As of November 2009, Twelpforce had provided answers to over 19,500 customer inquiries.Twitter.com, “Case Study: Best Buy Twelpforce,” Twitter 101, http://business.twitter.com/twitter101/case_bestbuy.
Figure 7.1 A Sampling of Tweets Filtered through Best Buy’s @Twelpforce Twitter Account

Surgeons and residents at Henry Ford Hospital have even tweeted during brain surgery (the teaching hospital sees the service as an educational tool). Some tweets are from those so young they’ve got “negative age.” Twitter.com/kickbee is an experimental fetal monitor band that sends tweets when motion is detected: “I kicked Mommy at 08:52.” And savvy hackers are embedding “tweeting” sensors into all sorts of devices. Botanicalls, for example, offers an electronic flowerpot stick that detects when plants need care and sends Twitter status updates to owners (sample post: “URGENT! Water me!”).
Organizations are well advised to monitor Twitter activity related to the firm, as it can act as a sort of canary-in-a-coal mine uncovering emerging events. Users are increasingly using the service as a way to form flash protest crowds. Amazon.com, for example, was caught off guard over a spring 2009 holiday weekend when thousands used Twitter to rapidly protest the firm’s reclassification of gay and lesbian books (hash tag #amazonfail). Others use the platform for shame and ridicule. BP has endured withering ridicule from the satire account @BPGlobalPR (followed by roughly 200,000 two months after the spill).
For all the excitement, many wonder if Twitter is overhyped. Some reports suggest that many Twitter users are curious experimenters who drop the service shortly after signing up.D. Martin, “Update: Return of the Twitter Quitters,” Nielsen Wire, April 30, 2009. This raises the question of whether Twitter is a durable phenomenon or just a fad.
Pundits also wonder if revenues will ever justify initially high valuations and if rivals could usurp Twitter’s efforts with similar features. Thus far, Twitter has been following a “grow-first-harvest-later” approach.J. Murrell, “Twitter Treads Gently into Advertising Minefield,” San Jose Mercury News, April 13, 2010. The site’s rapid rise has allowed it to attract enough start-up capital to enable it to approach revenue gradually and with caution, in the hopes that it won’t alienate users with too much advertising (an approach not unlike Google’s efforts to nurture YouTube). MIT’s Technology Review reports that data sharing deals with Google and Bing may have brought in enough money to make the service profitable in 2009, but that amount was modest (just $25 million).D. Talbot, “Can Twitter Make Money?” Technology Review, March/April 2010. Twitter’s advertising platform is expected to be far more lucrative. Reflecting Twitter’s “deliberately cautious” approach to revenue development, the ad model featuring sponsored ‘‘promoted tweets” rolled out first as part of the search, with distribution to individual Twitter feeds progressing as the firm experiments and learns what works best for users and advertisers.
Another issue—many Twitter users rarely visit the site. Most active users post and read tweets using one of many—often free—applications provided by third parties, such as Seesmic, TweetDeck, and Twhirl. This happens because Twitter made its data available for free to other developers via API (application programming interface)Programming hooks, or guidelines, published by firms that tell other programs how to get a service to perform a task such as send or receive data. For example, Amazon.com provides APIs to let developers write their own applications and Websites that can send the firm orders.. Exposing data can be a good move as it spawned an ecosystem of over one hundred thousand complementary third-party products and services that enhance Twitter’s reach and usefulness (generating network effects from complementary offerings similar to other “platforms” like Windows, iPhone, and Facebook). There are potential downsides to such openness. If users don’t visit Twitter.com, that lessens the impact of any ads running on the site. This creates what is known as the “free rider problemWhen others take advantage of a user or service without providing any sort of reciprocal benefit.,” where users benefit from a service while offering no value in exchange. Encouraging software and service partners to accept ads for a percentage of the cut could lessen the free rider problem.P. Kafka, “Twitter’s Ad Plan: Copy Google,” AllThingsD, February 25, 2010.
When users don’t visit a service, it makes it difficult to spread awareness of new products and features. It can also create branding challenges and customer frustration. Twitter execs lamented that customers were often confused when they searched for “Twitter” in the iPhone App Store and were presented with scores of offerings but none from Twitter itself.D. Goldman, “Twitter Grows Up: Take a Peek Inside,” CNN, April 16, 2010. Twitter’s purchase of the iPhone app Tweetie (subsequently turned into the free “Twitter for iPhone” app) and the launch of its own URL-shortening service (competing with bit.ly and others) signal that Twitter is willing to move into product and service niches and compete with third parties that are reliant on the Twitter ecosystem.
Microblogging does appear to be here to stay, and the impact of Twitter has been deep, broad, stunningly swift, and at times humbling in the power that it wields. But whether Twitter will be a durable, profit-gushing powerhouse remains to be seen. Speculation on Twitter’s future hasn’t prevented many firms from commercializing new microblogging services, and a host of companies have targeted these tools for internal corporate use. Salesforce.com’s Chatter, Socialtext Signals, and Yammer are all services that have been billed as “Twitter for the Enterprise.” Such efforts allow for Twitter-style microblogging that is restricted for participation and viewing by firm-approved accounts.
Key Takeaways
- While many public and private microblogging services exist, Twitter remains by far the dominant service.
- Unlike status updates found on services like Facebook and LinkedIn, Twitter’s default supports asymmetric communication, where someone can follow updates without first getting their approval. This function makes Twitter a good choice for anyone cultivating a following—authors, celebrities, organizations, and brand promoters.
- You don’t need to tweet to get value. Many Twitter users follow friends, firms, celebrities, and thought leaders, quickly gaining access to trending topics.
- Twitter hash tags (keywords preceded by the # character) are used to organize “tweets” on a given topic. Users can search on hash tags, and many third-party applications allow for Tweets to be organized and displayed by tag.
- Firms are leveraging Twitter in a variety of ways, including: promotion, customer response, gathering feedback, and time-sensitive communication.
- Like other forms of social media, Twitter can serve as a hothouse that attracts opinion and forces organizational transparency and accountability.
- Activists have leveraged the service worldwide, and it has also served as an early warning mechanism in disasters, terror, and other events.
- Despite its rapid growth and impact, significant questions remain regarding the firm’s durability, revenue prospects, and enduring appeal to initial users.
- Twitter makes its data available to third parties via an API (application programming interface). The API has helped a rich ecosystem of over seventy thousand Twitter-supporting products and services emerge. But by making the Twitter stream available to third parties, Twitter may suffer from the free rider problem where others firms benefit from Twitter’s service without providing much benefit back to Twitter itself. New ad models may provide a way to distribute revenue-generating content through these services. Twitter has also begun acquiring firms that compete with other players in its ecosystem.
Questions and Exercises
- If you don’t already have one, set up a Twitter account and “follow” several others. Follow a diverse group—corporations, executives, pundits, or other organizations. Do you trust these account holders are who they say they are? Why? Which examples do you think use the service most effectively? Which provide the weaker examples of effective Twitter use? Why? Have you encountered Twitter “spam” or unwanted followers? What can you do to limit such experiences? Be prepared to discuss your experiences with class.
- If you haven’t done so, install a popular Twitter application such as TweetDeck, Seesmic, or a Twitter client for your mobile device. Why did you select the product you chose? What advantages does your choice offer over simply using Twitter’s Web page? What challenges do these clients offer Twitter? Does the client you chose have a clear revenue model? Is it backed by a viable business?
- Visit search.twitter.com. Which Twitter hash tags are most active at this time? Are there other “trending topics” that aren’t associated with hash tags? What do you think of the activity in these areas? Is there legitimate, productive activity happening? Search Twitter on topics, firms, brand names, and issues of interest to you. What do you think of the quality of the information you’ve uncovered on Twitter? Who might find this to be useful?
- Why would someone choose to use Twitter over Facebook’s status update, or other services? Which (if either) do you prefer and why?
- What do you think of Twitter’s revenue prospects? Is the firm a viable independent service or simply a feature to be incorporated into other social media activity? Advocate where you think the service will be in two years, five, ten. Would you invest in Twitter? Would you suggest that other firms do so? Why?
- Assume the role of a manager for your firm. Advocate how the organization should leverage Twitter and other forms of social media. Provide examples of effective use, and cautionary tales, to back up your recommendation.
- Some instructors have mandated Twitter for classroom use. Do you think this is productive? Would your professor advocate tweeting during lectures? What are the pros and cons of such use? Work with your instructor to discuss a set of common guidelines for in-class and course use of social media.
- As of this writing, Twitter was just rolling out advertising via “promoted tweets.” Perform some additional research. How have Twitter’s attempts to grow revenues fared? How has user growth been trending? Has the firm’s estimated value increased or decreased from the offer figures cited in this chapter? Why?
- What do you think of Twitter’s use of the API? What are the benefits of offering an API? What are the downsides? Would you create a company to take advantage of the Twitter API? Why or why not?
- Follow this book’s author at http://twitter.com/gallaugher. Tweet him if you run across interesting examples that you think would be appropriate for the next version of the book.
7.6 Other Key Web 2.0 Terms and Concepts
Learning Objectives
After studying this section you should be able to do the following:
- Know key terms related to social media, peer production, and Web 2.0, including RSS, folksonomies, mash-ups, location-based services, virtual worlds, and rich media.
- Provide examples of the effective business use of these terms and technologies.
RSS
RSSA method for sending/broadcasting data to users who subscribe to a service’s “RSS feed.” Many Web sites and blogs forward headlines to users who subscribe to their “feed,” making it easy to scan headlines and click to access relevant news and information. (an acronym that stands for both “really simple syndication” and “rich site summary”) enables busy users to scan the headlines of newly available content and click on an item’s title to view items of interest, thus sparing them from having to continually visit sites to find out what’s new. Users begin by subscribing to an RSS feed for a Web site, blog, podcast, or other data source. The title or headline of any new content will then show up in an RSS readerA tool for subscribing to and accessing RSS feeds. Most e-mail programs and Web browsers can also act as RSS readers. There are also many Web sites (including Google Reader) that allow users to subscribe to and read RSS feeds.. Subscribe to the New York Times Technology news feed, for example, and you will regularly receive headlines of tech news from the Times. Viewing an article of interest is as easy as clicking the title you like. Subscribing is often as easy as clicking on the RSS icon appearing on the home page of a Web site of interest.
Many firms use RSS feeds as a way to mange information overload, opting to distribute content via feed rather than e-mail. Some even distribute corporate reports via RSS. RSS readers are offered by third-party Web sites such as Google and Yahoo! and they have been incorporated into all popular browsers and most e-mail programs. Most blogging platforms provide a mechanism for bloggers to automatically publish a feed when each new post becomes available. Google’s FeedBurner is the largest publisher of RSS blog feeds, and offers features to distribute content via e-mail as well.
Figure 7.2
RSS readers like Google Reader can be an easy way to scan blog headlines and click through to follow interesting stories.
Figure 7.3

Web sites that support RSS feeds will have an icon in the address bar. Click it to subscribe.
Folksonomies
FolksonomiesKeyword-based classification systems created by user communities (also known as social tagging). (sometimes referred to as social tagging) are keyword-based classification systems created by user communities as they generate and review content. (The label is meant to refer to a people-powered taxonomy.) Bookmarking site Del.icio.us, photo-sharing site Flickr (both owned by Yahoo!), and Twitter’s hash tags all make heavy use of folksonomies.
With this approach, classification schemes emerge from the people most likely to understand them—the users. By leveraging the collective power of the community to identify and classify content, objects on the Internet become easier to locate, and content carries a degree of recommendation and endorsement.
Flickr cofounder Stewart Butterfield describes the spirit of folksonomies, saying, “The job of tags isn’t to organize all the world’s information into tidy categories, it’s to add value to the giant piles of data that are already out there.”D. Terdiman, “Folksonomies Tap People Power,” Wired, February 1, 2005. The Guggenheim Museum in New York City and the San Francisco Museum of Modern Art, among other museums, are taking a folksonomic approach to their online collections, allowing user-generated categories to supplement the specialized lexicon of curators. Amazon.com has introduced a system that allows readers to classify books, and most blog posts and wiki pages allow for social tagging, oftentimes with hot topics indexed and accessible via a “tag cloud” in the page’s sidebar.
Mash-up
Mash-upsThe combination of two or more technologies or data feeds into a single, integrated tool. are combinations of two or more technologies or data feeds into a single, integrated tool. Some of the best known mash-ups leverage Google’s mapping tools. HousingMaps.com combines Craigslist.org listings with Google Maps for a map-based display for apartment hunters. IBM linked together job feeds and Google Maps to create a job-seeker service for victims of Hurricane Katrina. SimplyHired links job listings with Google Maps, LinkedIn listings, and salary data from PayScale.com. And Salesforce.com has tools that allow data from its customer relationship management (CRM) system to be combined with data feeds and maps from third parties.
Mash-ups are made easy by a tagging system called XMLAbbreviation of Extensible Markup Language. A tagging language that can be used to identify data fields made available for use by other applications. For example, programmers may wrap XML tags around elements in an address data stream (e.g., 〈business name〉, 〈street address〉, 〈city〉, 〈state〉) to allow other programs to recognize and use these data items. (for extensible markup language). Site owners publish the parameters of XML data feeds that a service can accept or offer (e.g., an address, price, product descriptions, images). Other developers are free to leverage these public feeds using application programming interfaces (APIs), published instructions on how to make programs call one another, to share data, or to perform tasks. Using APIs and XML, mash-up authors smoosh together seemingly unrelated data sources and services in new and novel ways. Lightweight, browser-friendly software technologies like Ajax and HTML5 can often make a Web site interface as rich as a desktop application, and rapid deployment frameworks like Ruby on Rails will enable and accelerate mash-up creation and deployment.
Location-Based Services
Computing devices increasingly know where you are—and this is creating all sorts of new opportunities for social media. Twitter, Facebook, and Google Buzz are among the many social services that have added location-based options, allowing you to tweet or post a status update attached with a physical location as determined by your phone’s global positioning system (GPS)A network of satellites and supporting technologies used to identify a device’s physical location., triangulation from nearby cell phone towers, or proximity to neighboring Wi-Fi hotspots. This introduces a whole new way to gather and share information. In a new part of town and curious what folks are saying about the spot? Search for tweets tagged as being posted around that location.
Augmented-realityComputer applications that overlay real-world images with computer-generated imagery and data. apps can overlay real data on top of images from a GPS and compass-equipped smartphone. Swivel your iPhone around with Stella Artois’s Bar Finder app open, and it’ll point you to the nearest Stella-equipped watering hole (it’ll also let you text your friends to join you for a drink and call a cab for a safe ride home). Wikitude overlays images appearing through your phone’s camera lens with geotagged data from Wikipedia. Point your Yelp app down the street and activate the monocle feature to see starred reviews hover over the top of establishments that appear on screen.
Boston-based SCVNGR (pronounced “scavenger”), a gaming app, has allowed over four hundred clients, including Princeton, MetLife, and Boston’s Museum of Fine Arts, to create their own mobile phone-based scavenger hunts. The profitable firm has a 90 percent client return rate and had attracted funding from Google Ventures and Highland Capital Partners all before founder Seth Priebatsch turned twenty-one.J. Kincaid, “SCVNGR Raises $4 Million from Google Ventures,” TechCrunch, December 24, 2009.
Perhaps the best known among the location-based pure plays is Foursquare. The service allows players to “check in” at different locations, allowing players to earn “badges” displayed in the app for completing specific achievements (“gym rat” for exercise buffs, “school night” for weeknight bar hoppers). Check into a location more than anyone else and you become that spot’s “mayor.” Foursquare users can follow public location postings from their friends, discovering when someone’s close by and gaining recommendations on new places to explore. Foursquare grew to over one million users roughly one year after the service debuted at the 2009 South by Southwest conference. Firms are now using Foursquare for promotions and to support loyalty programs—offering “mayor specials” or sending out coupons and other incentives when users are nearby. Starbucks, the Bravo television channel, frozen yogurt chain Tasti D-Lite, and the Milwaukee-based burger chain AJ Bombers are among the diverse clients leveraging the service.
Figure 7.4 A Sampling of Location-Aware Apps

Wikitude shows Wikipedia overlays on top of images appearing through the viewfinder. Stella Artois’s Le Bar will point you to establishments offering the brew, and Foursquare offers vendor promotions as well as revealing nearby tweets.
Of course, all this public location sharing raises privacy concerns. The Web site PleaseRobMe.com was created to draw attention to the potentially dangerous issues around real-time location sharing. After a brief demonstration period, the site stopped its real-time aggregation of publicly accessible user-location data and now serves as an awareness site warning of the “stalkerish” side of location-based apps. In most cases, though, users remain firmly in control—determining if they want to keep a visit private or release their locale to verified “app friends” or to the broader online space.
Virtual Worlds
In virtual worldsA computer-generated environment where users present themselves in the form of an avatar, or animated character., users appear in a computer-generated environment in the form of an avatarAn online identity expressed by an animated or cartoon figure., or animated character. Users can customize the look of their avatar, interact with others by typing or voice chat, and can travel about the virtual world by flying, teleporting, or more conventional means.
The most popular general-purpose virtual world is Second Life by Linden Labs, although many others exist. Most are free, although game-oriented worlds, such as World of Warcarft (with ten million active subscribers), charge a fee. Many corporations and organizations have established virtual outposts by purchasing “land” in the world of Second Life, while still others have contracted with networks to create their own, independent virtual worlds.
Most organizations have struggled to commercialize these Second Life forays, but activity has been wide-ranging in its experimentation. Reuters temporarily “stationed” a reporter in Second Life, presidential candidates have made appearances in the virtual world, organizations ranging from Sun Microsystems to Armani have set up virtual storefronts, and there’s a significant amount of virtual mayhem. Second Life “terrorists” have “bombed” virtual outposts run by several organizations, including ABC News, American Apparel, and Reebok.
Even grade schoolers are heavy virtual world users. Many elementary school students get their first taste of the Web through Webkinz, an online world that allows for an animated accompaniment with each of the firm’s plush toys. Webkinz’s parent company, privately held Ganz, doesn’t release financial figures. But according to Compete.com, by the end of 2008 Webkinz.com had roughly the same number of unique visitors as FoxNews.com. The kiddie set virtual world market is considered so lucrative that Disney acquired ClubPenguin for $350 million with agreements to pay another potential three hundred fifty million if the effort hits growth incentives.B. Barnes, “Disney Acquires Web Site for Children,” New York Times, August 2, 2007.
YouTube, Podcasting, and Rich Media
Blogs, wikis, and social networks not only enable sharing text and photos, they also allow for the creation and distribution of audio and video. PodcastsDigital audio or video files served as a series of programs or a multimedia blog. are digital audio files (some also incorporate video), provided as a series of programs. Podcasts range from a sort of media blog, archives of traditional radio and television programs, and regular offerings of original online content. While the term podcast derives from Apple’s wildly successful iPod, podcasts can be recorded in audio formats such as MP3 that can be played on most portable media players. (In perhaps the ultimate concession to the market leader, even the iPod rival Microsoft Zune refers to serialized audio files as podcasts on its navigation menu).
There are many podcast directories, but Apple’s iTunes is by far the largest. Anyone who wants to make a podcast available on iTunes can do so for free. A podcast publisher simply records an audio file, uploads the file to a blog or other hosting server, then sends the RSS feed to Apple (copyrighted material cannot be used without permission, with violators risking banishment from iTunes). Files are discovered in the search feature of the iTunes music store, and listings seamlessly connect the user with the server hosting the podcast. This path creates the illusion that Apple serves the file even though it resides on a publisher’s servers.
While blogs have made stars of some unknowns, the most popular podcasts are from mainstream media outlets. A recent visit to the podcasting section of iTunes showed that eight of the top ten most popular podcasts were high-quality productions of mainstream media programs, including offerings from CBS, Comedy Central, NPR, and PBS. Podcasts are also revolutionizing education, with scores of universities “open sourcing” their classrooms and offering lectures for public consumption via Apple’s iTunesU.
In contrast to iTunes, YouTube actually hosts video on its own servers, so all you need to do is shoot a video and upload it to the site. YouTube is a bastion of amateur video, with most clips shot and uploaded by nonprofessionals. It’s also become a protest site (e.g., “A Comcast Technician Sleeping on my Couch”). However, YouTube has also become a go-to distribution platform for professional content such as ad clips, customer support guides, music videos, TV shows, movies, and more. Much of this rich mediaContent that is more complex than simple text. The term can refer to images, animation, audio, and video. content can be distributed or streamed within another Web site, blog, or social network profile.
Key Takeaways
- RSS fosters the rapid sharing and scanning of information, including updates from Web 2.0 services such as blogs, wikis, and social networks. RSS feeds can be received via Web browsers, e-mail, cell phones, and special RSS readers.
- Folksonomies allow users to collaboratively tag and curate online media, making it easy for others to find useful content. Since folksonomies are created by users themselves, they are often more easily understood and embraced than classification schemes imposed by site owners.
- Mash-ups promote the useful combination of different Web services, such as maps and other information feeds. Mash-up authors leverage technologies such as APIs and XML to combine seemingly unrelated data sources and services in new and novel ways.
- Location-based services are increasingly combining geolocated data with social media. Users can now quickly see related social media surrounding an area, even overlaying this data on top of maps and images through a phone’s camera lens. Sites like Foursquare are morphing into loyalty and customer-rewards programs. While users are largely in control of sharing location data, some fear privacy and security issues from oversharing.
- Virtual worlds allow users to interact with and within a computer-generated alternate reality.
- Internet media is increasingly becoming “richer,” leveraging audio, video, and animation. Organizations and users are creating and distributing rich media online, with interesting content spreading virally.
Questions and Exercises
- What is RSS and an RSS reader? Why would an individual use one? Why would a firm use RSS?
- Use an RSS reader like Google Reader, or the features built into your e-mail program or browser, and subscribe to RSS feeds. Discuss your experience with the class. Which feeds did you subscribe to? What did you like or not like about using an RSS reader?
- If you have a smartphone, download Foursquare or other location-based app. Is this service popular in your community? Research how firms are leveraging these tools for real business value.
- Investigate SCVNGR. Many schools are using the tool for orientation programs. Is your school using this? If so, participate in a SCVNGR game on campus. If not, build a case for considering SCVNGR (or similar service) and share this with your student government or student orientation office.
- Are privacy concerns from location-based apps valid? What can users do to be safe even while using location-based apps?
- Visit Second Life or another virtual world. Create an avatar and look for examples of corporate/commercial involvement. Be prepared to discuss your experience—both positive and negative.
- Investigate some of the many virtual worlds targeted at children, including Webkinz, Club Penguin, and Whyville. What are the revenue models for these efforts? How do these sites ensure they are safe for children? Assume the role of a parent—what are the pros and cons of these sites? Which (if any) would you allow your children to participate in? Why? Would you invest in any of these efforts or advise corporations to enter the kid-focused virtual world space? Why or why not?
- If you don’t already own it, download iTunes for free, go to the iTunes music store, and explore the free podcast section. Alternatively, find podcasts from another service. Which podcasts seem to be the most popular? Why? Do you use podcasts or other rich media? Why or why not?
- Visit YouTube. Identify examples of corporations using the service. Identify examples of customer use. Be prepared to discuss your findings with the class. Do you think Google is making much money with YouTube? Why or why not?
- Which firm do you think spends more on the technology infrastructure that powers its service—Apple with iTunes podcasts or Google with YouTube? Explain your answer.
- Why would a firm make its data available via XML to use as a mash-up? What can it gain? Are there any risks involved in providing programming hooks that allow the creation of mash-ups?
- Give examples of efforts that take advantage of folksonomies. Why are folksonomies considered to be useful?
- Do you spend time in rich media Web sites? Which ones? How much time do you or your friends spend on these sites? How would you describe the quality of rich media content found online?
- How might a firm use rich media online? What concerns does a firm or individual face with respect to rich media?
- Why do you suppose that the most popular podcasts come from established media firms (e.g., Comedy Central, NPR) rather than amateurs, while the top bloggers emerged outside the professional journalist/writer community?
7.7 Prediction Markets and the Wisdom of Crowds
Learning Objectives
After studying this section you should be able to do the following:
- Understand the concept of the wisdom of crowds as it applies to social networking.
- List the criteria necessary for a crowd to be smart.
Many social software efforts leverage what has come to be known as the wisdom of crowdsThe idea that a group of individuals (the crowd), often consisting of untrained amateurs, will collectively have more insight than a single or small group of trained professionals.. In this concept, a group of individuals (the crowd often consists mostly of untrained amateurs), collectively has more insight than a single or small group of trained professionals. Made popular by author James Surowiecki (whose best-selling book was named after the phenomenon), the idea of crowd wisdom is at the heart of wikis, folksonomy tagging systems, and many other online efforts. An article in the journal Nature positively comparing Wikipedia to Encyclopedia Britannica lent credence to social software’s use in harnessing and distilling crowd wisdom.J. Giles, “Special Report: Internet Encyclopedias Go Head to Head,” Nature 438, no. 15 (December 14, 2005): 900–901.
The crowd isn’t always right, but in many cases where topics are complex, problems are large, and outcomes are uncertain, a large, diverse group may bring collective insight to problem solving that one smart guy or a professional committee lacks. One technique for leveraging the wisdom of crowds is a prediction marketPolling a diverse crowd and aggregating opinions in order to form a forecast of an eventual outcome., where a diverse crowd is polled and opinions aggregated to form a forecast of an eventual outcome. The concept is not new. The stock market is arguably a prediction market, with a stock price representing collective assessment of the discounted value of a firm’s future earnings. But Internet technologies are allowing companies to set up prediction markets for exploring all sorts of problems.
Consider Best Buy, where employees are encouraged to leverage the firm’s TagTrade prediction market to make forecasts, and are offered small gifts as incentives for participation. The idea behind this incentive program is simple: the “blue shirts” (Best Buy employees) are closest to customers. They see traffic patterns and buying cycles, can witness customer reactions first hand, and often have a degree of field insight not available to senior managers at the company’s Minneapolis headquarters. Harness this collective input and you’ve got a group brain where, as wisdom of crowds proponents often put it, “the we is greater than the me.” When Best Buy asked its employees to predict gift card sales, the “crowd’s” collective average answer was 99.5 percent accurate; experts paid to make the prediction were off by 5 percent. Another experiment predicting holiday sales was off by only 1/10 of 1 percent. The experts? Off by 7 percent!P. Dvorak, “Best Buy Taps ‘Prediction Market,’” Wall Street Journal, September 16, 2008; and Renée Dye, “The Promise of Prediction Markets: A Roundtable,” McKinsey Quarterly (2008): 83–93.
In an article in the McKinsey Quarterly, Surowiecki outlined several criteria necessary for a crowd to be “smart.”R. Dye, “The Promise of Prediction Markets: A Roundtable,” McKinsey Quarterly (2008): 83–93. The crowd must
- be diverse, so that participants are bringing different pieces of information to the table,
- be decentralized, so that no one at the top is dictating the crowd’s answer,
- offer a collective verdict that summarizes participant opinions,
- be independent, so that each focuses on information rather than the opinions of others.
Google, which runs several predictive markets, underscored these principles when it found that predictions were less accurate when users were geographically proximate, meaning folks in the same work group who sat near one another typically thought too much alike.B. Cowgill, J. Wolfers, and E. Zitzewitz, “Using Prediction Markets to Track Information Flows: Evidence from Google,” working paper accessed November 30, 2009, via http://bocowgill.com/GooglePredictionMarketPaper.pdf. Poorer predictive outcomes likely resulted because these relatively homogeneous clusters of users brought the same information to the table (yet another reason why organizations should hire and cultivate diverse teams).
Many firms run predictive markets to aid in key forecasts, and with the potential for real financial payoff. But University of Chicago law professor Todd Henderson warns predictive markets may also hold legal and ethical challenges. The Securities and Exchange Commission may look askance at an employee who gets a heads-up in a predictive market that says a certain drug is going to be approved or fail clinical trials. If she trades on this information is she an insider, subject to prosecution for exploiting proprietary data? Disclosure issues are unclear. Gambling laws are also murky, with Henderson uncertain as to whether certain predictive markets will be viewed as an unregulated form of betting.R. Dye, “The Promise of Prediction Markets: A Roundtable,” McKinsey Quarterly 2 (2008): 83–93.
Publicly accessible prediction markets are diverse in their focus. The Iowa Electronic Market attempts to guess the outcome of political campaigns, with mixed results. Farecast (now part of Microsoft’s Bing knowledge engine) claims a 75 percent accuracy rate for forecasting the future price of airline tickets.“Audit Reveals Farecast Predictive Accuracy at 74.5 percent,” farecast.live.com, May 18, 2007, http://www.prnewswire.com/news-releases/farecast-launches-new-tools-to -help-savvy-travelers-catch-elusive-airfare-price-drops-this-summer-58165652.html. The Hollywood Stock Exchange allows participants to buy and sell prediction shares of movies, actors, directors, and film-related options. The exchange, now owned by investment firm Cantor Fitzgerald, has picked Oscar winners with 90 percent accuracy.J. Surowiecki, “Crowdsourcing the Crystal Ball,” Forbes, October 15, 2007. And at HedgeStreet.com, participants can make microbets, wagering as little as ten dollars on the outcome of economic events, including predictions on the prices of homes, gold, foreign currencies, oil, and even the economic impact of hurricanes and tropical storms. HedgeStreet is considered a market and is subject to oversight by the Commodity Futures Trading Commission.E. Lambert, “Hedging for Dummies,” Forbes, March 13, 2006, 70–72.
Key Takeaways
- Many Web 2.0 efforts allow firms to tap the wisdom of crowds, identifying collective intelligence.
- Prediction markets tap crowd opinion with results that are often more accurate than the most accurate expert forecasts and estimates.
- Prediction markets are most accurate when tapping the wisdom of a diverse and variously skilled and experienced group, and are least accurate when participants are highly similar.
Questions and Exercises
- What makes for a “wise” crowd? When might a crowd not be so wise?
- Find a prediction market online and participate in the effort. Be prepared to share your experience with your class, including any statistics of predictive accuracy, participant incentives, business model of the effort, and your general assessment of the appeal and usefulness of the effort.
- Brainstorm on the kinds of organizations that might deploy prediction markets. Why might you think the efforts you suggest and advocate would be successful?
- In what ways are legal issues of concern to prediction market operators?
7.8 Crowdsourcing
Learning Objectives
After studying this section you should be able to do the following:
- Understand the value of crowdsourcing.
- Identify firms that have used crowdsourcing successfully.
The power of Web 2.0 also offers several examples of the democratization of production and innovation. Need a problem solved? Offer it up to the crowd and see if any of their wisdom offers a decent result. This phenomenon, known as crowdsourcingThe act of taking a job traditionally performed by a designated agent (usually an employee) and outsourcing it to an undefined generally large group of people in the form of an open call., has been defined by Jeff Howe, founder of the blog crowdsourcing.com and an associate editor at Wired, as “the act of taking a job traditionally performed by a designated agent (usually an employee) and outsourcing it to an undefined, generally large group of people in the form of an open call.”J. Howe, “The Rise of Crowdsourcing,” Wired, June 2006.
Can the crowd really do better than experts inside a firm? At least one company has literally struck gold using crowdsourcing. As told by Don Tapscott and Anthony Williams in their book Wikinomics, mining firm Goldcorp was struggling to gain a return from its 55,000-acre Canadian property holdings. Executives were convinced there was gold “in them thar hills,” but despite years of efforts, the firm struggled to strike any new pay dirt. CEO Rob McEwen, a former mutual fund manager without geology experience who unexpectedly ended up running Goldcorp after a takeover battle, then made what seemed a Hail Mary pass—he offered up all the firm’s data, on the company’s Web site. Along with the data, McEwen ponied up $575,000 from the firm as prize money for the Goldcorp Challenge to anyone who came up with the best methods and estimates for reaping golden riches. Releasing data was seen as sacrilege in the intensely secretive mining industry, but it brought in ideas the firm had never considered. Taking the challenge was a wildly diverse group of “graduate students, consultants, mathematicians, and military officers.” Eighty percent of the new targets identified by entrants yielded “substantial quantities of gold.” The financial payoff? In just a few years a one-hundred-million-dollar firm grew into a nine-billion-dollar titan. For Goldcorp, the crowd coughed up serious coin.
Netflix followed Goldcorp’s lead, offering anonymous data to any takers, along with a one-million-dollar prize to the first team that could improve the accuracy of movie recommendations by 10 percent. Top performers among the over thirty thousand entrants included research scientists from AT&T Labs, researchers from the University of Toronto, a team of Princeton undergrads, and the proverbial “guy in a garage” (and yes, that was his team name). Frustrated for nearly three years, it took a coalition of four teams from Austria, Canada, Israel, and the United States to finally cross the 10 percent threshold. The winning team represented an astonishing brain trust that Netflix would never have been able to harness on its own.S. Lohr, “And the Winner of the $1 Million Netflix Prize (Probably) Is…” New York Times, June 26, 2009.
Other crowdsourcers include Threadless.com, which produces limited run t-shirts with designs users submit and vote on. Marketocracy runs stock market games and has created a mutual fund based on picks from the 100 top-performing portfolios. Just under seven years into the effort, the firm’s m100 Index reports a 75 percent return versus 35 percent for the S&P 500. The St. Louis Cardinals baseball team is even crowdsourcing. The club’s One for the Birds contest calls for the fans to submit scouting reports on promising players, as the team hopes to broaden its recruiting radar beyond its classic recruiting pool of Division I colleges.
There are several public markets for leveraging crowdsourcing for innovation, or as an alternative to standard means of production. Waltham, Massachusetts–based InnoCentive allows “seekers” to offer cash prizes ranging from ten to one hundred thousand dollars. Over one hundred twenty thousand “solvers” have registered to seek solutions for tasks put forward by seekers that include Dow Chemical, Eli Lilly, and Procter & Gamble. Among the findings offered by the InnoCentive crowd are a biomarker that measures progression of ALS. Amazon.com has even created an online marketplace for crowdsourcing called Mechanical Turk. Anyone with a task to be completed or problem to be solved can put it up for Amazon, setting their price for completion or solution. For its role, Amazon takes a small cut of the transaction. And alpha geeks looking to prove their code chops can turn to TopCoder, a firm that stages coding competitions that deliver real results for commercial clients such as ESPN. By 2009, TopCoder contests had attracted over 175,000 participants from 200 countries.M. Brandel, “Should Your Company ‘Crowdsource’ Its Next Project?” Computerworld, December 6, 2007; M. Brandel, “Crowdsourcing: Are You Ready to Ask the World for Answers?” Computerworld, March 3, 2008; and TopCoder, 2009, http://topcoder.com/home.
Not all crowdsourcers are financially motivated. Some benefit by helping to create a better service. Facebook leveraged crowd wisdom to develop versions of its site localized in various languages. Facebook engineers designated each of the site’s English words or phrases as a separate translatable object. Members were then invited to translate the English into other languages, and rated the translations to determine which was best. Using this form of crowdsourcing, fifteen hundred volunteers cranked out Spanish Facebook in a month. It took two weeks for two thousand German speakers to draft Deutsch Facebook. How does the Facebook concept of “poke” translate around the world? The Spaniards decided on “dar un toque,” Germans settled on “anklopfen,” and the French went with “envoyer un poke.”D. Kirkpatrick, “Help Wanted: Adults on Facebook,” Fortune, March 21, 2008. Vive le crowd!
Key Takeaways
- Crowdsourcing tackles challenges through an open call to a broader community of potential problem solvers. Examples include Goldcorp’s discovering of optimal mining locations in land it already held, Facebook’s leverage of its users to create translations of the site for various international markets, and Netflix’s solicitation of improvements to its movie recommendation software.
- Several firms run third-party crowdsourcing forums, among them InnoCentive for scientific R&D, TopCoder for programming tasks, and Amazon’s Mechanical Turk for general work.
Questions and Exercises
- What is crowdsourcing? Give examples of organizations that are taking advantage of crowdsourcing and be prepared to describe these efforts.
- What ethical issues should firms be aware of when considering crowdsourcing? Are there other concerns firms may have when leveraging this technique?
- Assume the role of a manager or consultant. Recommend a firm and a task that would be appropriate for crowdsourcing. Justify your choice, citing factors such as cost, breadth of innovation, time, constrained resources, or other factors. How would you recommend the firm conduct this crowdsourcing effort?
7.9 Get SMART: The Social Media Awareness and Response Team
Learning Objectives
After studying this section you should be able to do the following:
- Illustrate several examples of effective and poor social media use.
- Recognize the skills and issues involved in creating and staffing an effective social media awareness and response team (SMART).
- List and describe key components that should be included in any firm’s social media policy.
- Understand the implications of ethical issues in social media such as “sock puppetry” and “astroturfing” and provide examples and outcomes of firms and managers who used social media as a vehicle for dishonesty.
- List and describe tools for monitoring social media activity relating to a firm, its brands, and staff.
- Understand issues involved in establishing a social media presence, including the embassy approach, openness, and staffing.
- Discuss how firms can engage and respond through social media, and how companies should plan for potential issues and crises.
For an example of how outrage can go viral, consider Dave Carroll.The concepts in this section are based on work by J. Kane, R. Fichman, J. Gallaugher, and J. Glasser, many of which are covered in the article “Community Relations 2.0,” Harvard Business Review, November 2009. The Canadian singer-songwriter was traveling with his band Sons of Maxwell on a United Airlines flight from Nova Scotia to Nebraska when, during a layover at Chicago’s O’Hare International Airport, Carroll saw baggage handlers roughly tossing his guitar case. The musician’s $3,500 Taylor guitar was in pieces by the time it arrived in Omaha. In the midst of a busy tour schedule, Carroll didn’t have time to follow up on the incident until after United’s twenty-four-hour period for filing a complaint for restitution had expired. When United refused to compensate him for the damage, Carroll penned the four-minute country ditty “United Breaks Guitars,” performed it in a video, and uploaded the clip to YouTube (sample lyrics: “I should have gone with someone else or gone by car…’cuz United breaks guitars”). Carroll even called out the unyielding United rep by name. Take that, Ms. Irlwig! (Note to customer service reps everywhere: you’re always on.)
The clip went viral, receiving 150,000 views its first day and five million more by the next month. Well into the next year, “United Breaks Guitars” remained the top result on YouTube when searching the term “United.” No other topic mentioning that word—not “United States,” “United Nations,” or “Manchester United”—ranked ahead of this one customer’s outrage.
Video
(click to see video)Dave Carroll’s ode to his bad airline experience, “United Breaks Guitars,” went viral, garnering millions of views.
Scarring social media posts don’t just come from outside the firm. Earlier that same year employees of Domino’s Pizza outlet in Conover, North Carolina, created what they thought would be a funny gross-out video for their friends. Posted to YouTube, the resulting footage of the firm’s brand alongside vile acts of food prep was seen by over one million viewers before it was removed. Over 4.3 million references to the incident can be found on Google, and many of the leading print and broadcast outlets covered the story. The perpetrators were arrested, the Domino’s storefront where the incident occurred was closed, and the firm’s president made a painful apology (on YouTube, of course).
Not all firms choose to aggressively engage social media. As of this writing some major brands still lack a notable social media presence (Apple comes immediately to mind). But your customers are there and they’re talking about your organization, its products, and its competitors. Your employees are there, too, and without guidance, they can step on a social grenade with your firm left to pick out the shrapnel. Soon, nearly everyone will carry the Internet in their pocket. Phones and MP3 players are armed with video cameras capable of recording every customer outrage, corporate blunder, ethical lapse, and rogue employee. Social media posts can linger forever online, like a graffiti tag attached to your firm’s reputation. Get used to it—that genie isn’t going back in the bottle.
As the “United Breaks Guitars” and “Domino’s Gross Out” incidents show, social media will impact a firm whether it chooses to engage online or not. An awareness of the power of social media can shape customer support engagement and crisis response, and strong corporate policies on social media use might have given the clueless Domino’s pranksters a heads-up that their planned video would get them fired and arrested. Given the power of social media, it’s time for all firms to get SMARTThe social media awareness and response team. A group tasked with creating policies and providing support, training, guidance, and development expertise for and monitoring of a firm’s social media efforts., creating a social media awareness and response team. While one size doesn’t fit all, this section details key issues behind SMART capabilities, including creating the social media team, establishing firmwide policies, monitoring activity inside and outside the firm, establishing the social media presence, and managing social media engagement and response.
Creating the Team
Firms need to treat social media engagement as a key corporate function with clear and recognizable leadership within the organization. Social media is no longer an ad hoc side job or a task delegated to an intern. When McDonald’s named its first social media chief, the company announced that it was important to have someone “dedicated 100% of the time, rather than someone who’s got a day job on top of a day job.”E. York, “McDonald’s Names First Social-Media Chief,” Chicago Business, April 13, 2010. Firms without social media baked into employee job functions often find that their online efforts are started with enthusiasm, only to suffer under a lack of oversight and follow-through. One hotel operator found franchisees were quick to create Facebook pages, but many rarely monitored them. Customers later notified the firm that unmonitored hotel “fan” pages contained offensive messages—a racist rant on one, paternity claims against an employee on another.
Organizations with a clearly established leadership role for social media can help create consistency in firm dialogue; develop and communicate policy; create and share institutional knowledge; provide training, guidance, and suggestions; offer a place to escalate issues in the event of a crisis or opportunity; and catch conflicts that might arise if different divisions engage without coordination.
While firms are building social media responsibility into job descriptions, also recognize that social media is a team sport that requires input from staffers throughout an organization. The social media team needs support from public relations, marketing, customer support, HR, legal, IT, and other groups, all while acknowledging that what’s happening in the social media space is distinct from traditional roles in these disciplines. The team will hone unique skills in technology, analytics, and design, as well as skills for using social media for online conversations, listening, trust building, outreach, engagement, and response. As an example of the interdisciplinary nature of social media practice, consider that the social media team at Starbucks (regarded by some as the best in the business) is organized under the interdisciplinary “vice president of brand, content, and online.”Starbucks was named the best firm for social media engagement in a study by Altimeter Group and WetPaint. See the 2009 ENGAGEMENTdb report at http://engagementdb.com.
Also note that while organizations with SMARTs (social media teams) provide leadership, support, and guidance, they don’t necessarily drive all efforts. GM’s social media team includes representatives from all the major brands. The idea is that employees in the divisions are still the best to engage online once they’ve been trained and given operational guardrails. Says GM’s social media chief, “I can’t go in to Chevrolet and tell them ‘I know your story better than you do, let me tell it on the Web.’”C. Barger, talk at the Social Media Club of Detroit, November 18, 2009. Also available via UStream and DigitalMarketingZen.com. Similarly, the roughly fifty Starbucks “Idea Partners” who participate in MyStarbucksIdea are specialists. Part of their job is to manage the company’s social media. In this way, conversations about the Starbucks Card are handled by card team experts, and merchandise dialogue has a product specialist who knows that business best. Many firms find that the social media team is key for coordination and supervision (e.g., ensuring that different divisions don’t overload consumers with too much or inconsistent contact), but the dynamics of specific engagement still belong with the folks who know products, services, and customers best.
Responsibilities and Policy Setting
In an age where a generation has grown up posting shoot-from-the-hip status updates and YouTube is seen as a fame vehicle for those willing to perform sensational acts, establishing corporate policies and setting employee expectations are imperative for all organizations. The employees who don’t understand the impact of social media on the firm can do serious damage to their employers and their careers (look to Domino’s for an example of what can go wrong).
Many experts suggest that a good social media policy needs to be three things: “short, simple, and clear.”J. Soat, “7 Questions Key to Social Networking Success,” InformationWeek, January 16, 2010. Fortunately, most firms don’t have to reinvent the wheel. Several firms, including Best Buy, IBM, Intel, The American Red Cross, and Australian telecom giant Telstra, have made their social media policies public.
Most guidelines emphasize the “three Rs”: representation, responsibility, and respect.
- Representation. Employees need clear and explicit guidelines on expectations for social media engagement. Are they empowered to speak on behalf of the firm? If they do, it is critical that employees transparently disclose this to avoid legal action. U.S. Federal Trade Commission rules require disclosure of relationships that may influence online testimonial or endorsement. On top of this, many industries have additional compliance requirements (e.g., governing privacy in the health and insurance fields, retention of correspondence and disclosure for financial services firms). Firms may also want to provide guidelines on initiating and conducting dialogue, when to respond online, and how to escalate issues within the organization.
- Responsibility. Employees need to take responsibility for their online actions. Firms must set explicit expectations for disclosure, confidentiality and security, and provide examples of engagement done right, as well as what is unacceptable. An effective social voice is based on trust, so accuracy, transparency, and accountability must be emphasized. Consequences for violations should be clear.
- Respect. Best Buy’s policy for its Twelpforce explicitly states participants must “honor our differences” and “act ethically and responsibly.” Many employees can use the reminder. Sure customer service is a tough task and every rep has a story about an unreasonable client. But there’s a difference between letting off steam around the water cooler and venting online. Virgin Atlantic fired thirteen of the airline’s staffers after they posted passenger insults and inappropriate inside jokes on Facebook.L. Conway, “Virgin Atlantic Sacks 13 Staff for Calling Its Flyers ‘Chavs,’” The Independent, November 1, 2008.
Policies also need to have teeth. Remember, a fourth “R” is at stake—reputation (both the firm’s and the employee’s). Violators should know the consequences of breaking firm rules and policies should be backed by action. Best Buy’s policy simply states, “Just in case you are forgetful or ignore the guidelines above, here’s what could happen. You could get fired (and it’s embarrassing to lose your job for something that’s so easily avoided).”
Despite these concerns, trying to micromanage employee social media use is probably not the answer. At IBM, rules for online behavior are surprisingly open. The firm’s code of conduct reminds employees to remember privacy, respect, and confidentiality in all electronic communications. Anonymity is not permitted on IBM’s systems, making everyone accountable for their actions. As for external postings, the firm insists that employees not disparage competitors or reveal customers’ names without permission and asks that any employee posts from IBM accounts or that mention the firm also include disclosures indicating that opinions and thoughts shared publicly are the individual’s and not Big Blue’s.
Some firms have more complex social media management challenges. Consider hotels and restaurants where outlets are owned and operated by franchisees rather than the firm. McDonald’s social media team provides additional guidance so that regional operations can create, for example, a Twitter handle (e.g., @mcdonalds_cincy) that handle a promotion in Cincinnati that might not run in other regions.E. York, “McDonald’s Names First Social-Media Chief,” Chicago Business, April 13, 2010. A social media team can provide coordination while giving up the necessary control. Without this kind of coordination, customer communication can quickly become a mess.
Training is also a critical part of the SMART mandate. GM offers an intranet-delivered video course introducing newbies to the basics of social media and to firm policies and expectations. GM also trains employees to become “social media proselytizers and teachers.” GM hopes this approach enables experts to interact directly with customers and partners, allowing the firm to offer authentic and knowledgeable voices online.
Training should also cover information security and potential threats. Social media has become a magnet for phishing, virus distribution, and other nefarious online activity. Over one-third of social networking users claim to have been sent malware via social networking sites (see Chapter 13 "Information Security: Barbarians at the Gateway (and Just About Everywhere Else)"). The social media team will need to monitor threats and spread the word on how employees can surf safe and surf smart.
Since social media is so public, it’s easy to amass examples of what works and what doesn’t, adding these to the firm’s training materials. The social media team provides a catch point for institutional knowledge and industry best practice; and the team can update programs over time as new issues, guidelines, technologies, and legislation emerge.
The social media space introduces a tension between allowing expression (among employees and by the broader community) and protecting the brand. Firms will fall closer to one end or the other of this continuum depending on compliance requirements, comfort level, and goals. Expect the organization’s position to move. Firms will be cautious as negative issues erupt, others will jump in as new technologies become hot and early movers generate buzz and demonstrate results. But it’s the SMART responsibility to avoid knee-jerk reaction and to shepherd firm efforts with the professionalism and discipline of other management domains.
Astroturfing and Sock Puppets
Social media can be a cruel space. Sharp-tongued comments can shred a firm’s reputation and staff might be tempted to make anonymous posts defending or promoting the firm. Don’t do it! Not only is it a violation of FTC rules, IP addresses and other online breadcrumbs often leave a trail that exposes deceit.
Whole Foods CEO John Mackey fell victim to this kind of temptation, but his actions were eventually, and quite embarrassingly, uncovered. For years, Mackey used a pseudonym to contribute to online message boards, talking up Whole Foods stock and disparaging competitors. When Mackey was unmasked, years of comments were publicly attributed to him. The New York Times cited one particularly cringe-worthy post where Mackey used the pseudonym to complement his own good looks, writing, “I like Mackey’s haircut. I think he looks cute!”A. Martin, “Whole Foods Executive Used Alias,” New York Times, July 12, 2007.
Fake personas set up to sing your own praises are known as sock puppetsA fake online persona created to promote a particular point of view, often in praise of a firm, product, or individual. Be aware that the use of undisclosed relationships in endorsements is a violation of U.S. Federal Trade Comission rules. among the digerati, and the practice of lining comment and feedback forums with positive feedback is known as astroturfingEngineering the posting of positive comments and reviews of a firm’s product and services (or negative ones of a firm’s competitors). Many ratings sites will penalize firms that offer incentives for positive feedback posts.. Do it and it could cost you. The firm behind the cosmetic procedure known as the Lifestyle Lift was fined $300,000 in civil penalties after the New York Attorney General’s office discovered that the firm’s employees had posed as plastic surgery patients and wrote glowing reviews of the procedure.C. Cain Miller, “Company Settles Case of Reviews It Faked,” July 14, 2009.
Review sites themselves will also take action. TripAdvisor penalizes firms if it’s discovered that customers are offered some sort of incentive for posting positive reviews. The firm also employs a series of sophisticated automated techniques as well as manual staff review to uncover suspicious activity. Violators risk penalties that include being banned from the service.
Your customers will also use social media keep you honest. Several ski resorts have been embarrassed when tweets and other social media posts exposed them as overstating snowfall results. There’s even an iPhone app skiers can use to expose inaccurate claims.L. Rathke, “Report: Ski Resorts Exaggerate Snowfall Totals,” USA Today, January 29, 2010.
So keep that ethical bar high—you never know when technology will get sophisticated enough to reveal wrongdoings.
Monitoring
Concern over managing a firm’s online image has led to the rise of an industry known as online reputation managementThe process of tracking and responding to online mentions of a product, organization, or individual. Services supporting online reputation management range from free Google Alerts to more sophisticated services that blend computer-based and human monitoring of multiple media channels.. Firms specializing in this field will track a client firm’s name, brand, executives’ names, or other keywords, reporting online activity and whether sentiment trends toward the positive or negative.
But social media monitoring is about more than about managing one’s reputation; it also provides critical competitive intelligence, it can surface customer support issues, and it can uncover opportunities for innovation and improvement. Firms that are quick to lament the very public conversations about their brands happening online need to embrace social media as an opportunity to learn more.
Resources for monitoring social media are improving all the time, and a number of tools are available for free. All firms can take advantage of Google Alerts, which flag blog posts, new Web pages, and other publicly accessible content, regularly delivering a summary of new links to your mailbox (for more on using Google for intelligence gathering, see Chapter 14 "Google: Search, Online Advertising, and Beyond"). Twitter search and third-party Twitter clients like TweetDeck can display all mentions of a particular term. Tools like Twitrratr will summarize mentions of a phrase and attempt to classify tweets as “positive,” “neutral,” or “negative.”
Figure 7.5
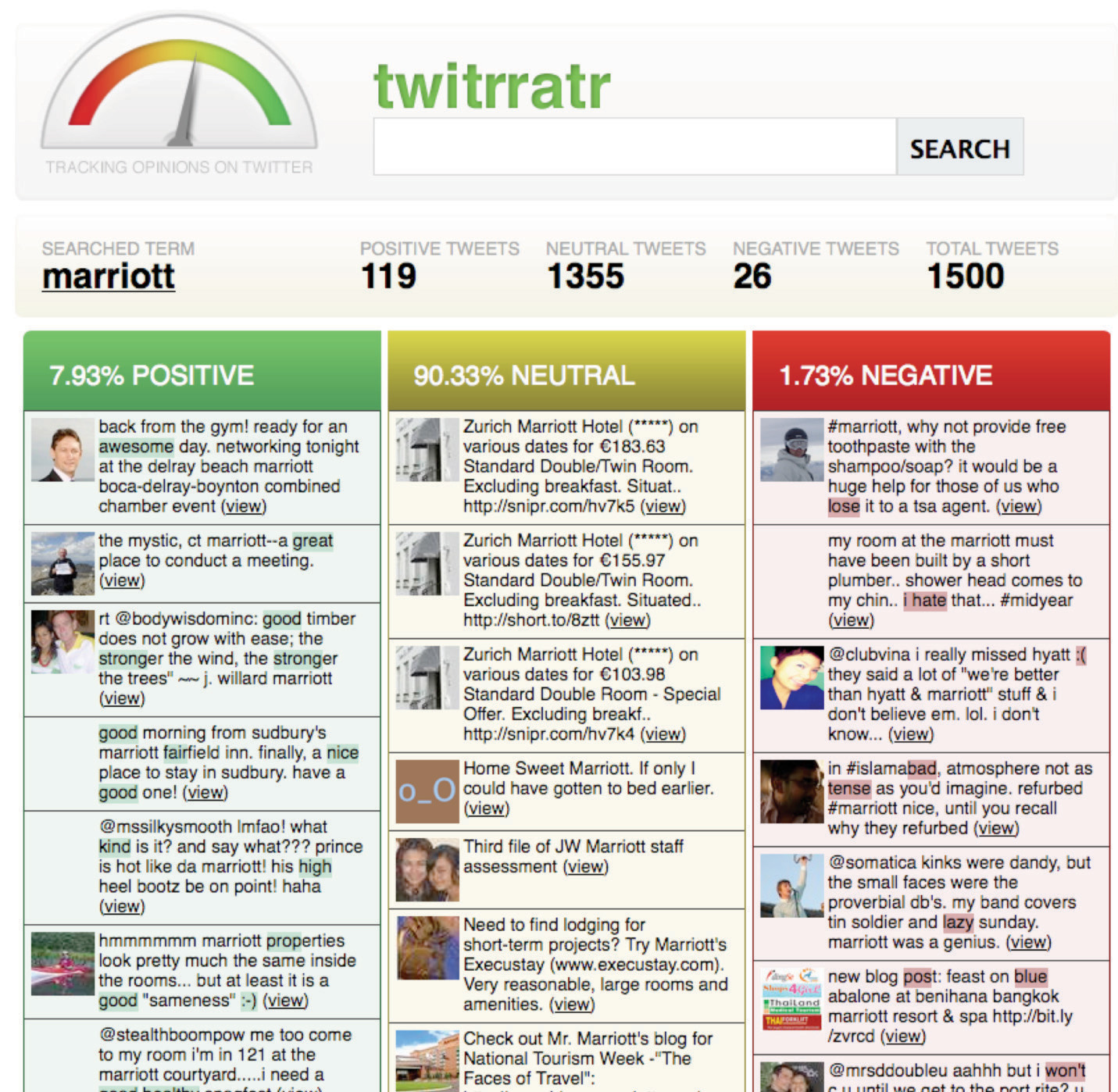
Tools like Twitrratr attempt to classify the sentiment behind tweets mentioning a key word or phrase. Savvy firms can mine comments for opportunities to provide thoughtful customer service (like the suggestion at the top right to provide toothpaste for those who lose it in U.S. airport security).
Facebook provides a summary of fan page activity to administrators (including stats on visits, new fans, wall posts, etc.), while Facebook’s Insights tool measures user exposure, actions, and response behavior relating to a firm’s Facebook pages and ads.
Bit.ly and many other URL-shortening services allow firms to track Twitter references to a particular page. Since bit.ly applies the same shortened URL to all tweets pointing to a page, it allows firms to follow not only if a campaign has been spread through “retweeting” but also if new tweets were generated outside of a campaign. Graphs plot click-throughs over time, and a list of original tweets can be pulled up to examine what commentary accompanied a particular link.
Location-based services like Foursquare have also rolled out robust tools for monitoring how customers engage with firms in the brick-and-mortar world. Foursquare’s analytics and dashboard present firms with a variety of statistics, such as who has “checked in” and when, a venue’s male-to-female ratio, and which times of day are more active for certain customers. “Business owners will also be able to offer instant promotions to try to engage new customers and keep current ones.”N. Bolton, “Foursquare Introduces New Tools for Businesses,” March 9, 2010. Managers can use the tools to notice if a once-loyal patron has dropped off the map, potentially creating a special promotion to lure her back.
Monitoring should also not be limited to customers and competitors. Firms are leveraging social media both inside their firms and via external services (e.g., corporate groups on Facebook and LinkedIn), and these spaces should also be on the SMART radar. This kind of monitoring can help firms keep pace with employee sentiment and insights, flag discussions that may involve proprietary information or other inappropriate topics, and provide guidance for those who want to leverage social media for the firm’s staff—that is, anything from using online tools to help organize the firm’s softball league to creating a wiki for a project group. Social media are end-user services that are particularly easy to deploy but that can also be used disastrously and inappropriately, so it’s vital for IT experts and other staffers on the social media team to be visible and available, offering support and resources for those who want to take a dip into social media’s waters.
Establishing a Presence
Firms hoping to get in on the online conversation should make it easy for their customers to find them. Many firms take an embassyIn the context of social media, an established online presence where customers can reach and interact with the firm. An effective embassy approach uses a consistent firm name in all its social media properties. approach to social media, establishing presence at various services with a consistent name. Think facebook.com/starbucks, twitter.com/starbucks, youtube.com/starbucks, flickr.com/starbucks, and so on. Corporate e-mail and Web sites can include icons linking to these services in a header or footer. The firm’s social media embassies can also be highlighted in physical space such as in print, on bags and packaging, and on store signage. Firms should try to ensure that all embassies carry consistent design elements, so users see familiar visual cues that underscore they are now at a destination associated with the organization.
As mentioned earlier, some firms establish their own communities for customer engagement. Examples include Dell’s IdeaStorm and MyStarbucksIdea. Not every firm has a customer base that is large and engaged enough to support hosting its own community. But for larger firms, these communities can create a nexus for feedback, customer-driven innovation, and engagement.
Customers expect an open dialogue, so firms engaging online should be prepared to deal with feedback that’s not all positive. Firms are entirely within their right to screen out offensive and inappropriate comments. Noting this, firms might think twice before turning on YouTube comments (described as “the gutter of the Internet” by one leading social media manager).Brad Nelson, presentation at the Social Media Conference NW, Mount Vernon, WA, March 25, 2010. Such comments could expose employees or customers profiled in clips to withering, snarky ridicule. However, firms engaged in curating their forums to present only positive messages should be prepared for the community to rebel and for embarrassing cries of censorship to be disclosed. Firms that believe in the integrity of their work and the substance of their message shouldn’t be afraid. While a big brand like Starbucks is often a target of criticism, social media also provides organizations with an opportunity to respond fairly to that criticism and post video and photos of the firm’s efforts. In Starbucks’ case, the firm shares its work investing in poor coffee-growing communities as well as efforts to support AIDS relief. A social media presence allows a firm to share these works without waiting for conventional public relations (PR) to yield results or for journalists to pick up and interpret the firm’s story. Starbucks executives have described the majority of comments the company receives through social media as “a love letter to the firm.” By contrast, if your firm isn’t prepared to be open or if your products and services are notoriously subpar and your firm is inattentive to customer feedback, then establishing a brand-tarring social media beachhead might not make sense. A word to the self-reflective: Customer conversations will happen online even if you don’t have any social media embassies. Users can form their own groups, hash tags, and forums. A reluctance to participate may signal that the firm is facing deeper issues around its product and service.
While firms can learn a lot from social media consultants and tool providers, it’s considered bad practice to outsource the management of a social media presence to a third-party agency. The voice of the firm should come from the firm. In fact, it should come from employees who can provide authentic expertise. Starbucks’ primary Twitter feed is managed by Brad Nelson, a former barista, while the firm’s director of environmental affairs, Jim Hanna, tweets and engages across social media channels on the firm’s green efforts.
Engage and Respond
Having an effective social media presence offers “four Ms” of engagement: it’s a megaphone allowing for outbound communication; it’s a magnet drawing communities inward for conversation; and it allows for monitoring and mediation of existing conversations.J. Gallaugher and S. Ransbotham, “Social Media and Dialog Management at Starbucks” (presented at the MISQE Social Media Workshop, Phoenix, AZ, December 2009). This dialogue can happen privately (private messaging is supported on most services) or can occur very publicly (with the intention to reach a wide audience). Understanding when, where, and how to engage and respond online requires a deft and experienced hand.
Many firms will selectively and occasionally retweet praise posts, underscoring the firm’s commitment to customer service. Highlighting service heroes also reinforces exemplar behavior to employees who may be following the firm online, too. Users are often delighted when a major brand retweets their comments, posts a comment on their blog, or otherwise acknowledges them online—just be sure to do a quick public profile investigation to make sure your shout-outs are directed at customers you want associated with your firm. Escalation procedures should also include methods to flag noteworthy posts, good ideas, and opportunities that the social media team should be paying attention to. The customer base is often filled with heartwarming stories of positive customer experiences and rich with insight on making good things even better.
Many will also offer an unsolicited apology if the firm’s name or products comes up in a disgruntled post. You may not be able to respond to all online complaints, but selective acknowledgement of the customer’s voice (and attempts to address any emergent trends) is a sign of a firm that’s focused on customer care. Getting the frequency, tone, and cadence for this kind of dialogue is more art than science, and managers are advised to regularly monitor other firms with similar characteristics for examples of what works and what doesn’t.
Many incidents can be responded to immediately and with clear rules of engagement. For example, Starbuck issues corrective replies to the often-tweeted urban legend that the firm does not send coffee to the U.S. military because of a corporate position against the war. A typical response might read, “Not true, get the facts here” with a link to a Web page that sets the record straight.
Reaching out to key influencers can also be extremely valuable. Prominent bloggers and other respected social media participants can provide keen guidance and insight. The goal isn’t to create a mouthpiece, but to solicit input, gain advice, gauge reaction, and be sure your message is properly interpreted. Influencers can also help spread accurate information and demonstrate a firm’s commitment to listening and learning. In the wake of the Domino’s gross-out, executives reached out to the prominent blog The Consumerist.A. Jacques, “Domino’s Delivers during Crisis: The Company’s Step-by-Step Response after a Vulgar Video Goes Viral,” The Public Relations Strategist, October 24, 2009. Facebook has solicited advice and feedback from MoveOn.org months before launching new features.B. Stone, “Facebook Aims to Extend Its Reach across the Web,” New York Times, December 2, 2008. Meanwhile, Kaiser Permanente leveraged advice from well-known health care bloggers in crafting its approach to social media.J. Kane, R. Fichman, J. Gallaugher, and J. Glaser, “Community Relations 2.0,” Harvard Business Review, November 2009.
However, it’s also important to recognize that not every mention is worthy of a response. The Internet is filled with PR seekers, the unsatisfiably disgruntled, axe grinders seeking to trap firms, dishonest competitors, and inappropriate groups of mischief makers commonly referred to as trolls. One such group hijacked Time Magazine’s user poll of the World’s Most Influential People, voting their twenty-one-year-old leader to the top of the list ahead of Barack Obama, Vladimir Putin, and the pope. Prank voting was so finely calibrated among the group that the rankings list was engineered to spell out a vulgar term using the first letter of each nominee’s name.E. Schonfeld, “Time Magazine Throws Up Its Hands As It Gets Pawned by 4Chan,” TechCrunch, April 27, 2009.
To prepare, firms should “war game” possible crises, ensuring that everyone knows their role, and that experts are on call. A firm’s social media policy should also make it clear how employees who spot a crisis might “pull the alarm” and mobilize the crisis response team. Having all employees aware of how to respond gives the firm an expanded institutional radar that can lower the chances of being blindsided. This can be especially important as many conversations take place in the so-called dark Web beyond the reach of conventional search engines and monitoring tools (e.g., within membership communities or sites, such as Facebook, where only “friends” have access).
In the event of an incident, silence can be deadly. Consumers expect a response to major events, even if it’s just “we’re listening, we’re aware, and we intend to fix things.” When director Kevin Smith was asked to leave a Southwest Airline flight because he was too large for a single seat, Smith went ballistic on Twitter, berating Southwest’s service to his thousands of online followers. Southwest responded that same evening via Twitter, posting, “I’ve read the tweets all night from @ThatKevinSmith—He’ll be getting a call at home from our Customer Relations VP tonight.”
In the event of a major crisis, firms can leverage online media outside the social sphere. In the days following the Domino’s incident, the gross-out video consistently appeared near the top of Google searches about the firm. When appropriate, companies can buy ads to run alongside keywords explaining their position and, if appropriate, offering an apology.S. Gregory, “Domino’s YouTube Crisis: 5 Ways to Fight Back,” Time, April 18, 2009. Homeopathic cold remedy Zicam countered blog posts citing inaccurate product information by running Google ads adjacent to these links, containing tag lines such as “Zicam: Get the Facts.”Zicam had regularly been the victim of urban legends claiming negative side effects from use; see Snopes.com, “Zicam Warning,” http://www.snopes.com/medical/drugs/zicam.asp. However, the firm subsequently was cited in an unrelated FDA warning on the usage of its product; see S. Young, “FDA Warns against Using 3 Popular Zicam Cold Meds,” CNN.com, June 16, 2009.
Review sites such as Yelp and TripAdvisor also provide opportunities for firms to respond to negative reviews. This can send a message that a firm recognizes missteps and is making an attempt to address the issue (follow-through is critical, or expect an even harsher backlash). Sometimes a private response is most effective. When a customer of Farmstead Cheeses and Wines in the San Francisco Bay area posted a Yelp complaint that a cashier was rude, the firm’s owner sent a private reply to the poster pointing out that the employee in question was actually hard of hearing. The complaint was subsequently withdrawn and the critic eventually joined the firm’s Wine Club.K. Paterson, “Managing an Online Reputation,” New York Times, July 29, 2009. Private responses may be most appropriate if a firm is reimbursing clients or dealing with issues where public dialogue doesn’t help the situation. One doesn’t want to train members of the community that public griping gets reward. For similar reasons, in some cases store credit rather than reimbursement may be appropriate compensation.
Who Should Speak for Your Firm? The Case of the Cisco Fatty
Using the Twitter handle “TheConnor,” a graduating college student recently offered full-time employment by the highly regarded networking giant Cisco posted this tweet: “Cisco just offered me a job! Now I have to weigh the utility of a fatty paycheck against the daily commute to San Jose and hating the work.” Bad idea. Her tweet was public and a Cisco employee saw the post, responding, “Who is the hiring manager. I’m sure they would love to know that you will hate the work. We here at Cisco are versed in the web.” Snap!
But this is also where the story underscores the subtleties of social media engagement. Cisco employees are right to be stung by this kind of criticism. The firm regularly ranks at the top of Fortune’s list of “Best Firms to Work for in America.” Many Cisco employees take great pride in their work, and all have an interest in maintaining the firm’s rep so that the company can hire the best and brightest and continue to compete at the top of its market. But when an employee went after a college student so publicly, the incident escalated. The media picked up on the post, and it began to look like an old guy picking on a clueless young woman who made a stupid mistake that should have been addressed in private. There was also an online pile-on attacking TheConnor. Someone uncovered the woman’s true identity and posted hurtful and disparaging messages about her. Someone else set up a Web site at CiscoFatty.com. Even Oprah got involved, asking both parties to appear on her show (the offer was declined). A clearer social media policy highlighting the kinds of issues to respond to and offering a reporting hierarchy to catch and escalate such incidents might have headed off the embarrassment and helped both Cisco and TheConnor resolve the issue with a little less public attention.H. Popkin, “Twitter Gets You Fired in 140 Characters or Less,” MSNBC, March 23, 2009.
It’s time to take social media seriously. We’re now deep into a revolution that has rewritten the rules of customer-firm communication. There are emerging technologies and skills to acquire, a shifting landscape of laws and expectations, a minefield of dangers, and a wealth of unexploited opportunities. Organizations that professionalize their approach to social media and other Web 2.0 technologies are ready to exploit the upside—potentially stronger brands, increased sales, sharper customer service, improved innovation, and more. Those that ignore the new landscape risk catastrophe and perhaps even irrelevance.
Key Takeaways
- Customer conversations are happening and employees are using social media. Even firms that aren’t planning on creating a social media presence need to professionalize the social media function in their firm (consider this a social media awareness and response team, or SMART).
- Social media is an interdisciplinary practice, and the team should include professionals experienced in technology, marketing, PR, customer service, legal, and human resources.
- While the social media team provides guidance, training, and oversight, and structures crisis response, it’s important to ensure that authentic experts engage on behalf of the firm. Social media is a conversation, and this isn’t a job for the standard PR-style corporate spokesperson.
- Social media policies revolve around “three Rs”: representation, responsibility, and respect. Many firms have posted their policies online so it can be easy for a firm to assemble examples of best practice.
- Firms must train employees and update their knowledge as technologies, effective use, and threats emerge. Security training is a vital component of establishing social media policy. Penalties for violation should be clear and backed by enforcement.
- While tempting, creating sock puppets to astroturf social media with praise posts violates FTC rules and can result in prosecution. Many users who thought their efforts were anonymous have been embarrassingly exposed and penalized. Customers are also using social media to expose firm dishonesty.
- Many tools exist for monitoring social media mentions of an organization, brands, competitors, and executives. Google Alerts, Twitter search, TweetDeck, Twitrratr, bit.ly, Facebook, and Foursquare all provide free tools that firms can leverage. For-fee tools and services are available as part of the online reputation management industry (and consultants in this space can also provide advice on improving a firm’s online image and engagement).
- Social media are easy to adopt and potentially easy to abuse. The social media team can provide monitoring and support for firm-focused efforts inside the company and running on third-party networks, both to improve efforts and prevent unwanted disclosure, compliance, and privacy violations.
- The embassy approach to social media has firms establish their online presence through consistently named areas within popular services (e.g., facebook.com/starbucks, twitter.com/starbucks, youtube.com/starbucks). Firms can also create their own branded social media sites using tools such as Salesforce.com’s “Ideas” platform.
- Social media provides “four Ms” of engagement: the megaphone to send out messages from the firm, the magnet to attract inbound communication, and monitoring and mediation—paying attention to what’s happening online and selectively engage conversations when appropriate. Engagement can be public or private.
- Engagement is often more art than science, and managers can learn a lot by paying attention to the experiences of others. Firms should have clear rules for engagement and escalation when positive or negative issues are worthy of attention.
Questions and Exercises
- The “United Breaks Guitars” and “Domino’s Gross Out” incidents are powerful reminders of how customers and employees can embarrass a firm. Find other examples of customer-and-employee social media incidents that reflected negatively on an organization. What happened? What was the result? How might these incidents have been prevented or better dealt with?
- Hunt for examples of social media excellence. List an example of an organization that got it right. What happened, and what benefits were received?
- Social media critics often lament a lack of ROI (return on investment) for these sorts of efforts. What kind of return should firms expect from social media? Does the return justify the investment? Why or why not?
- What kinds of firms should aggressively pursue social media? Which ones might consider avoiding these practices? If a firm is concerned about online conversations, what might this also tell management?
- List the skills that are needed by today’s social media professionals. What topics should you study to prepare you for a career in this space?
- Search online to find examples of corporate social media policies. Share your findings with your instructor. What points do these policies have in common? Are there aspects of any of these policies that you think are especially strong that other firms might adopt? Are there things in these policies that concern you?
- Should firms monitor employee social media use? Should they block external social media sites at work? Why or why not? Why might the answer differ by industry?
- Use the monitoring tools mentioned in the reading to search your own name. How would a prospective employer evaluate what they’ve found? How should you curate your online profiles and social media presence to be the most “corporate friendly”?
- Investigate incidents where employees were fired for social media use. Prepare to discuss examples in class. Could the employer have avoided these incidents?
- Use the monitoring tools mentioned in the reading to search for a favorite firm or brand. What trends do you discover? Is the online dialogue fair? How might the firm use these findings?
- Consider the case of the Cisco Fatty. Who was wrong? Advise how a firm might best handle this kind of online commentary.




